When we at the Internet Society published the ccTLD study in 2021 to measure how much content is hosted inside or outside economies based on measures such as latency and hop-count, it was evident that Singapore is popular for hosting content of all varieties, especially within the Asia Pacific region. As noted in the study, 68% of Singapore’s ccTLD, .sg, was hosted inside the economy. Malaysia also appeared in the data as a popular location abroad for hosting ccTLD content.
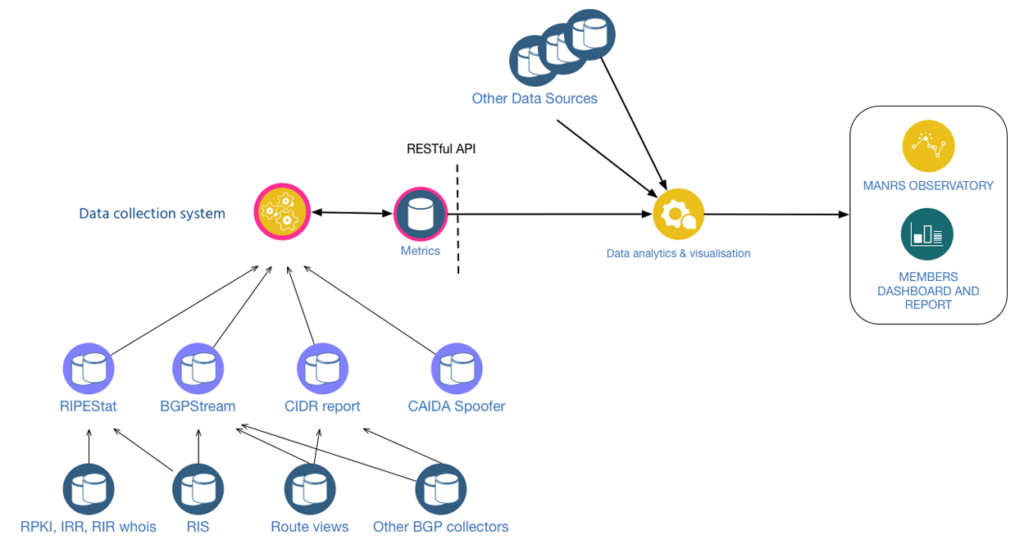
In this post, I will be examining the routing security of operators in Singapore (according to APNIC registration data) and how .sg ccTLD domains are performing from a Resource Public Key Infrastructure (RPKI) point of view. This routing security post is based on the MANRS Observatory, which collects data from multiple sources. While we try our level best to filter any false positives, it’s not possible to entirely avoid them.
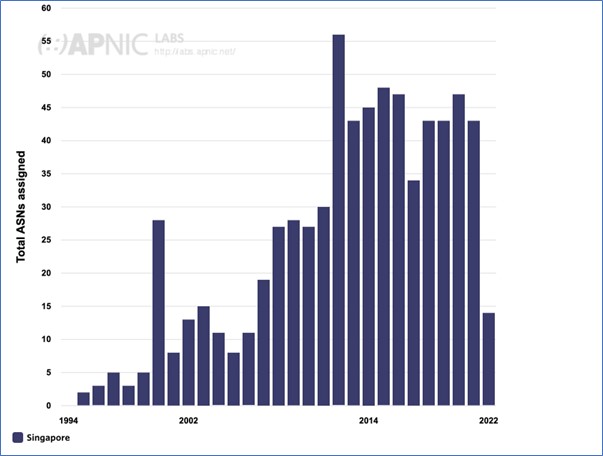
There are more than 1,000 networks in Singapore and according to APNIC delegation records, APNIC provides some good visual statistics of the per economy resource delegations through its REx tool.
The public view of the MANRS Observatory allows you to select an economy and view not only the current status of the operators in the economy but also the historical overview of the last 12 months. You can also see how the economy is performing compared to its neighbours or other economies.
