
Remotely Triggered Black Hole (RTBH) is a popular approach that has been used for the last two decades to mitigate Distributed Denial-of-Service (DDoS) attacks by Autonomous Systems (ASes).
The Unwanted Traffic Removal Service (UTRS), developed and deployed by Team Cymru about 10 years ago, offers a global, free and easy-to-join and operate RTBH implementation. Considering this exceptional value proposition and almost a decade of operation, we explore how this service is used nowadays to mitigate DDoS attacks.
Methodology
In order to achieve our goal, my fellow researchers and I from the Delft University of Technology, Yokohama National University, and Japan’s National Institute of Information and Communications Technology collected three datasets for six months (October 2022 – April 2023):
- UTRS. This dataset contains information about the UTRS announcements to mitigate DDoS attacks by the UTRS members. To collect this dataset, we registered our own AS and joined the UTRS project. Thus, we were able to gather data about the under-attack target networks, sent by the UTRS members.
- AmpPot. The dataset contains request data collected from a network of globally distributed amplification honeypots deployed by Yokohama National University.
- Internet-of-Things (IoT) Milker. This dataset contains information about IoT-botnet-driven DDoS attacks. To collect this dataset, we deployed a Command and Control (C&C) monitoring system to oversee DDoS attack commands sent to IoT bots.
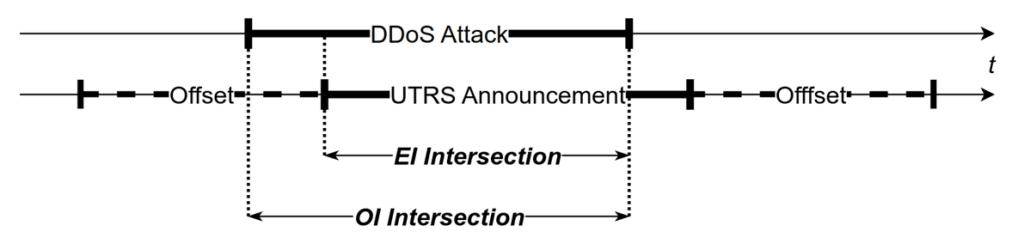
By correlating these datasets, in particular UTRS-AmpPot and UTRS-Milker, in time and IP space, we gathered the insights answering the proposed research questions. So as attacks and corresponding UTRS announcements are not aligned in time, we computed two views representing the intersections with the UTRS dataset data. The first view (Exact Interval (EI)) contains data about exact time interval intersections between DDoS attacks and UTRS announcements, while the second (Offset Interval (OI)) represents the intersections of DDoS attack intervals with the UTRS announcement span extended by 12 hours in both directions (see Figure 1 for details).
Findings
Table 1 describes the collected datasets used in this study. The second column (# entries) presents the total number of observations in each dataset aggregated for the whole period of observation. The third column (# targets) shows the number of target networks in the case of UTRS and Milker datasets, while for AmpPot, it displays the number of targeted individual IPs. The fourth column (# unique IPs) shows the number of targeted unique IPs.
| Dataset | # entries | # targets | # unique IPs |
| UTRS | 533,257 | 7,820 | 7,830 |
| AmpPot | 1,616,184 | 1,080,770 | 1,080,770 |
| Milker | 223,267 | 46,764 | 2,787,522 |
UTRS dataset
Table 1 shows that there are 7,820 unique target networks from 124 ASes that contain 7,830 individual IP addresses in the UTRS dataset. The UTRS webpage reports that there are more than 1,300 UTRS members, while the Regional Internet Registries Statistics website reveals that there are 115,000 ASes globally. Analysing this data, we can make several conclusions.
First, only about 1% of all ASes are UTRS members, which is disappointing given its value proposition. This service is subject to the network effect, meaning its usefulness will only be perceived if a substantial portion of all ASes join the initiative.
Second, only about 10% of all participating ASes actively use UTRS to mitigate DDoS attacks. We assume that given the low portion of participants, the effects of the announcements are not that significant. This conclusion is also confirmed by the low usage of the service; on average, there are only 3,122 announcements per day, aimed at 357 target networks.
Third, the majority of UTRS announcements targeted individual IP addresses (/32); only two entries in the dataset targeted the same /27 subnetwork within the same day. This shows that participating ASes prefer to use the UTRS very selectively, probably as a last resort (although they can announce up to /25 networks), because all the traffic to the target should be ideally blocked after the announcement. This also explains why a large portion of the announcements (21%) are short-lived, less than 5 minutes long. The introduction of the BGP Flowspec type of announcement in UTRS 2.0 may address this issue.
Dataset intersections
Table 2 provides the details about the intersections of the UTRS-AmpPot and UTRS-Milker datasets. As we can see, the number of intersections is quite small.
| Parameter | UA-EI | UA-OI | UM-EI | UM-OI |
| # of entries | 468 | 6,774 | 9 | 791 |
| # of unique DDoS attack targets | 249 | 1,268 | 2 | 143 |
| # of unique UTRS targets | 249 | 1,268 | 8 | 163 |
| # of unique UTRS ASNs | 25 | 43 | 2 | 6 |
There are only 43 ASes in total for which an intersection is found: 11 ASes are from Brazil, 9 from the USA, and 7 from Argentina. The results of the correlation also show that quite a low percent of DDoS attacks on the UTRS members trigger mitigation: 1.03% of AmpPot and 0.06% of Milker for EI; 8.86% of AmpPot and 6.88% of Milker for OI. At the same time, globally, this percentage is even smaller: 0.025% of AmpPot and 0.001% of Milker for EI; 0.212% of AmpPot and 0.147% of Milker for OI.
Conclusions
DDoS attacks continue to remain a significant threat to the Internet. UTRS offers a free, global, and easy-to-join and use RTBH alternative to mitigate this threat. Unfortunately, as our analysis shows, despite a unique value proposition and after almost 10 years of operation, it still has not become widely adopted.
More details about this work can be found in our scientific peer-reviewed paper ‘Peering into the Darkness: The Use of UTRS in Combating DDoS Attacks‘ presented at ESORICS 2023.
Yury Zhauniarovich (website, LinkedIn) is an Assistant Professor at the Technology, Policy and Management (TPM) faculty at TU Delft. He is interested in a broad range of topics related to cybersecurity, network measurements and data analytics.
Radu Anghel, Swaathi Vetrivel, Elsa Turcios Rodriguez, Kaichi Sameshima, Daisuke Makita, Katsunari Yoshioka, and Carlos Gañán contributed to this work.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.

Team cymru is at least disputable in Reputation.
https://www.vice.com/en/article/dy3z9a/fbi-bought-netflow-data-team-cymru-contract
which is unfortunate as such a BGP feed is great.
maybe https://www.cloudflare.com/en-gb/lp/botnet-threat-feed/
might be an alternative someday