
RIPE NCC has taken the decision to withdraw from their RPKI Validator project. It won’t shut down instantly, but the RIPE NCC Validator will stop receiving maintenance as of July 2021.
The good news is they have given us all plenty of lead time to explore some other options. Which raises the question: What are my other options?
Fear not, there are plenty.
Other RPKI Validator systems
A useful catalogue of alternative validator choices is being maintained by NLNet Labs, which is reproduced below. Take a moment to think about the programming language you are using, and which validator would be the most appropriate for you to use.
| Name | Maintainer | Language | Last Commit |
|---|---|---|---|
| FORT Validator | NIC.mx | C | January 2021 |
| OctoRPKI | Cloudflare | Go | December 2020 |
| rcynic | Dragon Research Labs | Python | December 2018 |
| Routinator | NLnet Labs | Rust | February 2021 |
| rpki-client | OpenBSD | C | February 2021 |
| rpki-prover | Misha Puzanov | Haskell | February 2021 |
| RPKI Validator | RIPE NCC | Java | February 2021 |
| RPSTIR2 | ZDNS | Go | December 2020 |
Table 1 — Alternative validator options from a collection maintained by NLNet Labs.
If you check this listing, you will see that at least two of them include a Graphical User Interface (GUI) option: Routinator and RPStir2 (aka RPKIVIZ). The APNIC blog also has guides on how to install some of these validators (Routinator, OctoRPKI and FORT).
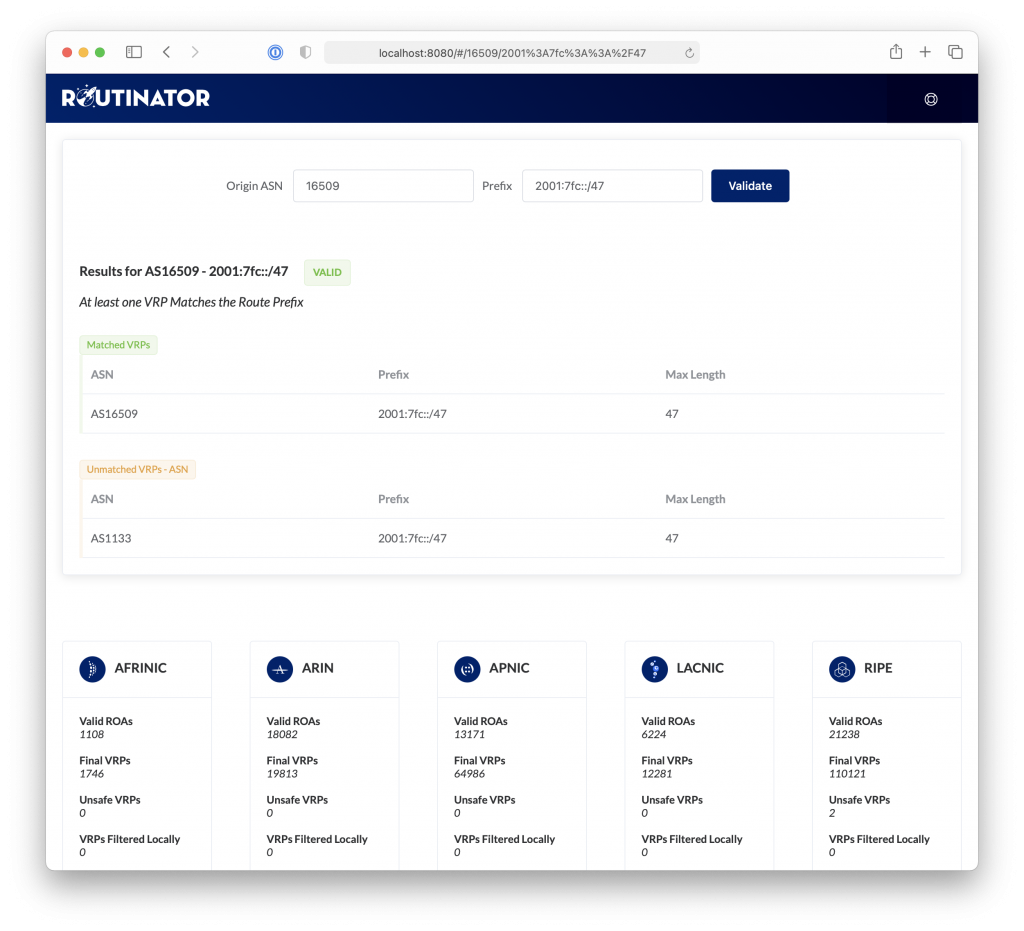
Routinator
Routinator connects to the trust anchors of the five Regional Internet Registries (RIRs), downloading their certificates and Route Origin Authorization (ROA) information, and verifying their signatures. It has a built in RTR server that allows it to send information directly to servers that support Route Origin Validation (ROV). A user interface is available via a built in HTTP server.