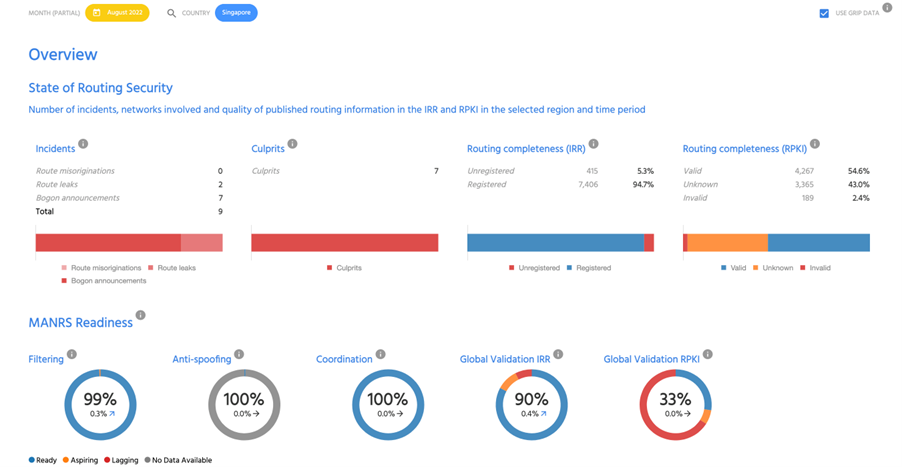
Looking at Singapore, it shows that in the month of August 2022 there were at least two incidents related to route leaks and seven incidents of bogon announcements. A bogon is an Internet number resource (Autonomous System Number (ASN), IPv4/IPv6 address) that should not be announced on the global routing table because either it is not allocated by the Internet Assigned Numbers Authority (IANA) and Regional Internet Registries (RIRs), or it is from the reserved blocks. All these incidents were caused by seven networks.
The most encouraging part is visible in the historical statistics, shown in Figure 4. While we can see incidents in almost every month of the last 12 months, fewer than 1% of networks have caused problems, and most of the incidents were related to bogon announcements.
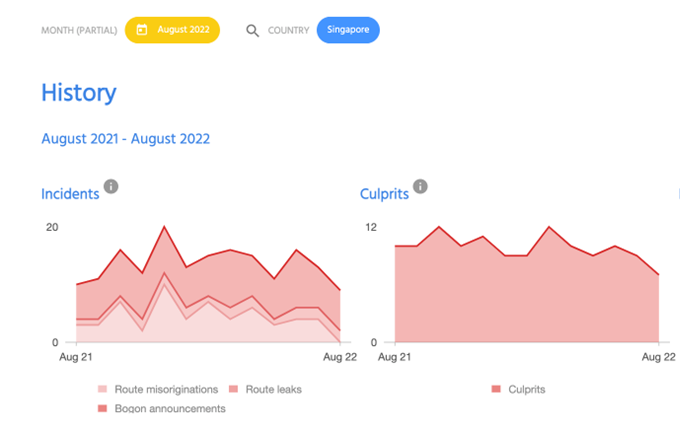
While the number of networks responsible for these incidents is low, we can’t say with certainty that most of the networks are implementing the baseline routing security required to avoid incidents.
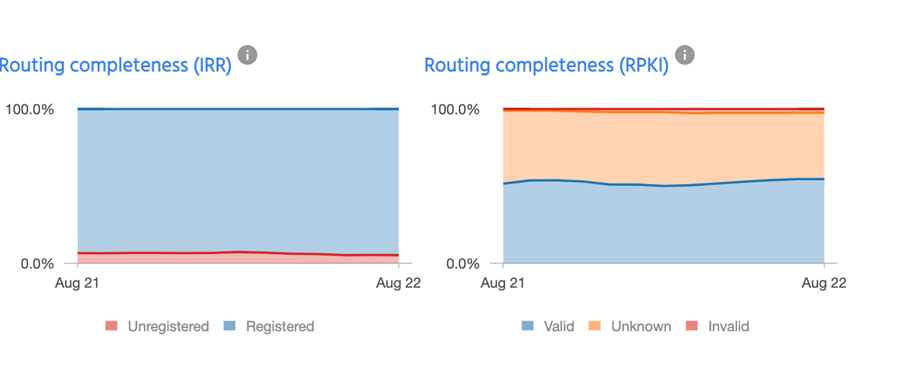
A Route Origin Authorization (ROA) is a cryptographically signed object that states an AS is authorized to originate a particular IP address prefix or set of prefixes. Singapore’s ROA adoption is almost 55%, which makes it higher than the global average of around 40%. However, the concerning part is the number of invalid ROAs, which is at 2.6% compared to the global average of 0.5%.
To see how government websites (ending in .gov.sg) are performing from the RPKI perspective, we looked at a sample and found most are hosted at Google or Amazon, which are both active at ROA signing, as shown in Figure 5.
