
The Domain Name System (DNS) is a critical part of the Internet infrastructure, mapping domain names to IP addresses. However, the DNS is also vulnerable to privacy concerns, as the queries sent across it can be intercepted and used for tracking or other malicious purposes. One solution to this issue is the adoption of query name minimization (qmin), a recursive DNS resolver privacy feature introduced in 2016.
In this blog post, we discuss the recent paper “A Second Look at DNS QNAME Minimization,” presented at the Passive and Active Measurement conference (PAM 2023). The paper was a collaborative effort between Karlstad University, SIDN Labs, and Internetstiftelsen and aimed to measure the adoption of qmin since its introduction in 2016.
What is qmin?
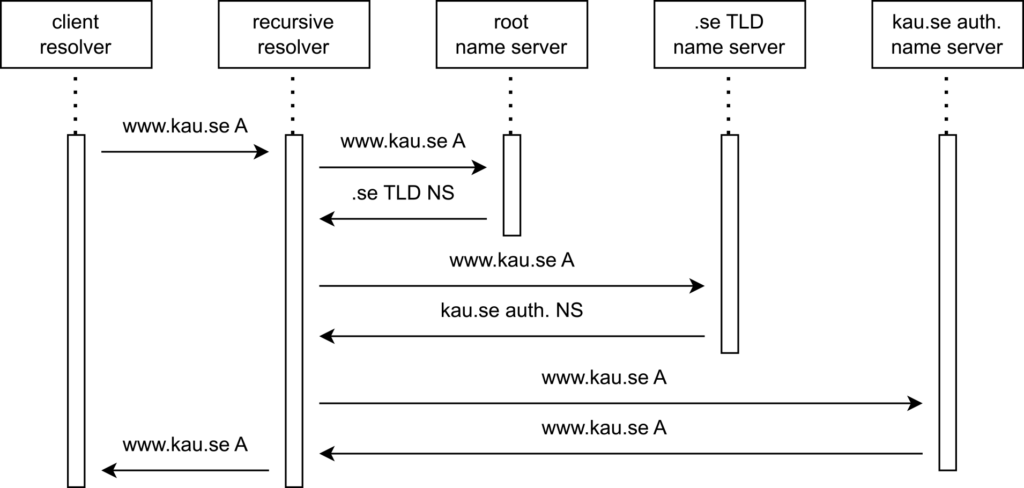
When a DNS query is sent, it passes through a recursive DNS resolver responsible for querying the DNS name servers to retrieve the requested resource record. Traditionally, a recursive resolver would send the entire query name to each authoritative name server.
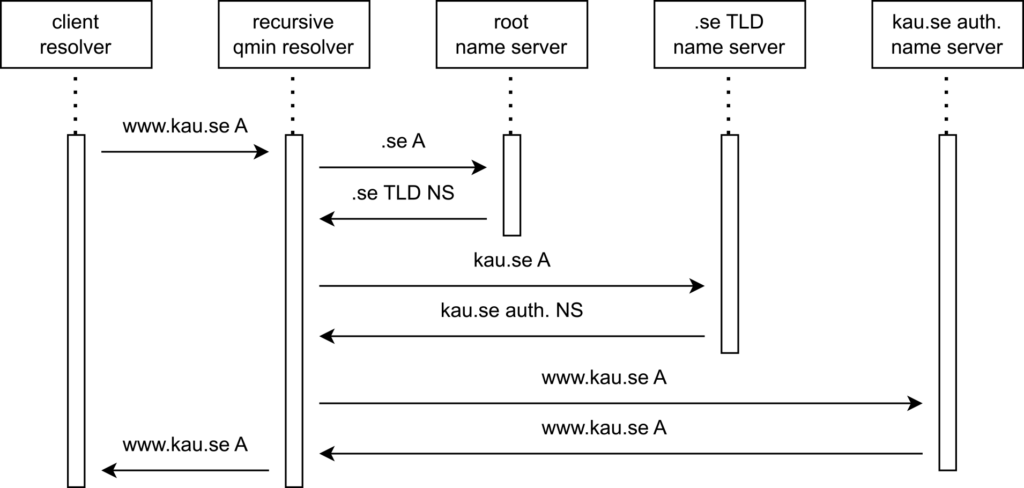
Query name minimization (qmin) is a privacy feature that limits the amount of information sent in DNS queries to enhance privacy (RFC 9156). Since its introduction in 2016, qmin has been gaining popularity due to its potential to improve privacy. In the study titled “A First Look at QNAME Minimization in the DNS,” researchers examined the adoption of qmin in 2018 using active and passive measurements as well as controlled experiments. In our study, we built and considerably extended the methodology used by De Vries and fellow researchers, using active and passive measurements to track the trend of qmin adoption and to understand the characteristics of the resolvers that have adopted qmin.
