
The Domain Name System (DNS) translates human-readable domain names into machine-readable IP addresses, serving as the starting point for most network activities and playing a crucial role in the Internet. Unfortunately, the pivotal role of DNS also attracts numerous attackers. According to a Cisco report, over 91% of Internet attacks are backed by the resolution of malicious domain names. Considering that blocking the DNS resolution of malicious domains can effectively curb cyber attacks, the security community has been continuously exploring methods for handling malicious domains, like domain takedowns.
Recently, Protective DNS (PDNS) has been proposed and developed. As shown in Figure 1, when a PDNS server queries a malicious domain listed in its blocklist, it rewrites the DNS response to provide a ‘safe’ answer (for example, resolving to a reserved IP address) to block it. PDNS offers a simpler solution for handling malicious domains without requiring changes to the DNS protocol or collaboration with other organizations (such as law enforcement agencies and domain registrars in domain takedown) to block domains, and it can provide real-time protection.
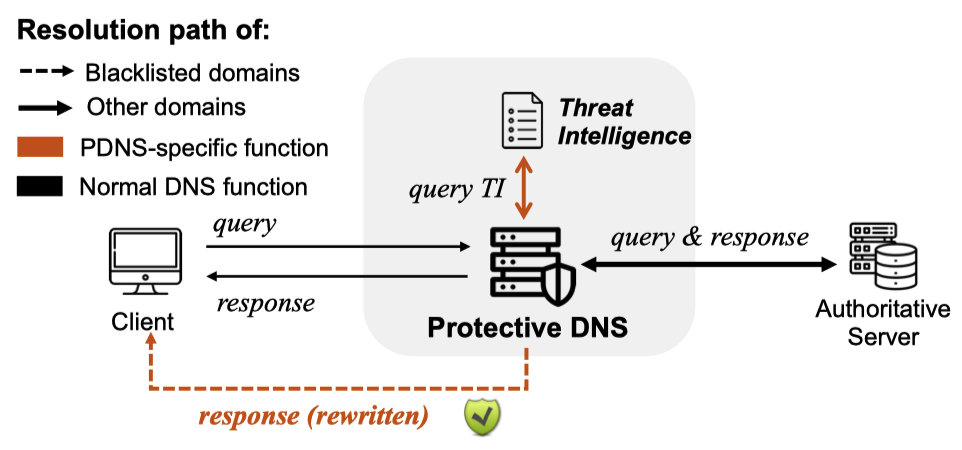
Although the concept of PDNS is relatively new, it has already gained support from several major DNS services, such as Cloudflare and Quad9. Moreover, economies including the United States, Canada (CIRA), and Europe (DNS4EU) have also initiated efforts to deploy national PDNS infrastructures.
My fellow researchers from Tsinghua University and I recently published a comprehensive measurement study on the implementation and security incidents of Protective DNS at NDSS 2024. Combining results from active probing, we identified 17,601 PDNS resolvers across the network and uncovered three critical security practice flaws.
Protective DNS is widely deployed in 117 economies or regions
By comparing with authoritative resolution results and excluding the impact of other domain name manipulations, we identified 17,601 PDNS resolvers out of 193,888 stable recursive resolvers across six scanning experiments, accounting for 9.08%. These PDNS resolvers are distributed across 117 economies or regions, covering 1,473 Autonomous System Numbers (ASNs).
Despite this wide distribution, the deployment of PDNS varies significantly among different economies. As shown in Table 1, the United States has the highest number of PDNS, with 6,296 resolver IP addresses. Specifically, PDNS in the United States spans 208 ASNs, indicating broad coverage. Even university DNS resolvers have implemented protective measures, with 13 PDNS resolvers found in eight universities, including Columbia University and the University of California, Los Angeles.
