
The APNIC Network Health Dashboard (DASH) is a monitoring and alerting platform available to all APNIC Members. It provides a consolidated view of routing and security status for their networks, along with customizable alerts, allowing Members to take timely action to protect infrastructure and maintain Internet stability.
The platform was developed in response to priorities identified through regular APNIC Membership surveys. Security has been consistently raised by Members as a key priority since 2011. In the 2024 APNIC Survey, Internet security was ranked among the top three strategic challenges for 40% of respondents, and as the number one operational challenge for 57%.
This feedback has guided APNIC’s development of DASH and related initiatives focused on improving network visibility, enhancing stability, and promoting security best practices across Member networks.
Existing DASH services
DASH brings together several existing services that address common operational and security issues faced by network operators.
- Routing status helps Members detect inconsistencies between their announced BGP routes and RPKI or IRR data. The service flags many routing issues, such as invalid route origins, missing IRR objects, or potential route hijacks, and supports near real-time alerts.
- Suspicious traffic draws on data from the APNIC Community Honeynet Project, which analyzes traffic from more than 400 honeypots deployed globally. It identifies when a Member’s network is sending suspicious traffic, often a sign of infected or compromised systems.
- Bogons monitors for unallocated or invalid prefixes being announced or propagated, which can indicate network misconfiguration or missing filters.
- The MANRS Readiness Score measures how closely a Member’s operations align with the routing security best practices promoted through the MANRS initiative.
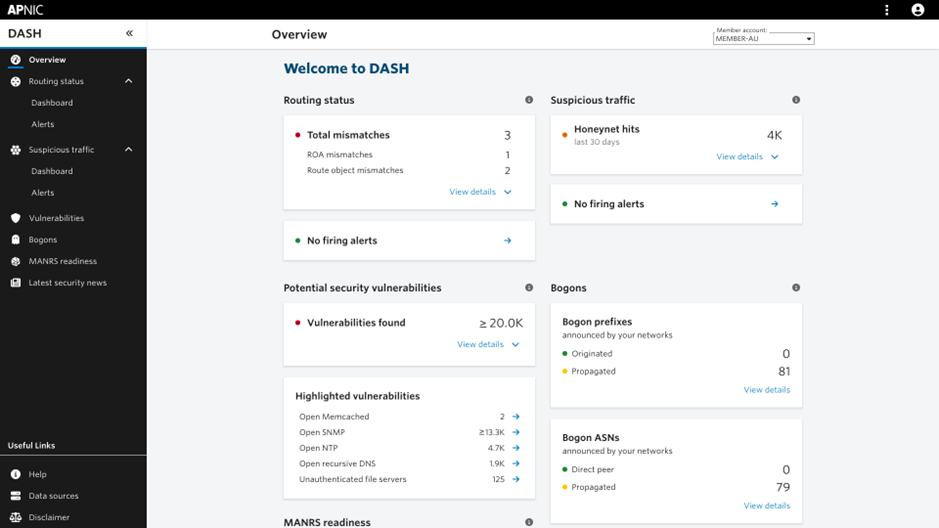
New feature: Potential Security Vulnerabilities
The new Potential Security Vulnerabilities service enables Members to see where open or misconfigured services within their address space may introduce risk.
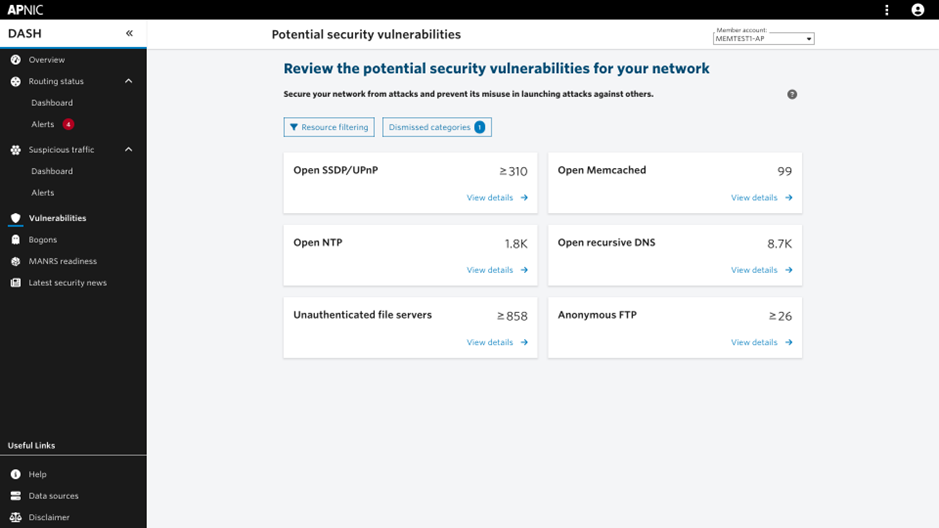
This service is powered by integration with Shodan, a third-party security platform that continuously scans the Internet to identify services and applications that might be exposed. DASH correlates this information with the Member’s address space to flag possible vulnerabilities that need attention.
