
The Maginot Line was a World War II-era series of fortifications, intended to protect France from a potential attack from the East.
The Line included concrete bunkers with mounted artillery guns, tunnels, railroad connections for supplies and to garrison French troops. However, despite its strength and elaborate design, the Maginot Line proved completely ineffective when German forces instead invaded Belgium to circumvent it. As such, the Maginot Line has come to mean ‘a defensive barrier or strategy that inspires a false sense of security’ and is often apparent in the world of cybersecurity.
Where is the cyber Maginot Line
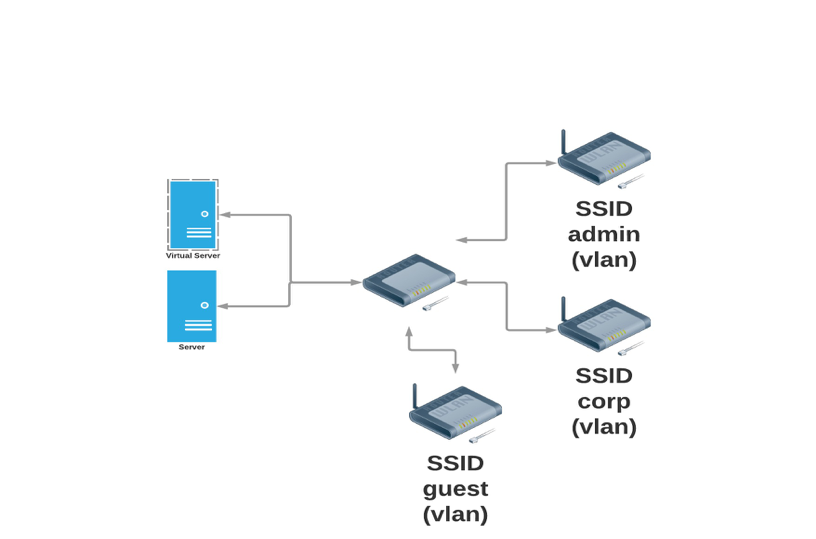
Recently we were tasked by a client to break into its internal network from its guest BYOD (Bring Your Own Device) network. The client had three different user groups (admin, corp and guest) isolated from each other and they used pfsense for all the routing and firewalling.
We were assigned to bypass the firewall and send a sample packet to any of the admin group machines or corp group machines. They never thought that instead of trying different packet filter bypass techniques we would directly attack the router itself.
Figure 1 — The client’s network had three isolated user groups (admin, corp and guest). We were tasked to breach the server via the guest network.
The pfsense router was left with default credential and it took just 10 minutes to take over the router, two routing tables to the router, and exploit one of the connected machines belonging to the admin network. Just like the Maginot Line, what looked like an impressive secured network was overtaken within a moment just because of one single misconfiguration associated with a scenario (bypass) they didn’t cater for.
In diagnosing how this happened, we identified opposing demands from within the organization: the business team asked the Dev teams to make everything as fast as possible so that it becomes operational; while the OPS team wanted it to run smoothly, which can’t be done without lots of debugging and testing of different elements to make it more efficient and smooth.
While conducting penetration testing, we had taken over 80% of the boxes exploiting different types of misconfiguration, which shows the number of risks related to the issue. Such scenarios are common, and more often than not, lead to misconfigurations and ultimately weaknesses in your network that can go unnoticed until they are exploited.
Shahee Mirza is the Head of Security Operations at Beetles Cyber Security Limited.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.

Good writing Shahee Vai
well done . nicely connected to history of security and explained. keep move forward like this more .
nice explanation brother with an effective story.
Such metaphor much wow, loved it
Proud of you Bhai. You are brilliant!!
Cyber security has been a big issue and this article was really helpful with the more nitty-gritty details.i have a website related to cyber-security check here for more information- https://mikeechols.com/