| CC | Number of IPs | ASN | IPs |
| US | 6,296 (35.8%) | 20115 (CHARTER-20115) | 1,074 (6.1%) |
| IRN | 1,225 (7.0%) | 3303 (SWISSCOM) | 777 (4.4%) |
| CN | 1,205 (6.8%) | 209 (CenturyLink Communications) | 705 (4.0%) |
| JP | 1,056 (6.0%) | 5617 (TPNET) | 613 (3.5%) |
| CH | 804 (4.6%) | 17506 (UCOM) | 576 (3.3%) |
| PL | 745 (4.2%) | 10796 (TWC-10796- MIDWEST) | 570 (3.2%) |
| MD | 635 (3.6%) | 21342 (AKAMAI-ASN2) | 523 (3.0%) |
| ID | 540 (3.1%) | 8926 (MOLDTELECOM-AS) | 480 (2.7%) |
| OM | 380 (2.2%) | 2519 (VECTANT) | 420 (2.4%) |
| RO | 367 (2.1%) | 50010 (Nawras-AS) | 379 (2.2%) |
| 117 economies | 1,473 ASNs | ||
The implementation of PDNS’s blocking function varies
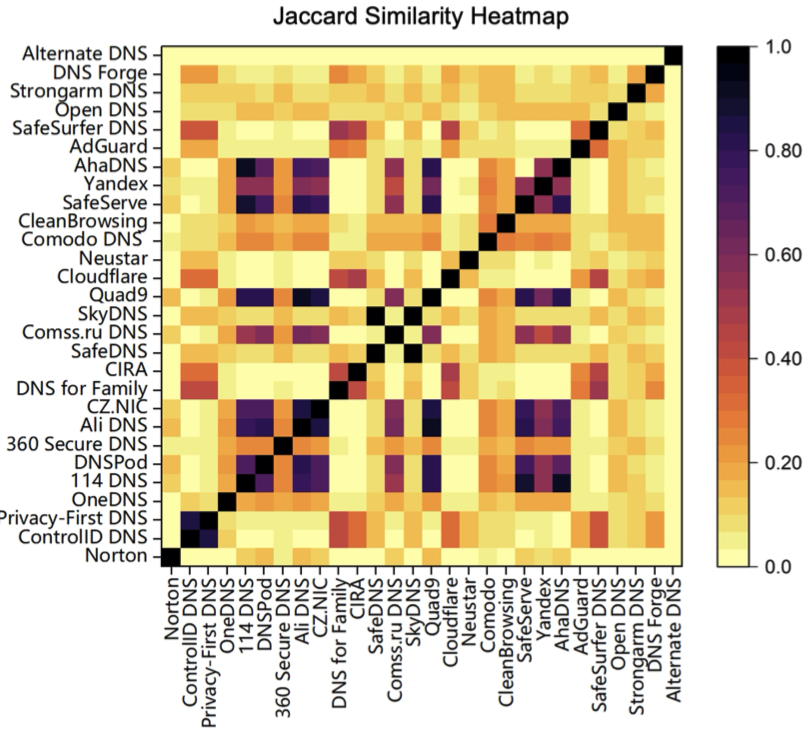
Firstly, the blocklist used by PDNS is crucial for blocking attacks. However, our results indicate that the blocklists used by different PDNS resolvers differ significantly. Figure 2 shows the similarity results of 28 well-known PDNS providers. The most similar are SkyDNS and SafeDNS (with a similarity of 0.99), which appear to be parallel services in Russia and other economies. However, the average blacklist similarity of alternative DNS with other DNS is only 0.21%. Most PDNS blocklists have little in common with those of other providers.
Secondly, the rewrite strategies of PDNS are also biased. As shown in Table 2, the most common method is responding with a safe IP address, adopted by 56.45% of PDNS, resulting in 577 safe IPs. Of these, 28.0% (162 IPs) return a block notification, such as block/forbid/intercept and complaint/appeal, when accessed via HTTP(S). Interestingly, 35 PDNS resolvers return category-specific IPs. For example, Hosting24’s PDNS returns 127.42.0.15 for malware and 127.42.0.155 for phishing domains.
| Rewriting policy | PDNS | Policy | Blocked domains | Malware | Botnet | Phishing | Adult | Spam | Tracker |
| Secure IP | 9,935 (56.45%) | 577 | 483 | 332 | 58 | 45 | 27 | 20 | 1 |
| Special-use IP | 7,209 (40.96% | 351 | 424 | 371 | 12 | 12 | 8 | 20 | 1 |
| No data | 822 (4.67%) | 222 | 142 | 44 | 16 | 9 | 11 | 0 | |
| Secure CNAME | 449 (2.55%) | 70 | 544 | 375 | 58 | 46 | 24 | 40 | 1 |
| Error response code | 408 (2.32%) | 3 | 362 | 267 | 28 | 33 | 13 | 20 | 1 |
Table 2 — Rewriting policies and each category’s average number of blocked domains.
