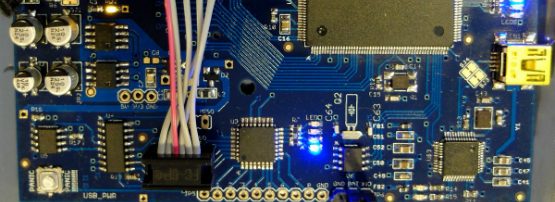
Last weekend, I had the joy of playing with a complete functional system at the IETF93 workshop in Prague, organized by CrypTech.
The system in question was a ‘novena’ development system with an ARM CPU and associated FPGA, programmed by the CrypTech project to provide cryptographic services.
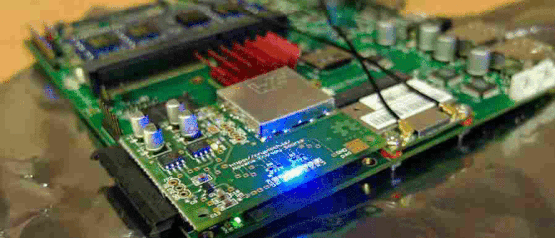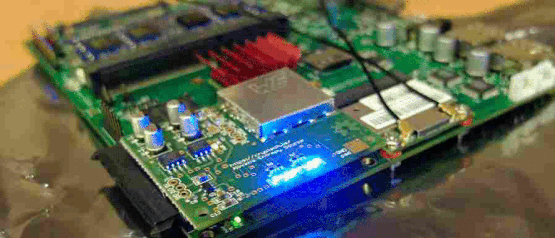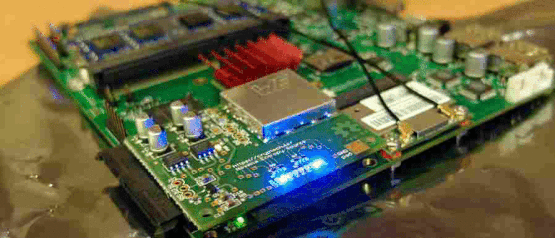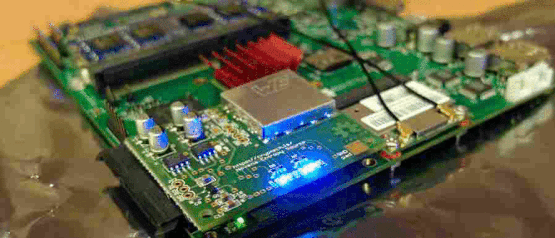
Das blinkenlicht
On top of this, a specially designed ‘noise board’ is used to feed strong random deterministic signals into a ‘noise mixer’. The mixer combines external data with internally generated data, from a ‘ring circuit’ in the FPGA which resonates chaotically, along with the pseudo-random output of a cryptographic function.
The noise board has been designed to use the GPIO pins as found on a Raspberry Pi, and is a functional ‘Pi-Hat’ board and can be used that way, or via USB, or attached to the CrypTech system directly.
The noise board uses commodity parts to make a ‘noisy diode‘, which is then encased in a radio frequency ‘cage’ to limit the leakage of signals into the noise source. Of note, the commodity parts are especially chosen so that a lot of different electronic part manufacturers can be used to source them, so there is less risk a single vendor can be compromised to change the system behaviour.

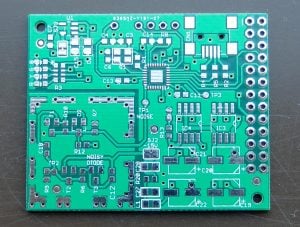
We were invited to think about examining the board for ourselves before sealing it, and shown the printed-circuit-board label which even carefully signposts the ‘noisy’ diode on the board.
At the workshop we were able to bootstrap the cryptographic services on this host and then configure it to use PKCS11 (the defined standard for communicating cryptographic services to a hard or soft provider of keying services). Finally, we got to configure OpenDNSSEC on a 32-bit virtual machine of our own, and use the system to perform DNSSEC zone signing.
We were also shown the ‘alpha’ board designs, which are going to be very close to the final board design. These boards include the first stages of tamperproof hardware, and use a simple ‘key wrap’ mechanism to ensure all the secrets held on the hardware longterm are themselves encrypted. They are protected by a special key held off the normal memory, in a small space on the circuit board, which can be fast-wiped at any time the tamper detection system triggers. If this single key is wiped, all the data on the rest of the system is lost. This is because without the key they cannot be recovered, after running memory has been lost.
The tamperproof system is provided in the alpha board with a ‘panic’ button (also carefully labelled on the circuit board’) which means you can choose to panic, or don’t panic as you see fit.


The experience of using a publicly defined, designed and built service like this is hugely rewarding. I felt confident in the skills in the room, and the mix of people from many backgrounds and economies, men and women who are committed to developing a higher sense of trust in the cryptographic frameworks we will depend on in the public Internet.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.

Wow! I want to help develop your open-source HSM. I have 20 years professional experience in software development (assembly, C, LISP) and FPGA circuit development (Xilinx, Verilog). Who may I contact?
Hi Peter – thanks for the offer of support. The people to contact are the group of engineers working on the project – you can find more information on their wiki site or the cryptech.is website:
https://cryptech.is/
http://wiki.cryptech.is/