
Pulse-wave Distributed Denial-of-Service (DDoS) attacks have recently managed to take down critical network infrastructure causing enormous financial and reputational damage. In contrast to conventional DDoS attacks, which grow steadily and persist longer in time, pulse-wave DDoS attacks are composed of short-duration, high-rate traffic pulses (Figure 1).
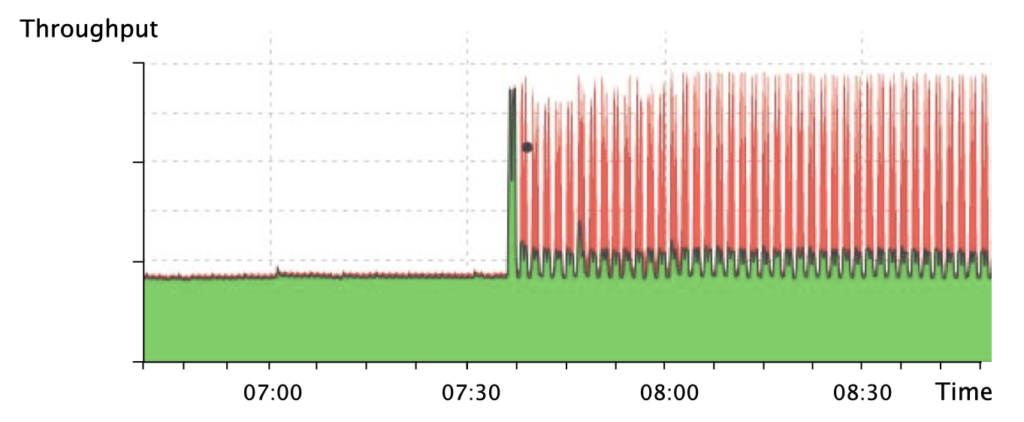
Each pulse can leverage a different attack vector (for example, NTP, DNS, Memcached) and can reach hundreds of Gigabits per second (Gbps).
Pulse-wave DDoS attacks target the limitations of existing defences
Pulse-wave DDoS attacks exploit four specific limitations of existing DDoS defences that:
- Cover a narrow set of attack vectors. For most of them, network operators have to manually pre-configure the limited set of attack patterns to be detected, as well as their mitigation rules (for example, signature-based defences and access-control lists). Other defences (for example, heavy-hitter detectors) support more abstract attack patterns but are still limited in the granularity they provide, for example, they only work at the per-flow level. Pulse-wave DDoS attacks exploit this limitation by morphing their vectors across the different attack pulses, to maximize their chances of success.
- Have slow reaction times. Most of them rely on hybrid architectures, composed of an in-network defence, responsible for detecting attacks, and an external facility, in charge of deciding how to mitigate them. The time that it takes for the in-network defence to reach the external facility and mitigate the attack is in the order of seconds to minutes. Under a pulse-wave DDoS attack, by the time the defence has managed to mitigate one of the attack pulses, another pulse kicks in, forcing the mitigation process to be restarted.
- Rely on drastic mitigation techniques such as re-routing or filtering, which strongly degrade performance in case of misclassification (for example, filtering-based defences may drop a flash crowd of benign traffic if it is misclassified). By leveraging multiple attack vectors, pulse-wave DDoS attacks increase the probability of misclassification and worsen the implications of these mitigation techniques. For example, in the event of a pulse-wave DDoS attack, a network with routing-based defences may experience route-flapping behaviours.
- Rely on threshold-based activation mechanisms, which, for example, identify an attack when a given counter exceeds a certain value. These triggering mechanisms have the risk of misconfiguration as they are hard to configure and can negatively impact performance if not optimally configured. Indeed, a too-broad threshold may result in attack traffic being missed, and a too-narrow threshold may produce false positives.
As such, if we were to build an ideal pulse-wave DDoS defence today, we would like it to be:
- Generic, to cover a broad range of attack vectors at different granularity.
- Fast, to mitigate every different attack pulse.
