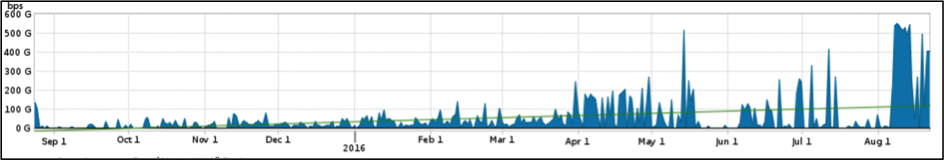
During the Rio Olympics, Distributed Denial of Service (DDoS) attacks reached a sustained value of 540Gbps of traffic.
Normally DDoS is a story of disruption and dismay as Internet services are unavailable for legitimate users. They can have a variety of implications for the victim, from simple nuisance through to significant brand damage, customer churn and even monetary loss for e-Commerce sites.
This story, however, is the opposite: it is a success story based on many months of preparation and effort that spanned multiple organizations, and in doing so, enabled them to successfully defend against some of the largest attacks seen to date.
Reason for the attacks
Leading up to and during the Olympics, there was a concerted campaign to disrupt the online properties of organizations affiliated with the Olympics. Many people in Brazil believed hosting the Olympics, after only having recently hosted the FIFA World Cup, was a waste of money that could have been better used to fund welfare, healthcare and education. Such reasons are among the multiple motivations for DDoS attacks, which range from political, religious, extortion, taking a competitor website offline or just malcontent.
A reason why DDoS is so popular among such campaigns is it is relatively easy to perform; a prospective attacker doesn’t need any coding skills or knowledge about protocols or applications. There are sites called ‘Booters’ and ‘Stressers’ that anyone can access, and for a relatively small amount of money these sites can be used to launch a variety of attacks from simple packet flooding, through to sophisticated application layer attacks.
In the months leading up to the Olympics, there were multiple DDoS attacks launched against various Internet properties. These attacks regularly reached 200+Gbps in size. The attackers used a number of methods, including DNS, SSDP and Chargen Reflection/Amplification, TCP Flooding as well as ICMP Floods and application layer attacks using Javascript and slow HTTP Posts.
UDP Reflection and Amplification attacks were directed towards UDP/80, UDP/443 and UDP/179. The later target (UDP/179) is of interest, as this may have been an attempt by attackers to disrupt the BGP routing within Brazil. Attackers may have simply assumed by sending UPD traffic to port 179 it would disrupt BGP, just like they assumed by sending UDP traffic to port 80 and 443 it would disrupt web servers.
Also of interest was the use of Generic Routing Encapsulation (GRE) as an attack vector. It is thought GRE was possibly used to circumvent poorly constructed ACLs or filters. This is because most people deploying ACLs or filters are usually focussed on TCP, UDP and ICMP, which make up only three of the 255 available protocol numbers (0 and 255 should not be used so that still leaves 1-254 as valid protocols that could be used for attacks). We expect to see more attacks use GRE as a result of this one.
Attacks used compromised IoT devices
Although the size of these coordinated attacks was massive, each of them was successfully detected and mitigated.
When the Olympics started, the attackers doubled-down on their efforts. They felt that causing disruption while the eyes of the world were focused on Rio de Janeiro would give their cause enormous visibility, and substantially embarrass the government and affiliate organizations.
Most of the attack effort used a botnet, which leveraged compromised Internet of Thing (IoT) devices. These included CCTV Cameras and home DSL routers that had been used for the 200+Gbps attacks over the months preceding the games. The sheer number of devices in the botnet enabled attackers to reach a staggering 540Gbps of sustained attack volume during the Olympics.
The IoT botnet was created by a group referred to as ‘Lizard Squad’ (which is described in more detail by Arbor Networks ASERT researcher Matt Bing), and leveraged default passwords and open Telnet services to install malware code that enabled remote control.
Unfortunately, many manufacturers continue to ship equipment that has many services like open DNS resolvers, Telnet and SSDP enabled by default. The equipment also does not require changing the default password as a matter of initial set up, so the number of potentially compromised devices available on the Internet is extremely large.
With any Internet-connected device, it is highly recommended to:
- change the default password to something that cannot be easily guessed or forced,
- disable any unnecessary services like Telnet and SSDP, and
- create appropriate ACLs or filters for services that are exposed to the Internet.
From attack to defence
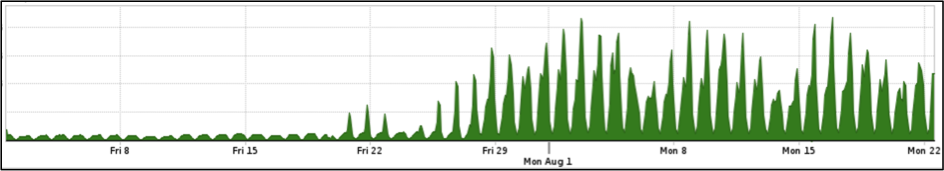
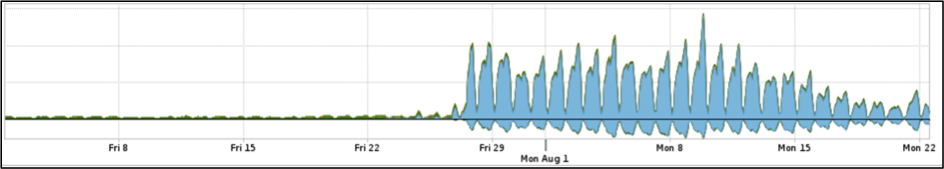
Even without DDoS attacks, Internet traffic grew significantly before and during the Olympics, due to the increased number of visitors and athletes. As such, it was imperative that the ‘defenders’ were able to clearly identify anomalous traffic from normal traffic.
The following graphs show two breakdowns of traffic increase for Google and Facebook.
The defenders used a number of methods to thwart the attackers, the most important being Flow Telemetry (Netflow, sFlow, cFlow, IPFIX) for detecting, classifying and tracing attack traffic.
Attack traffic was then mitigated using Intelligent DDoS Mitigation Systems (IDMS), which are capable of cleaning attack traffic from Layer 3 and 4 through to Layer 7. These were located in both the in-country Telecoms provider networks and an over the top Cloud-Based DDoS service.
This multi-layered strategy is considered best practice, as the Cloud-Based service can mitigate very large volumes of unwanted traffic (for example, UDP traffic destined for a TCP based service) and the smaller capacity in-country IDMS can mitigate lower volume flood and application layer attacks.
In addition, equipment can also be deployed within the data centre providing a final layer of protection.
This strategy enabled the defenders to use the best available mitigation bandwidth when the attacks were very large.
The successful detection and mitigation would not have been possible without two key things. The first, the human efforts before and during these events. The second, the ability of all the teams involved to communicate, develop an incident response plan, practice that plan, and adapt and evolve it over a number of months as the attackers themselves also evolved their methods. In doing so it enabled the defenders to stay one step ahead.
The Olympic experience proved it is possible – with the corrects tools, people, plans and best practices – to successfully defend against some very determined attackers launching large and complex attacks over a sustained period of time.
Tony Scheid is a Senior Consulting Engineer with Arbor Networks. He has been with Arbor for over 10 years and has considerable experience in design and deployment of DDoS detection and mitigation systems for large telecommunications providers, MSSP’s and enterprises.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.