Related security issues, especially Denial of Response attacks
However, analysis of the results from 17,601 PDNS resolvers reveals that, unfortunately, this service intended for security protection is no longer secure and may even introduce exploitable security risks. Specifically, this work identified three security risks stemming from flawed blocking strategy implementations:
- Denial of Response (DoR) due to aggressive non-response strategies.
- Dangling cloud IPs vulnerable to attacker takeover and abuse.
- Multiple flawed blocking strategies undermining PDNS protection subverting PDNS protective features. Due to space constraints, this work provides a detailed discussion of the DoR risk.
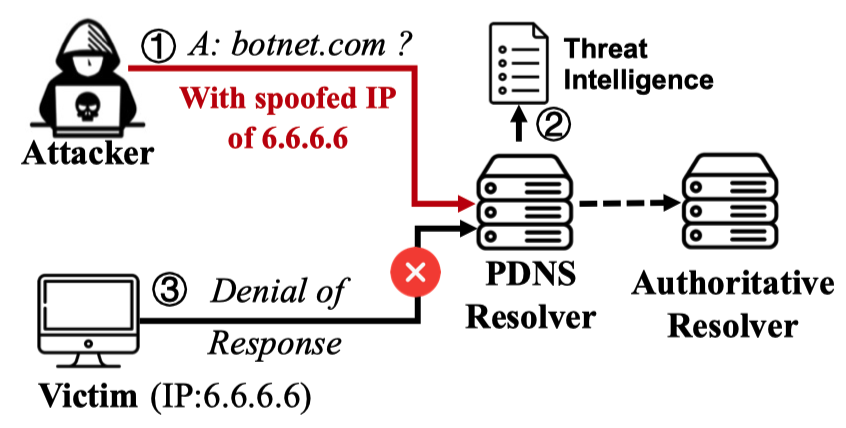
This work discovered that 28 PDNS resolvers temporarily block all domain resolutions for a client after receiving multiple malicious domain queries, even for benign domains such as google.com.
Based on this finding, we proposed the DoR threat model. Specifically, an attacker can disrupt all domain queries from a victim by sending a small number of malicious domain queries to the PDNS resolver using the spoofed victim’s IP address, potentially blocking the victim’s access to services like Google Search. Active testing revealed that seven of the 28 DoR-affected resolvers belong to well-known DNS providers. Notably, a PDNS resolver from ControlD DNS stops resolving any queries from a client for up to 12 hours after receiving just a dozen malicious domain queries.
Lessons learned for better implementation of PDNS
Due to the lack of standard guidelines, implementation flaws and security risks make end users vulnerable to attacks. Considering the widespread deployment and potential of PDNS, this work proposes several recommendations based on the analysis of the implementation and security practices of PDNS across the network.
- PDNS protection strategies should be transparent to users. To mitigate the impact of false positives, it is recommended to set up a page informing users of the reason for domain blocking (similar to the approach of 360 Secure DNS) and provide a user complaint channel (such as email).
- The infrastructure used for rewriting should be secure. Although using third-party resources (such as cloud IPs and sinkhole domains) are convenient, PDNS providers should exercise caution and promptly handle expired resources to avoid threats.
- Defend against potential DoR threats. Specifically, when responding to clients issuing a large number of DNS queries to malicious domains, PDNS operators can reply with a large DNS answer, forcing the client to use DNS over TCP, which also serves as a robust IP spoofing defence measure.
Mingxuan Liu, Assistant Researcher of Zhongguancun Lab, received her PhD degree from Tsinghua University in 2023. Her main research interests are Internet infrastructure security analysis and cybercrime governance based on data-driven methodology.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.
