Domain names, vital for tasks like digital certificate authentication, face growing vulnerabilities in our evolving digital landscape. A key threat is hosting-based domain takeover, where adversaries exploit domains resolved to expired or unreferenced endpoints of public hosting platforms (for example, Content Delivery networks (CDNs), web hosting, and Operational Support Systems (OSS)). With more organizations using hosting services, temporary resource allocation in such environments is problematic. Transient hosting service endpoints can be exploited if not effectively monitored, leading to breaches even at major companies like Microsoft.
Recent research introduces a new detection method for hosting-based dangling domains and assesses the complexity of this growing threat.
Hosting-based domain takeover
In the digital era, companies often use public platforms like CDNs for web hosting. But what’s the mechanism behind this, and where are the potential vulnerabilities?
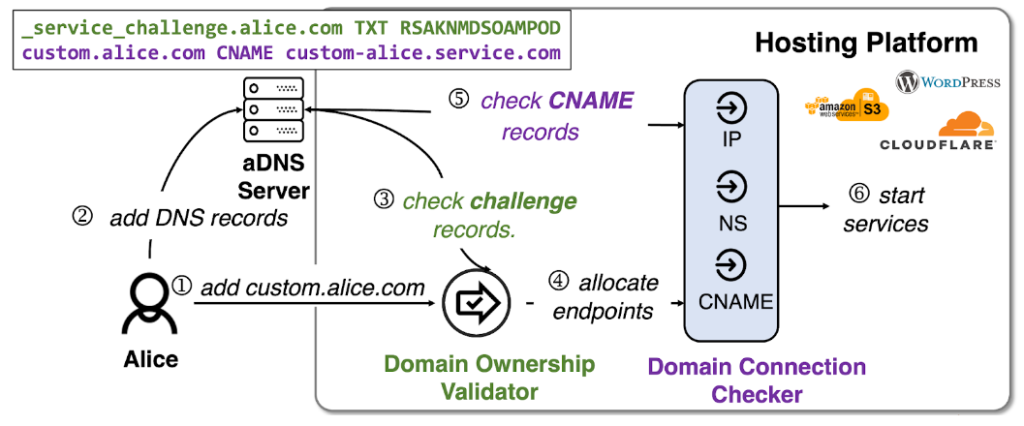
Figure 1 illustrates the hosting setup process involving two stages:
- Domain ownership validation (Steps 1-3), where a customer, Alice, proves her domain ownership using a challenge token (for example, a DNS TXT value) assigned by the platform.
- Service allocation and domain connection (Steps 4-6), where the platform provides 1-2 service endpoints (such as CNAME) post-verification, and Alice activates the service by adding CNAME records.
But what happens when things go wrong?
The chinks in the armour: Hosting vulnerabilities
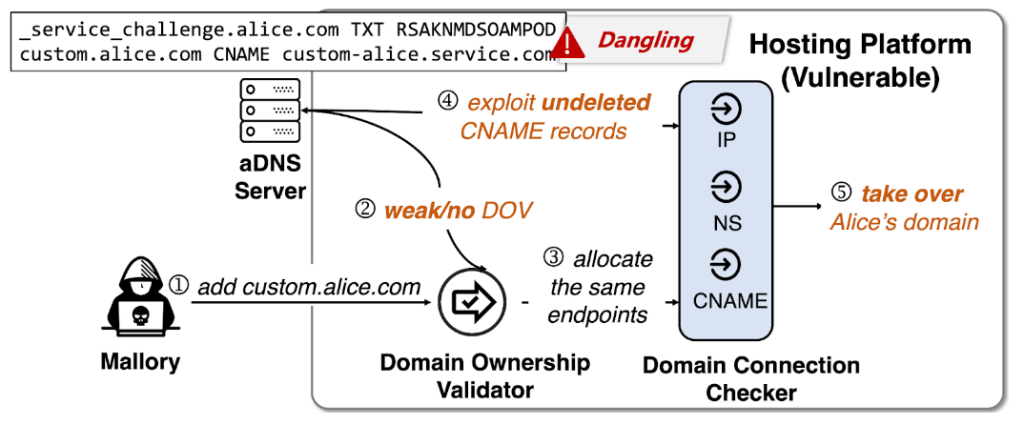
Hosting service vulnerabilities stem from poor domain ownership validation, allowing attackers to reuse the released endpoints. If the DNS records aren’t promptly purged after service expiration, they become dangling and exploitable. This mirrors the ‘use-after-free’ programming bug, where domains point to freed resources that can be maliciously reused.
