The Worldwide Infrastructure Security Report (WISR) offers direct insights from network, security, and operations professionals including service provider, cloud and enterprise organizations. The report topics, from DDoS attacks to key organizational issues such as incident response training, focuses on cyber threats, risks, and strategies to address them.
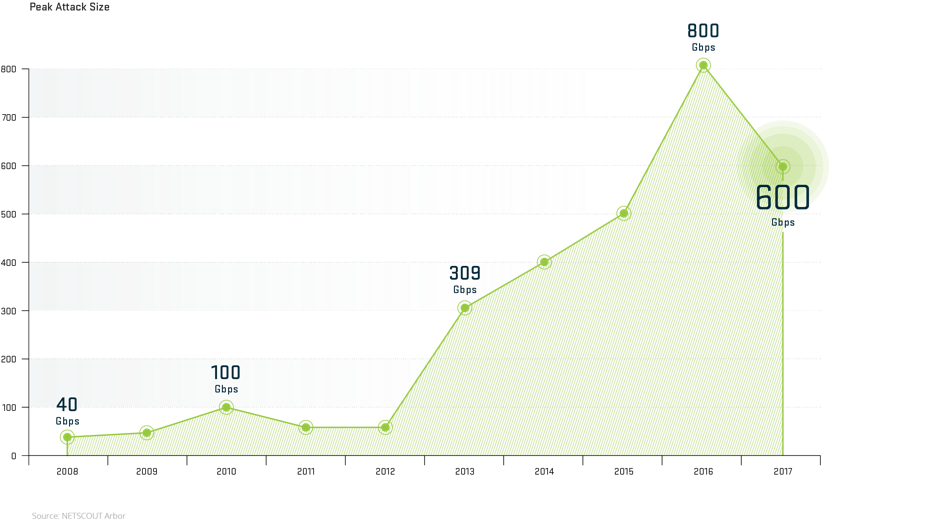
The general trend about the DDoS threat is that it becomes bigger in size, happens more frequently, and grows in complexity. However, in 2017, the largest attack reported in the WISR report was 600 Gbps, which represents a decrease from 800 Gbps in 2016.
Figure 1: Peak DDoS attack size from 2008 to 2017 (Arbor).
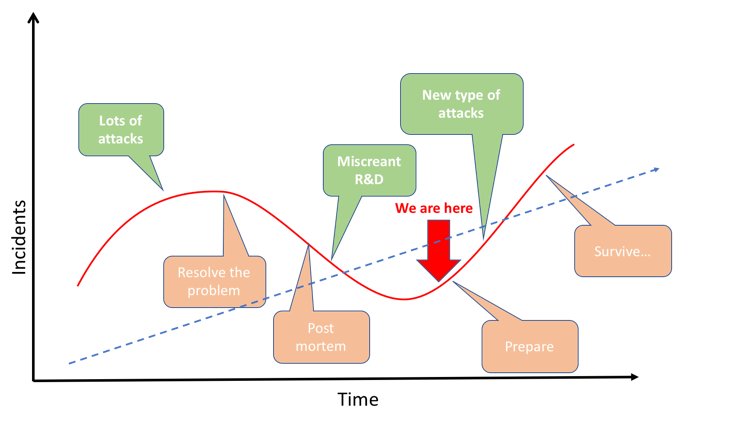
What we have also observed is that the attackers are innovative and persistent, and there is usually a pattern of the attack’s behaviour that looks like the following diagram:
Figure 2: Pattern of attacks over time (Arbor).
Although the largest DDoS attack seen in 2017 seems to decrease in size, the general belief is that the attack size will be growing as attackers develop new attack mechanisms and strategies.
Remarks: At the time of writing, there have been reports about attacks over Terabit per second being observed already.