Active measurements
Our active measurement methods were improved from previous studies, and we used three geographical locations to measure open resolvers. We queried each open resolver 100 times and set up a new domain using a wildcard label to mitigate cached delegations. These enhancements allowed us to observe additional behaviour when classifying resolvers, including ‘conflicting resolvers’, which minimize queries inconsistently.
Passive measurements
Our passive measurements used data collected from the k-root server and the .nl country-code TLD (ccTLD) to present the evolution of qmin adoption on a larger scale. We classified queries as minimized when they contained one label at the root and two at .nl. We filtered out queries from Google’s Chrome browser relating to non-existent single-label domain names to avoid overestimation. Our methodology provided deeper insight into qmin adoption, including who is leading and who is lagging, as well as discovering occasional information leakage from qmin-enabled resolvers.
Controlled experiments
In addition to our passive and active measurements, we conducted controlled experiments to examine the performance of popular open-source resolvers (Bind, Unbound, Knot Resolver, and PowerDNS) when handling minimized queries. We used the Cisco Umbrella Top 1M list of the most popular queries based on passive DNS usage. The resolvers were configured to have the same cache size and with DNSSEC turned off. We looked at both relaxed and strict modes of enabling qmin and compared the results with the previous study by De Vries and fellow researchers, and we saw that the trend is that the number of packets are going up for most of the resolvers, while the error rates are going down regardless of mode.
Qmin gains momentum
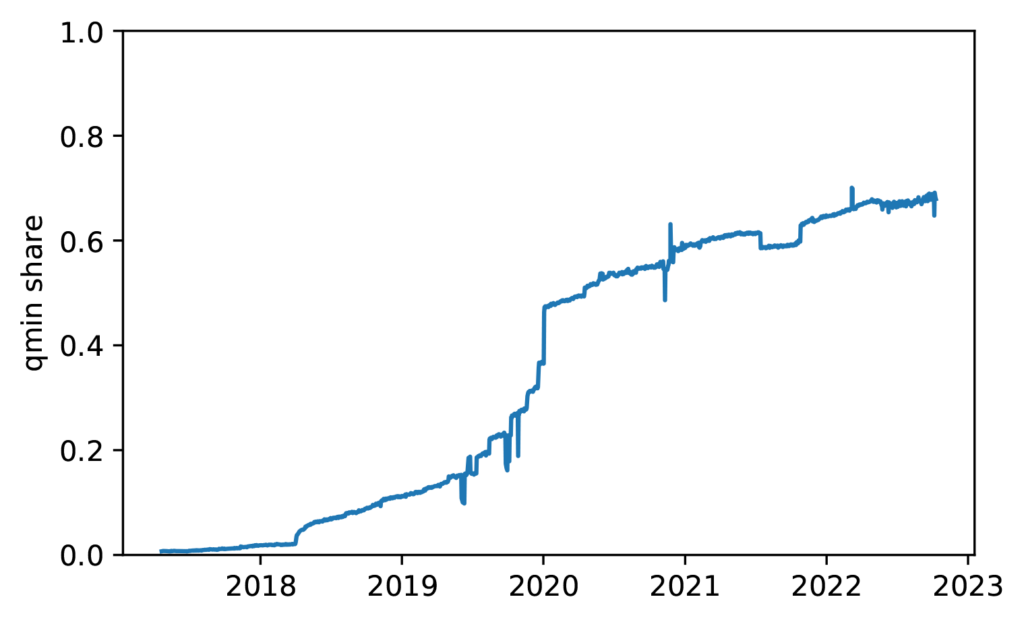
Our study shows that the adoption of qmin has increased significantly in recent years. The adoption has grown from 2.5k resolvers used by RIPE Atlas probes in 2018 to 14k in 2022 and from 18k open resolvers categorized as qmin-enabled in 2018 to 80k in 2022.