The anatomy of a hosting-based domain takeover
Figure 2 depicts the threat model. Mallory uses the same CNAME endpoints, bypasses domain connection validation, and hijacks Alice’s domain name.
HostingChecker: A novel detection framework
The HostingChecker framework, introduced at ACM SIGMETRICS 2023, aims to identify public hosting services and detect vulnerable domains on discontinued endpoints. The challenges are:
- The diversity of service types and hosting strategies makes manual inspection difficult.
- The need for efficient detection of vulnerable popular domains at scale.
The inspiration behind HostingChecker’s design stems from three key observations:
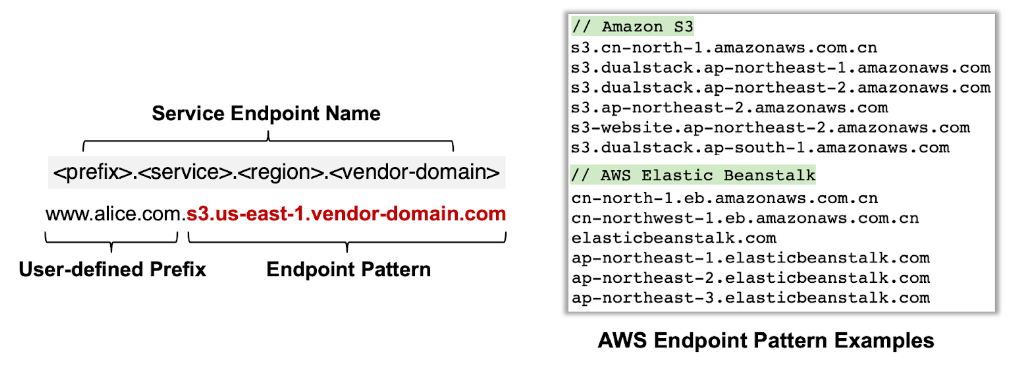
- Service endpoint naming conventions (Figure 3): Across the board, hosting services, whether they’re CDNs, OSS, or website builders, tend to follow similar endpoint naming practices.
- High domain dependency (Figure 4): Hosting service endpoints can serve numerous domains, resulting in high domain dependency — many apex domain names pointing to a single shared domain suffix.
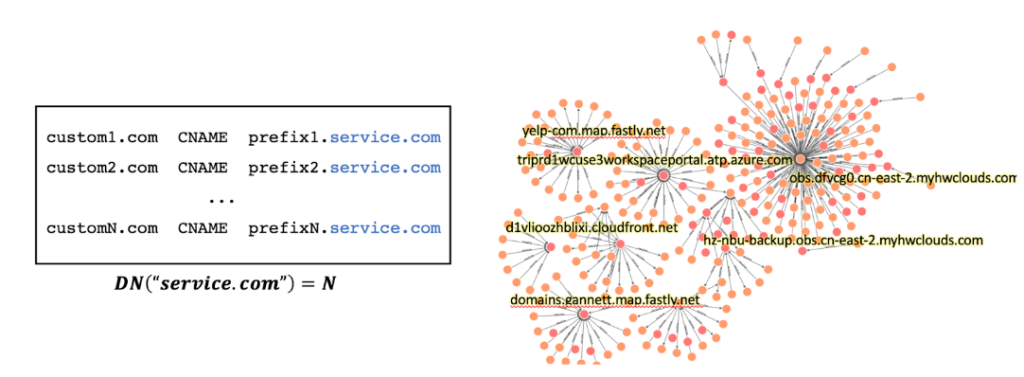
- Domain name resolution characteristics: The domain resolution chains can indicate if domains are hosted on public services. Certain DNS responses can also indicate service status. For example, when a service expires, the assigned CNAME may become an NXDOMAIN.