Each category of vulnerability is defined and reviewed by APNIC’s security and network experts. The findings help Members mitigate risks to system integrity and data confidentiality, and reduce the likelihood of their networked computers being used in Distributed Denial of Service (DDoS) attacks, such as amplification or reflection attacks, against others. By presenting these details in an accessible form, DASH assists its Membership to take action and contributes to a safer Internet ecosystem.
Working with vulnerability data
When a vulnerability is detected, DASH presents detailed information for its investigation. Members can see the affected IP address, hostname, and associated service port, along with the date it was last observed.
The interface supports filtering by Autonomous System Number (ASN) or prefix, which allows Members to focus on the portions of their network they directly manage. Issues can be dismissed individually or by category, helping operators maintain a clear and relevant dashboard view.
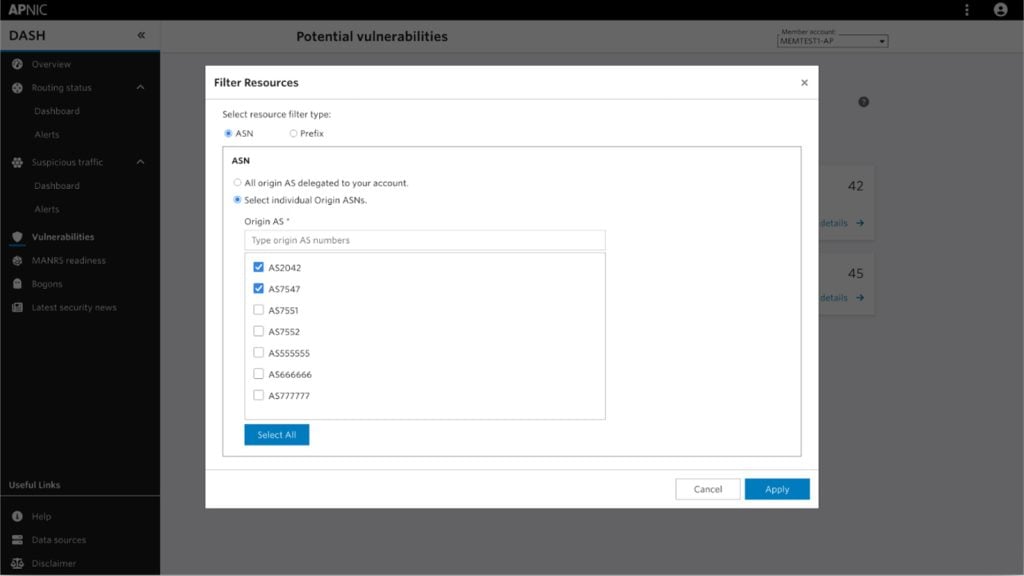
Towards a more secure Internet
With this new service, DASH provides a more comprehensive view of network health, helping Members identify and address security vulnerabilities early—ultimately contributing to a safer Internet for all
The new Potential Security Vulnerabilities service is available now, and Members are encouraged to log in and review their results. Please try the new feature and let us know how we can make it more valuable.
Watch Rafael’s APNIC 60 Lightning Talk on DASH’s new Potential Security Vulnerabilities feature.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.

how to get dash tool
Hi Saif, DASH is available to all APNIC Members. Login here: https://dash.apnic.net/