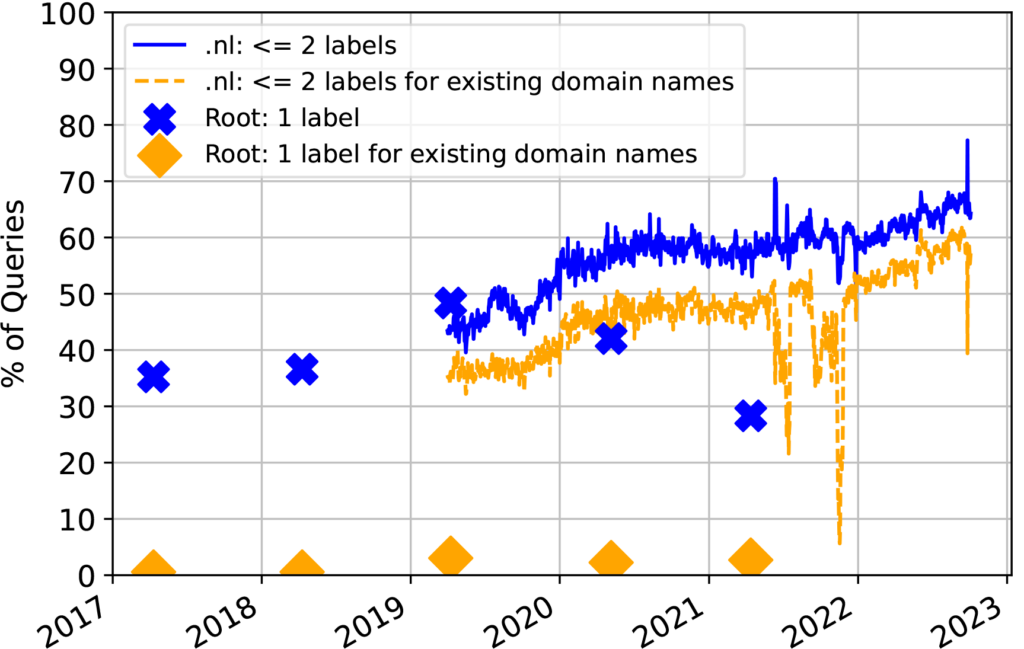
The results from the study also reveal an increase in qmin adoption through passive measurements on root and TLD name servers. In 2018, the adoption rate was only 0.6%, but in 2022 it had risen to 2.5% on one root server and from 35.5% in 2019 to 57.3% on the .nl TLD servers.
While the results from the RIPE Atlas probes may not represent the average resolver on the Internet, the overall trend towards increased qmin adoption is positive news for Internet privacy. With more and more organizations adopting qmin, the DNS ecosystem is becoming more secure and privacy-friendly.
Corner cases
When measuring minimized queries, it is essential to consider the vantage point’s limitations. The client-side active measurements only measured qmin at the third and fourth-level domains. Some corner cases suggested that the number of resolvers minimizing queries at lower levels (root and TLD) could be even higher than measured.
The active measurements on resolvers used by RIPE Atlas probes classified Google Public DNS resolvers as qmin-enabled. These results were contradicted by active measurements on open resolvers that consistently showed different responses from the Google Public DNS resolvers based on the domain.
Together with NLnet Labs, we contacted the Google Public DNS Team. They wanted to be credited for minimizing queries at the root and TLD level, which was not visible at the fourth-level domain.
$ dig @8.8.8.8 a.b.qnamemin-test.nlnetlabs.nl TXT +short
"NO - QNAME minimisation is NOT enabled on your resolver :("$ dig @8.8.8.8 a.b.qnamemin-test.internet.nl TXT +short
"HOORAY - QNAME minimisation is enabled on your resolver :)!"$ dig @8.8.8.8 a.b.qnamemintest.net TXT +short
"NO - QNAME minimisation is NOT enabled on your resolver :("The corner cases prompted a discussion about depth limits to qmin. We propose using the Public Suffix List (PSL) with one additional label (PSL+1) to set the depth limit for qmin. PSL is a list of TLDs used to restrict cookie settings, maintained by Mozilla, and includes effective TLDs like ‘.com’ and ‘.net’, as well as multi-label TLDs like ‘.ac.uk’ and ‘.co.jp’. The PSL could be a reference for determining the depth limit for qmin by identifying the authoritative DNS zones and determining when to stop minimizing queries.
Conclusion
The study concluded that qmin adoption has significantly increased since its introduction, indicating a positive trend toward enhanced DNS privacy. However, the study also revealed the importance of balancing privacy and performance when setting the depth limit for minimizing labels. This study provides valuable insights into the adoption and impact of qmin in the DNS and can inform future DNS privacy and security improvements.
Jonathan Magnusson is a PhD student in Cybersecurity and Network Analysis of the DNS at Karlstad University (KAU) in Sweden, sponsored by The Swedish Internet Foundation (IIS).
Paper Authors: Jonathan Magnusson, Moritz Müller, Anna Brunstrom, Tobias Pulls.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.

Great article!
Perhaps this is also interesting:
https://dnsthought.nlnetlabs.nl/#qnamemin