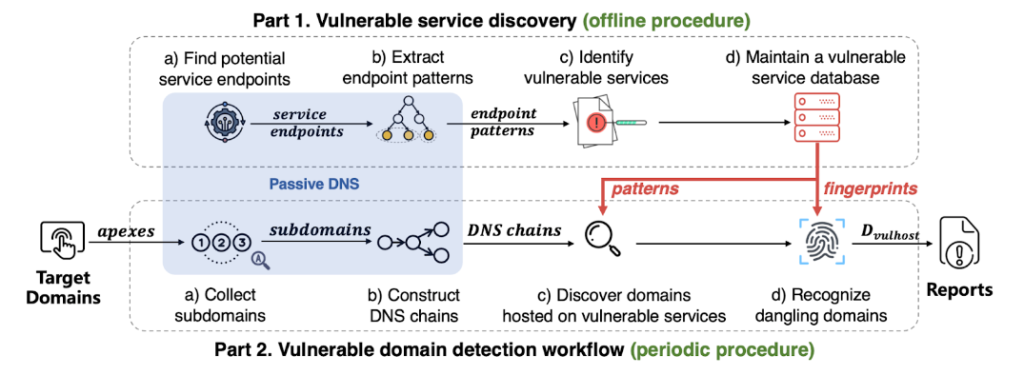
Based on the above observations, we designed the novel framework of HostingChecker (Figure 5). Its main functions include:
- Discovering vulnerable hosting services: HostingChecker leverages passive DNS traffic to recognize service endpoints by their naming patterns. Meticulous manual analysis is then performed to identify vulnerable services.
- Pinpointing vulnerable domains: HostingChecker builds DNS chains from passive data, and identifies domains hosted on risky services through pattern comparisons. Further detection of dangling domains is done through proactive HTTP and DNS probes.
Major findings and insights
We deployed HostingChecker using a representative passive DNS dataset, 114DNS, which processes 600 billion DNS queries per day. From December 2021 to July 2022, it examined the top 1M Tranco domains and specific .edu and .gov domains, revealing widespread hosting service vulnerabilities.
Vulnerability assessment of hosting services
As shown in Table 1, HostingChecker identified 165 hosting services and 995 endpoint patterns in the 114DNS dataset, with 65 services found vulnerable. These include famous cloud object storage services (such as Alibaba OSS and Huawei OBS), CDNs (such as Baidu and Cloudflare), and website builders (like Wix).
| Categories | # Vendors | # Endpoint patterns | # Services | |||
| All | Vulnerable | All | Vulnerable | All | Vulnerable | |
| Cloud Storage | 7 | 7 | 130 | 118 | 12 | 9 |
| CDN | 25 | 7 | 247 | 31 | 44 | 8 |
| Website Builder | 51 | 40 | 156 | 105 | 60 | 44 |
| Others | 27 | 4 | 462 | 4 | 49 | 4 |
| All | 88 | 52 | 995 | 258 | 165 | 65 |
Domain connection vulnerabilities in hosting services
We summarized various domain validation methods (Figure 1, steps 3-5) for hosting services and found significant security risks even among the most popular large providers. As shown in Table 2, public hosting providers employ diverse domain connection methods, but most (7/9) of them are exploitable for domain takeover.