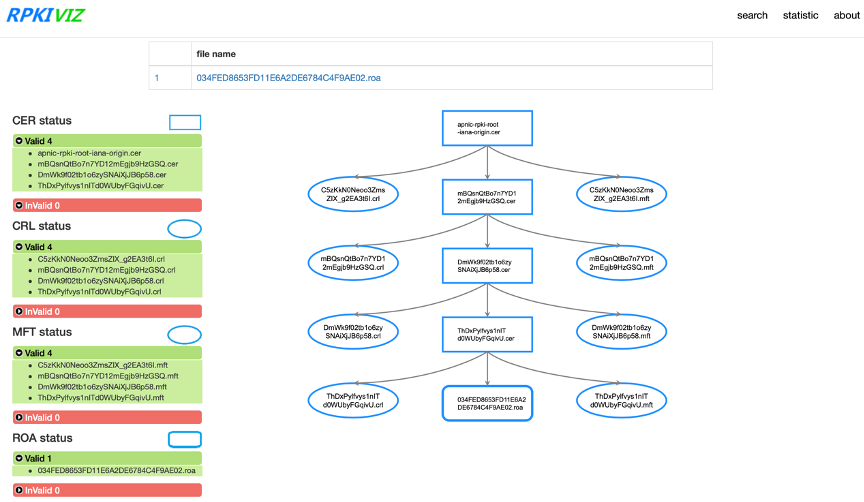
RPKIVIZ
We’ve written about RPKIVIZ in the past; it’s a graphical display based on the DNSVIZ model, helping debug chain validation issues, be they CRL, malformed parent certificate, or some other types of bugs. RPKIVIZ uses a tree structure to display the content and correlations of RPKI objects, such as Route Origin Attestations (ROAs), manifests, and certificate/CRL.
OctoRPKI
Cloudflare’s RPKI Validator requires a bootstrap file in order to fetch the RPKI data. The Trust Anchor Locators (TALs) for most RIRs ship with this, but ARIN requires users to agree to a Relying Party Agreement (RPA) in order to download the TAL. All five TALs are needed for validation.
OctoRPKI periodically refreshes the data provided by the RIRs and the delegated organizations. It keeps exploring the RPKI repositories until it reaches a stable state.
FORT Validator
The FORT Validator is part of the LACNIC/NIC.MX routing security project FORT. This open source tool allows operators to validate BGP routing information against the RPKI repository.
FORT Validator supports RTR version 0 (RFC 6810) and version 1 (RFC 8210). It depends on the router RTR implementation to determine which version it should use.
RPKI Prover
RPKI Prover is written in Haskell, making it an attractive choice for those most familiar with this language. At present there is no GUI, but the developer has indicated there are plans for a UI in future.
RPKI client
This validator was designed for OpenBSD but has since been ported to other systems. It may work on other systems, but it is regularly tested on the following:
- OpenBSD-current
- Alpine 3.12
- Debian 9, 10
- Fedora 31, 32, 33
- RHEL/CentOS 7, 8
Rcynic / DRL RPKI toolkit / ISC RPKI toolkit
The Rcynic Validator has gone by a variety of names, such as the DRL RPKI toolkit and ISC RPKI toolkit. It has had fewer updates in recent years than some of the other validator offerings.
About the RIPE RPKI Validator
The RIPE NCC Validator will continue to be maintained until July 2021. It is a system developed initially in Scala and then redeveloped in Java, with three core components:
- An implementation of the Resource Public Key Infrastructure (RPKI) ‘relying party’ (RP) function, which checks the cryptographic integrity of the RPKI products fetched from the worldwide repository system
- An implementation of the RPKI-RTR service, which ‘feeds’ the BGP with signals of validity for a given origin-AS and prefix (this is what actually provides the Route Origin Validation (ROV) service in the BGP)
- A GUI showing both the states of the repository systems (in their validity or completeness) and of the application of the RPKI Route Origin Authorizations (ROAs) to live BGP
The first two are requirements to run ROV, but the third has an additional benefit: it gives people a chance to see and understand the state of the global BGP against the published declarations of the ROA-active community. If you are a ROA producer, this tool can help you gain confidence about your ROAs and what it actually does.
Do your own validity checks to secure the BGP
I’ve written before on the risks and problems with using externally-sourced information to secure the BGP so I won’t rehash the problems here. The key point is that if you are concerned with your own RPKI state, there are times it can be helpful to look at it from ‘somewhere else’, to see what they see.
This is similar to the ‘Down for everyone or just me?‘ website — you know your own system’s lookup, but can anyone else see it?
In this narrow sense, having a publicly visible validation state can be useful, and there is nothing inherently wrong with using one. APNIC is very likely to consider offering this service in the web, to help Members and others to understand RPKI validity states and the BGP.
But please, for your own safety and security, don’t use this to configure your BGP via RPKI-RTR. Validity cannot be externally sourced – it has to be calculated by every BGP speaker for themselves.
That’s what the cryptography requires in order to do its job.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.