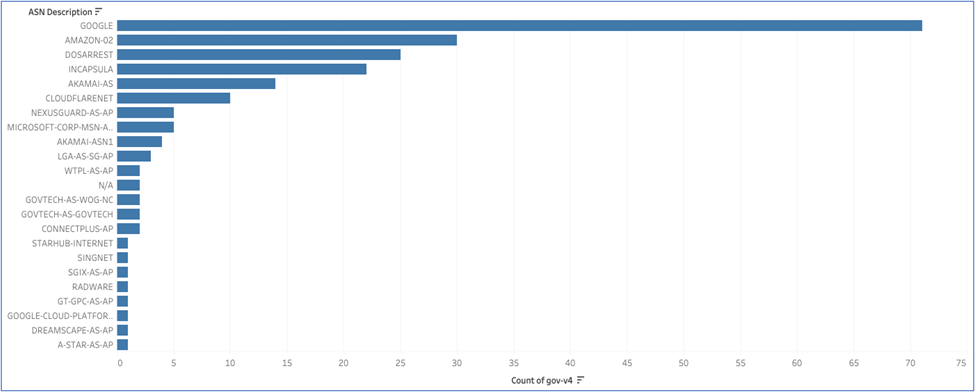
Out of that sample, we found most of the websites had valid ROAs of their IP host, but a substantial amount of ‘not found’.
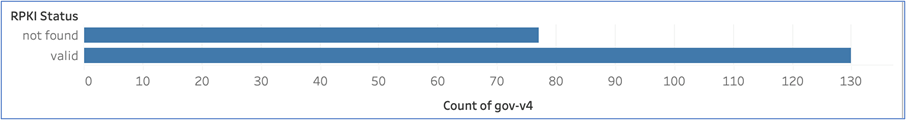
When we expand the data of ‘not found’ IP hosts to check which network these resources belong to, it’s a very different picture. There are many networks in the list as shown below — interestingly the top two are Akamai and Incapsula.
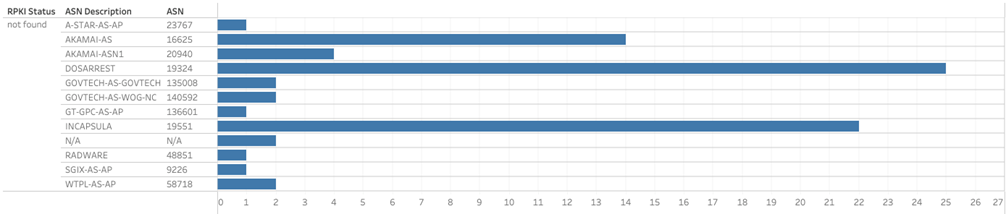
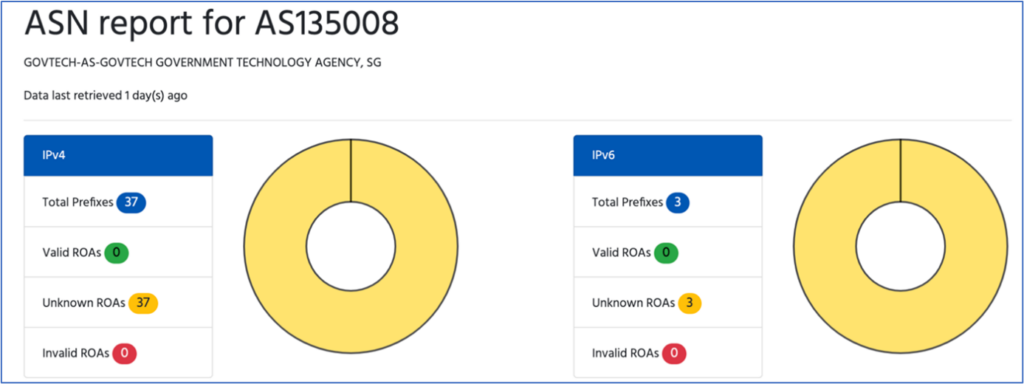
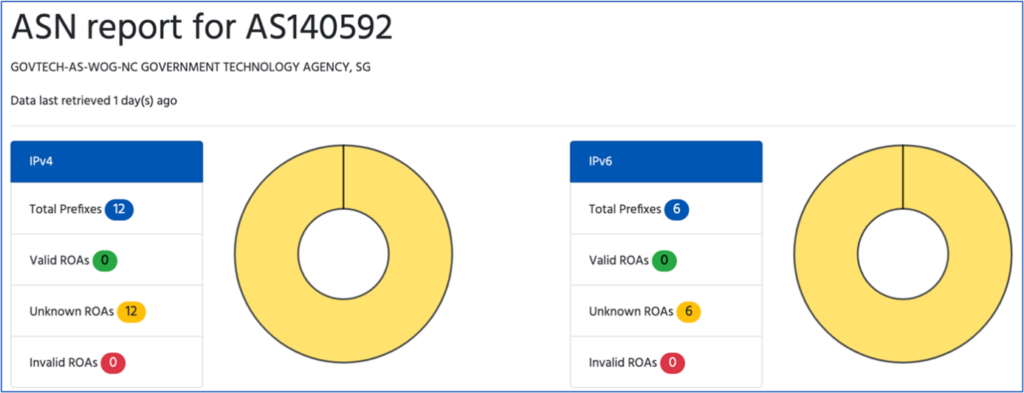
Unfortunately, two government-related networks, AS135008 and AS140592, have not signed any ROAs at all for their resources (Figures 8 and 9). AS135008 announces 37 IPv4 routes and three IPv6 routes while AS140952 announces 12 IPv4 routes and six IPv6 routes.
