
By dropping invalid routes of its peers, Mongolian mobile operator, MobiCom (AS55805), is showing ISPs and networks around the world that size and age have little to do with making the global routing infrastructure more robust and secure.
Speaking at this week’s APNIC 50 conference, MobiCom IP Network Engineer, Ulsbold Enkhtaivan, explains how his company fully implemented Resource Public Key Infrastructure (RPKI) in May this year by performing Route Origin Validation (ROV).
RPKI is a public key infrastructure framework designed to secure the Internet’s routing infrastructure, specifically the Border Gateway Protocol (BGP), and protect against route hijacking and other attacks.
Read: Telstra AS1221 strengthens its BGP security with RPKI implementation
“I first heard about BGP hijacking and how RPKI can help mitigate against this during the APNIC Hackathon at APRICOT 2019 in Daejeon, South Korea. From there, I returned to Mongolia to check that we had correctly signed Route Origin Authorizations (ROAs) for all of our prefixes so that they would show as valid,” explains Ulsbold.
Over the next 12 months, Ulsbold and his team sought to learn more about RPKI, including participating in webinars and hands-on workshops at Mongolia’s inaugural Network Operators Group meeting (mnNOG 1) and the RPKI Deployathon at APRICOT 2020.
Read: Community comes together to make deploying RPKI easier
“The workshops were really helpful as we got to put theory into practice and understand the physical processes we needed to implement RPKI fully,” said Ulsbold.
“This included choosing and installing a validator — we chose Routinator 3000, which we run on an Unbuntu machine — and enabling RPKI to Router (RTR) sessions between our routers and our validator.”
Read: How to install an RPKI Validator
With regard to the second step, Ulsbold notes they were lucky that their router’s operating system was up to date and able to support RPKI, a lesson for others interested in taking the next step after signing their ROAs.
Other lessons that Ulsbold will touch on in his APNIC 50 presentation include the need to:
- Get support from management. In Ulsbold’s case, his manager (now director) joined him at the RPKI Deployment session at APRICOT 2020 from which he understood the importance of needing to implement it.
- Be aware that RPKI will break your black hole announcements if you implement Remotely Triggered Black Hole (RTBH) filtering in your network.
- Always send the validation state to your iBGP session; this is due to BGP always preferring valid routes.
- Install more than one validator for redundancy purposes, something that Ulsbold and his team are currently testing.
“From here, we monitored how many invalid prefixes we were routing (see table below) over seven days after which time we started dropping invalid routes on IPv4 and IPv6,” says Ulsbold.
| Types | Invalid IPv4 routes |
| Transit | 325 |
| IXP | 946 |
| Peers and customers | 0 |
Table 1 — The number of invalid IPv4 routes MobiCom was routing before implementing ROV on 31 May 2020.
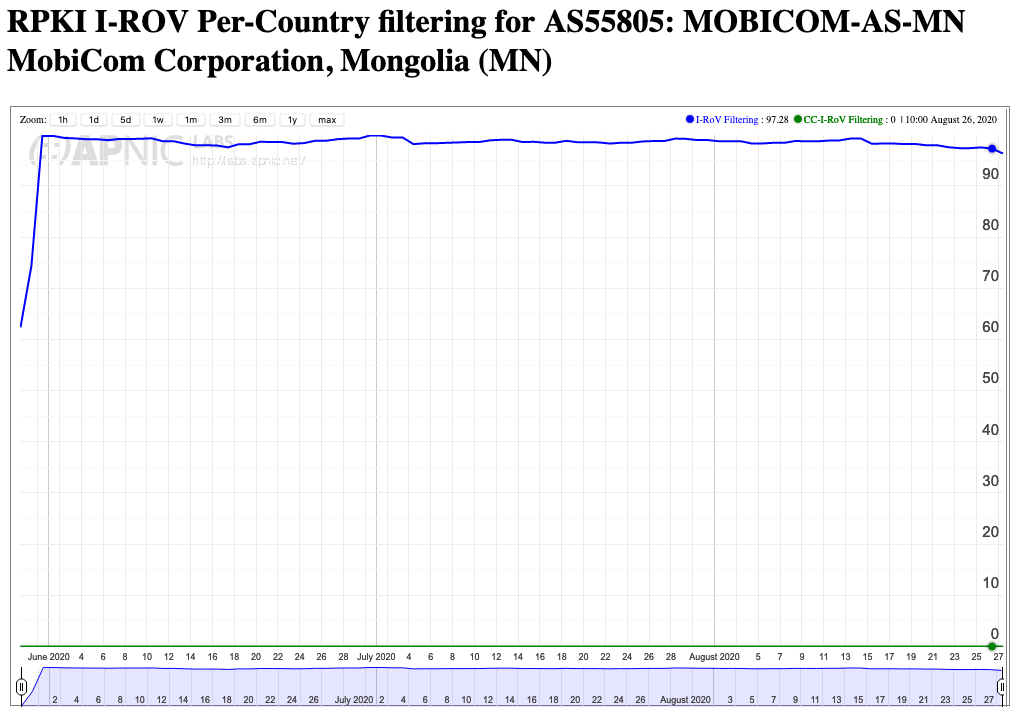
“For our upstream peers we allow all valid routes, and for our downstream peers we allow exact customer prefix and RTBH announcements then drop invalid ROAs. And we have not yet received one complaint from anyone about having their routes dropped!”
Ulsbold sees this as not just a major feather in MobiCom’s cap but also Mongolia’s, given its geographic importance as a key transit route between Asia and Europe.
“As a transit provider, we have a responsibility to implement RPKI to secure our customers from BGP hijacks. I expected that our company’s reputation will grow from this rather straightforward implementation both domestically and internationally as has been the case with other ISPs that have started to drop invalid routes.”
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.