- Safe, to prevent damaging benign traffic in case of misclassification.
- Fully automated, to eliminate the risk of misconfiguration.
ACC-Turbo mitigates pulse-wave DDoS attacks at line rate
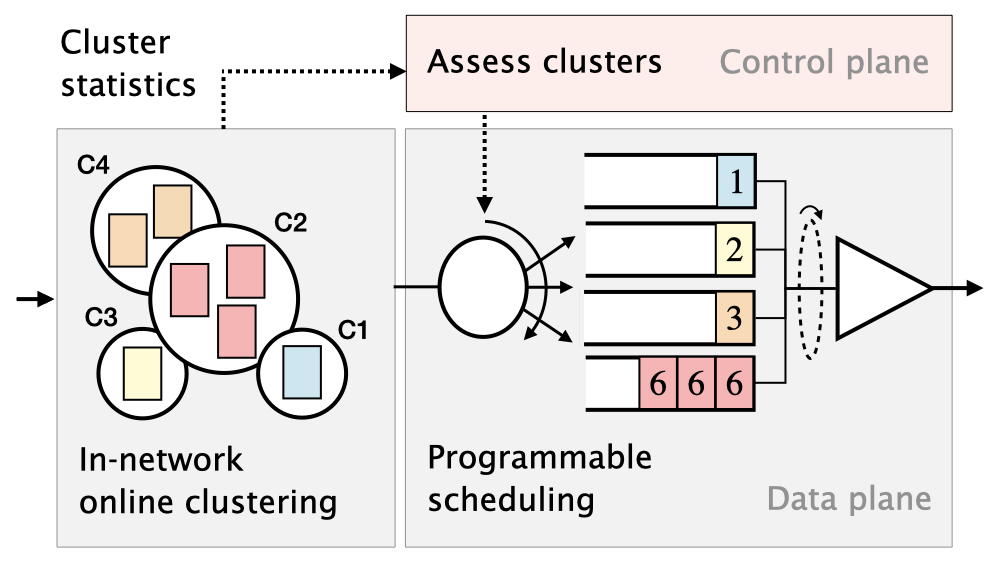
ACC-Turbo is a pulse-wave DDoS defence that runs at line rate, on programmable switches, and satisfies the four design requirements. The critical insight behind ACC-Turbo is based on two key techniques: Unsupervised inference — to effectively identify (possibly unknown) attack pulses — and programmable packet scheduling — to safely deprioritize malicious traffic, instead of just dropping it.
First, ACC-Turbo leverages packet clustering to infer high-bandwidth traffic aggregates that are responsible for a high amount of congestion in the network (and potentially responsible for the attack). By working at the aggregate level, ACC-Turbo manages to be generic and cover a broad range of attacks at flexible granularity. Further, ACC-Turbo runs the inference process directly in the data plane, to achieve a fast reaction time. It does so by leveraging in-network online packet clustering. As a result, ACC-Turbo manages to mitigate attacks in under a second.
Second, ACC-Turbo uses programmable packet scheduling to deprioritize traffic aggregates that seem most malicious. By deprioritizing attack traffic (instead of just dropping it), ACC-Turbo manages to be safe in mitigating attacks. Indeed, packet scheduling only leads to hard drops under congestion, being transparent otherwise. Since ACC-Turbo runs in the data plane (which does not impact traffic latency) and relies on scheduling (which is transparent under no attack), it can be left ‘always-on’, constantly running on all traffic. This makes ACC-Turbo fully automated, eliminating the need for an activation mechanism and its consequent risk of misconfiguration.
Learn more
Read our paper or watch our presentation (video, slides) at SIGCOMM 2022 to learn more about ACC-Turbo. The source code is also available on GitHub.
ACC-Turbo is one of the results of a joint research project between the Networked Systems Group at ETH Zürich and armasuisse. The goal of the research project is to investigate how network programmability can be used to automate the security of computer networks.
Albert Gran Alcoz is a PhD student at ETH Zürich in the Networked Systems Group.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.
