
Last month we were invited to do a half-day workshop on setting up a computer security incident response team at TWNIC’s event. I was putting together the slides with some examples of incidents that network operators get when a friend forwarded me this phishy-looking text message. She also said that at least three friends in the phone address book had received the same message from her.
Perfect timing for a fresh example for my incident response class! Let’s have a look at the message first:
Puan Najwa , anda sudah dapat courier service document, sila tandatangan atas electronik certification hxxp://goo.gl/dGraHH
That message is actually in Bahasa Malaysia and English (Manglish?) and can be loosely translated as the following:
Mrs Najwa, you have received a courier service document, please sign on the electronic certification.
It probably does not make any sense to most people, but as with many social engineering attacks, the objective of the attacker is to get people to click on the link in the message. I must also mention that the name of the receiver of the message will also appear in the text. Finally if you look at the URL, it has been obfuscated using a ‘URL shortener’ service (in this case goo.gl) to perhaps hide the actual location or file that is going to be downloaded and installed.
In the workshop, I mentioned that one of the goals of incident response is to mitigate the potential damage of an incident. In this case, it means to make sure that those who received similar message above will not be able to download and install whatever that link is serving.
bash-3.2$ wget hxxp://goo.gl/dGraHH
–2014-06-03 23:14:32– hxxp://goo.gl/dGraHH
Resolving goo.gl… 74.125.204.102, 74.125.204.100, 74.125.204.101, …
Connecting to goo.gl|74.125.204.102|:80… connected.
HTTP request sent, awaiting response… 301 Moved Permanently
Location: hxxps://www.dropbox.com/s/2spbfs86wsj2l8l/sijil.apk?m= [following]
–2014-06-03 23:14:32– hxxps://www.dropbox.com/s/2spbfs86wsj2l8l/sijil.apk
Using wget on my linux terminal instead of actually trying to visit the link using a browser directly (and risk getting my work computer infected!). You can see clearly that the short URL is actually pointing to an *.apk (or Android Package File). If you are keen to learn more Bahasa make a mental note now that the word sijil the Bahasa word for certificate 🙂
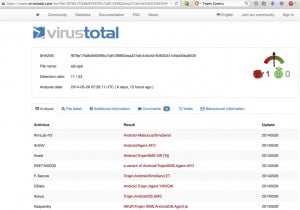
An incident response analyst at this stage will probably start asking, is this file malicious? Using freely available malware scanning service provided by the good folks at VirusTotal.com I was able to conclude that sijil.apk is up to no good.
What is interesting to see in the report when I first saw it was that someone had submitted the file a few days earlier.
Since this potentially malicious is hosted on Dropbox.com, we need to notify their abuse team about this so that they can do the necessary (i.e. remove it!). Fortunately, through a security operations mailing-list, I managed to reach out to someone at Dropbox who told me that requests for removing malicious files can be sent to abuse@dropbox.com. I was not able to tell exactly when the file was removed, but for sure it was no longer downloadable when I checked a few hours later. Kudos to the responsive abuse team at Dropbox! (Of course the miscreants behind this could just modify their message and host the file elsewhere)
Now let us see what this apk will do if it gets installed on an Android device. Once again, there are a few (free) services that you can use to do this. To cut a long story short check out the following URLs and try to figure out the domain name (or IP address) that is being ‘contacted’ by Sijil.apk. See also what are the other activities captured by the by the static & dynamic analysis performed on the file.
https://anubis.iseclab.org/?action=result&task_id=176b14a0ad15fe254a1bd807ae87bd976
http://apkscan.nviso.be/report/show/7e46ab220b1feb0ba1e608b5485219c2
When you look at the analysis reports above, you will probably have more questions such as how many people actually installed Sijil.apk or who is behind this (and for what reason) . And this is where issues like cross-border cooperation, roles and responsibilities (network operators, service providers, certs/csirts, law enforcement agencies) , intel-sharing begin to emerge. They can be complicated but I don’t intend to cover them in this post.
More on that in future blog posts!
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.

Seems you found the same malware which we found. But the file name is different.
Thanks for sharing. 🙂