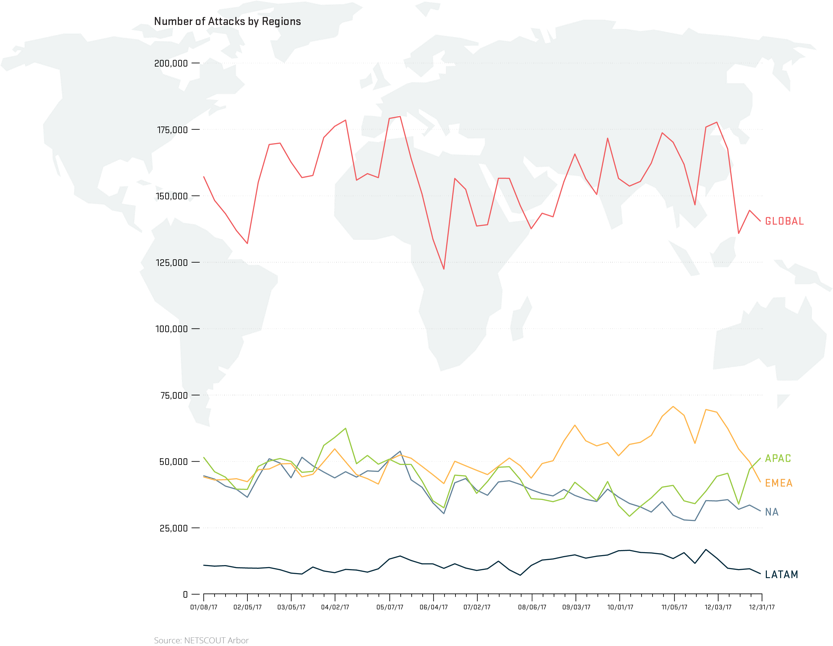
The Arbor Networks ATLAS system, which collects DDoS attack statistics from the Arbor Networks SP system deployed around the globe, provides a breakdown in terms of the number of DDoS events seen in four different geographical regions. The number of DDoS events observed in Europe and the Asia Pacific is higher than the other regions.
Figure 3: Number of DDoS events globally and as seen in four different geographical regions (Arbor).
DDoS attack vectors
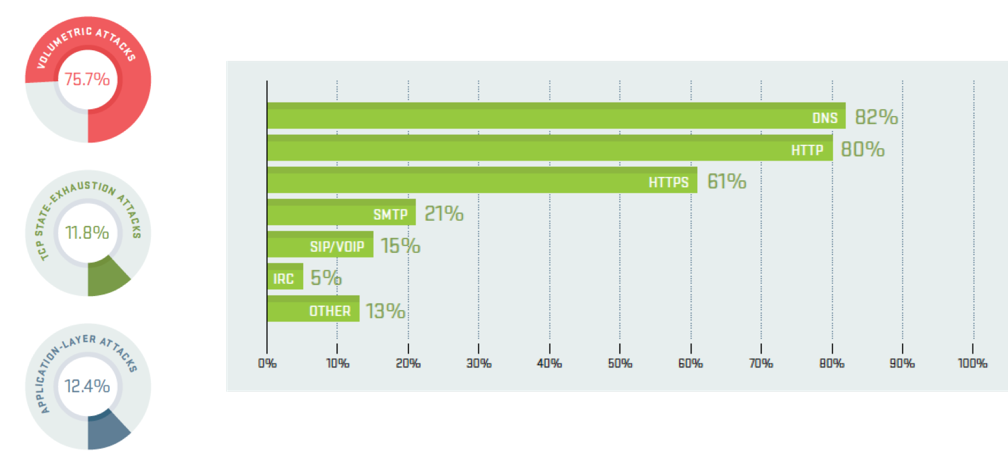
Looking at the mix of attack types experienced by service providers, volumetric attacks remain the most common, as in all previous iterations of the WISR reports.
Like the previous two years, 2017 saw a significant increase in the frequency of volumetric attacks around the world. The percentage of attacks that were volumetric in nature increased to approximately 76% in 2017, up from 73% in 2016. This is not surprising, given the widely reported prevalence of reflection/amplification and IoT-based attacks.
While for application-layer attacks, this type of attack continued to exploit many vulnerable services, the DNS was the most common service targeted by application-layer attacks, and was reported by 82% of service providers. HTTP remained at 80%, identical to 2016. Additionally, the number seeing attacks targeting secure web services (HTTPS) rose significantly from 52% to 61%.
Figure 4: Volumetric attacks were the most common form of attacks (top left graph), followed by TCP State-Exhaustion attacks and Application-Layer attacks. The DNS was the top target of attacks (bar graph), followed by HTTP and HTTPS (Arbor).
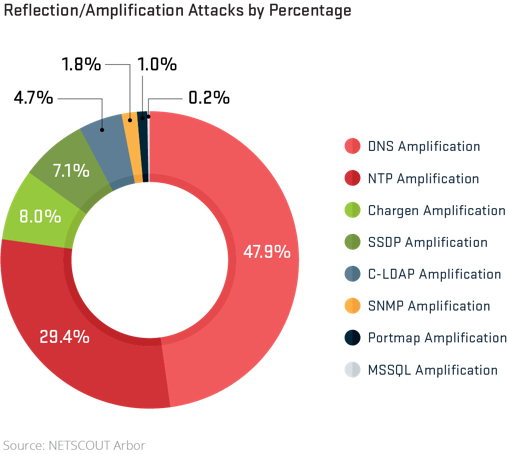
Speaking of reflection/amplification attacks, we observed a resurgence of the DNS as the dominant protocol used for reflection/amplification attacks. The DNS continued to be the most common reflection/amplification attack vector. In fact, the number of DNS reflection/amplification attacks is greater than all the other attack vectors combined. The number of DNS attacks is nearly double the number of NTP reflection/amplification attacks, which came in second.