In the .edu.sg sample, we found most of the websites are hosted at Amazon and Incapsula.
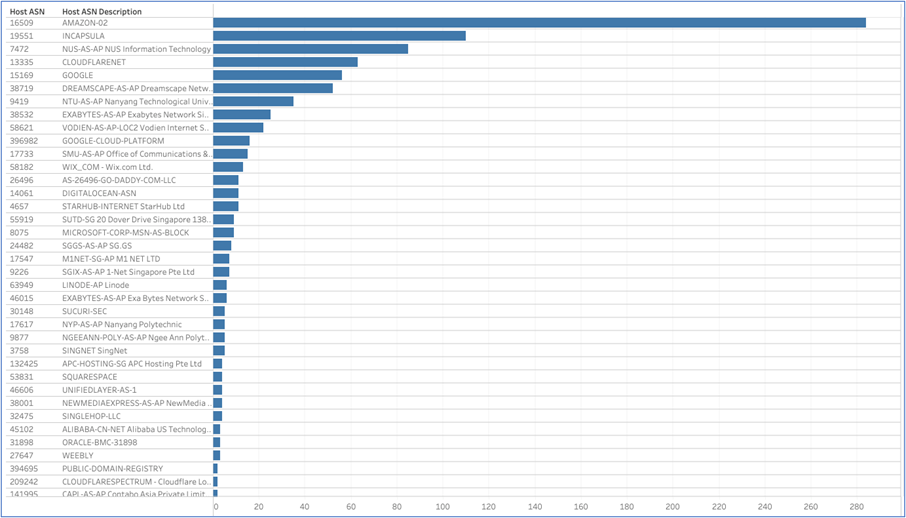
Once again, we found most had valid ROAs of their IP host.

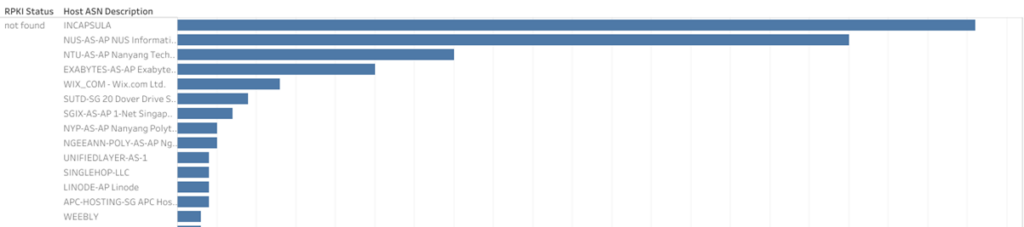
Looking at the not founds, we found most of the websites were hosted at Incapsula and the National University of Singapore (NUS).
Why is this important?
Having valid ROAs prevents your IP addresses from origin hijack attempts. As ROAs are digitally signed objects, they provide a means of verifying that an IP address block holder has authorized an AS to originate routes to the global routing table. Not having ROAs makes these prefixes vulnerable to origin hijacks.
We encourage everyone to host their websites with platforms that support RPKI and create ROAs for their resources. Most importantly, governments should emphasize security best practices.
Network operators have a responsibility to ensure a globally robust and secure routing infrastructure. Your network’s safety depends on a routing infrastructure that stops bad actors and mitigates accidental misconfigurations that can wreak havoc on the Internet. The more network operators work together, the fewer incidents there will be, and the less damage bad actors and misconfigurations can do.
Learn more about the importance of routing security, and implementation, at MANRS and how to create RPKI ROAs in MyAPNIC.
Aftab Siddiqui is a MANRS Project Lead & Senior Manager, Internet Technology at the Internet Society.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.