| Method | Type | Connect a custom domain to… | Services | Exploitable |
| CNAME | M1 | Fixed canonical domains | 12 | ⬤ |
| M2 | Any canonical domains customized by any users | 70 | ⬤ | |
| M3 | New canonical domains customized by new users | 12 | ⭘ | |
| M4 | The canonical domains allocated from a candidate pool | 5 | ◐ | |
| M5 | Canonical domains containing newly generated random labels | 47 | ⭘ | |
| NS | M6 | Fixed nameservers | 1 | ⬤ |
| M7 | The nameservers allocated from a candidate pool | 5 | ◐ | |
| IP | M8 | Fixed IPs | 8 | ⬤ |
| M9 | The IPs allocated from a candidate pool | 4 | ◐ |
The magnitude of the domain vulnerability landscape
The scale of domains using vulnerable services paints a worrying picture for the broader digital ecosystem. About 114k domains were found hosted on vulnerable services, posing potential threats like data breaches or malware attacks. Specifically, 10,351 FQDNs under the Tranco Top 1M domains, including well-known institutions (such as Stanford and Rice) and corporations (like Baidu, Huawei, and Marriott), were confirmed vulnerable.
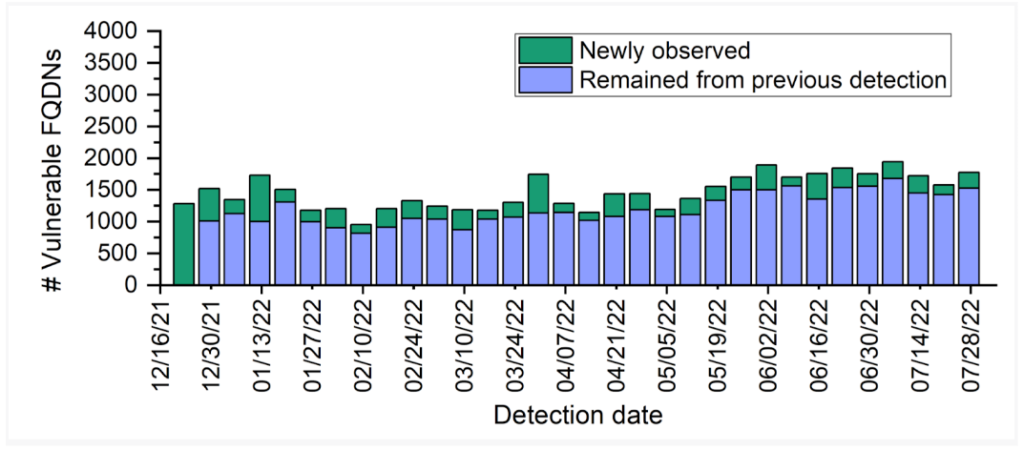
The threat of domain takeovers is prevalent and on the rise (Figure 6), demanding continual vigilance. Research indicated the emergence of over 200 new vulnerable domains weekly, emphasizing the persistent and growing nature of this security concern.
Best practices for public hosting services
HostingChecker is running continuously with 114DNS to find and report vulnerable domains. Our analysis also leads to suggestions to mitigate domain takeover threats:
- Strict Domain Validation: Employ standard validation methods like one-time tokens in TXT records rather than just checking reassignable endpoints.
- Distinct endpoints: Use unique, non-collidable endpoints (pairs) for each user and ensure each domain and account is distinctive.
- Maintain a historical record: Keep a record of user-defined labels and hosted domains linked to accounts, preventing attackers from reusing endpoint names.
- Proactive security alerts: Regularly update customers on potential threats. Alerts can include notifications about service expiration, the misconfiguration of wildcard DNS records, and any unusual domain activity.
Concluding thoughts
The rise in hosting-based domain takeovers highlights the need for strict domain validations and user awareness. For hosting services, collaboration and shared intelligence can strengthen defences.
For a detailed study, see our paper in the ACM SIGMETRICS 2023 titled ‘Detecting and Measuring Security Risks of Hosting-Based Dangling Domains’.
Mingming Zhang is an assistant researcher at ZGC Lab, Beijing. Her research interests are Internet infrastructure security, network protocol vulnerabilities, and new cyber threats.
Other authors including Xiang Li, Baojun Liu, Jianyu Lu, Yiming Zhang, Jianjun Chen, Haixin Duan, Shuang Hao, and Xiaofeng Zheng also contributed to this work.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.