Attackers always look for new exploits and in 2017 we observed massive growth in the use of C-LDAP for reflection/amplification attacks during the second half of the year.
Remarks: In February 2018, reflection/amplification attacks abusing the memcached protocol have been widely observed.
Read: Understanding the facts of memcached amplification attacks
Figure 5: DNS Amplification attacks were the most common form of attacks in 2017, followed by NTP Amplification attacks (Arbor).
Threats and concerns
Looking at the data for 2017 we see a few clear trends. DDoS attacks continue to be a major challenge for all types of network operators. While other threats such as advanced persistent threats and malicious insider are top of mind, they actually are experienced less frequently. Service providers reported DDoS as being both the top experienced threat and concern for the coming year. Enterprises rated ransomware as the top threat but ranked DDoS a close second.
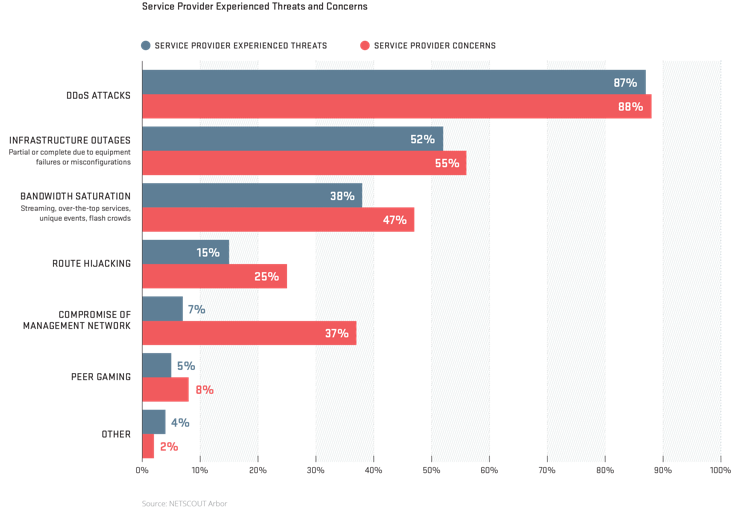
Figure 6: DDoS attacks continued to be a major challenge for all types of network operators in 2017 (Arbor).
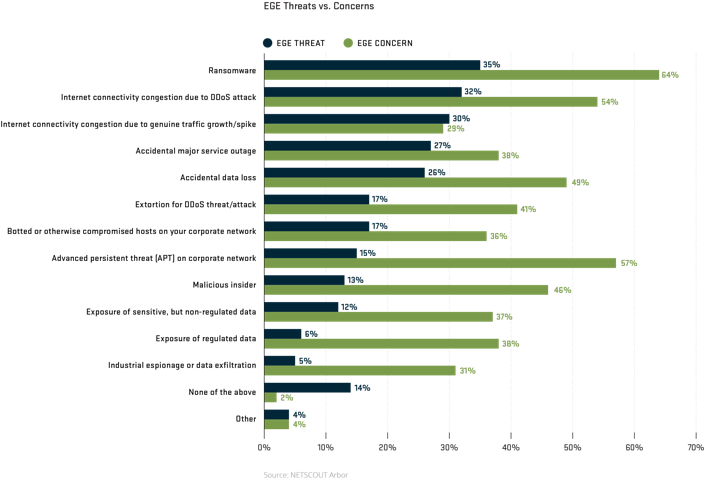
Figure 7: DDoS and APT attacks as well as accidental data loss are among the greatest concerns to enterprises, even though they are not of greatest threat (Arbor).
Although not as large, DDoS attacks will continue to be a threat
Now, more than ever, business and commerce simply cannot exist without robust Internet infrastructure that is continuously available. Even recreation and socialization depend on the Internet to deliver information and services.
As we have seen in the 2017 report, attackers continue to build and weaponize massive IoT botnets of unprecedented size and capability. Volumetric DDoS attacks have scaled back a bit in sheer size, but continue to increase in frequency.
We’ve seen increasing sophistication of IoT-based botnet attack capabilities. These modern botnets are capable of delivering attacks that include application-layer, volumetric and complex multi-vector DDoS attacks. Further, easy-to-use DDoS for hire services have helped make more sophisticated multi-vector DDoS attacks increasingly common.
Download the full report – https://www.arbornetworks.com/report/
CF Chui is a 20 + year veteran in designing, implementing, and supporting highly available network systems and solutions. In this current role with Arbor Networks, CF is involved in the global research projects as well as working closely with customers in the Asia Pacific to develop and optimize approaches for their network security.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.