
As a fundamental Internet infrastructure, the Domain Name System (DNS) is continually under attack. While various DNS security mechanisms have been proposed, standardized, and implemented, little is known about how prevalent they are in the current DNS ecosystem.
To answer this, we at Waseda University have conducted a large-scale survey into the adoption of various DNS security mechanisms — DNSSEC, DNS Cookies, CAA, SPF, DMARC, MTA-STS, DANE, and TLSRPT — and in doing so identified what effects adoption rates.
In this blog post, I will report the results of our survey and discuss practical ways to ensure the widespread use of security mechanisms in the future.
- Easy-to-deploy DNS security mechanisms and those that are not expensive to set up are more widely adopted.
- Root servers, and top-level domains are leading adopters of DNSSEC and DNS Cookies. Top 10 websites are leading adopters of SPF and DMARC.
- We encourage domain name administrators to check the state-of-the-art DNS security mechanisms and the tools/services that will ease the configuration burden.
Scope of survey
In this survey, we used root servers, top-level domains (TLDs), and domain names used by well-known websites. We targeted IPv4 addresses of all 13 root servers, 13 legacy gTLDs and 254 ccTLDs, and the top 10K domain names published by Tranco.
Each IP address collected was tested on a domain name basis. In cases where we observed at least one IP address that operates a security mechanism, we assumed that the entire domain name space has adopted that security mechanism.
Table 1 shows the DNS resource records and signatures required when setting up the security mechanism. We checked if the target domain name had the target resource records and signatures.
| Configure | Target domain name | RR | Signature | |
| DNSSEC | Server | <domain name> | RRSIG | n/a |
| DNS Cookies | Server | n/a | n/a | n/a |
| CAA | Server | <domain name> | CAA | n/a |
| SPF | Server | <domain name> | TXT | v=spf1… |
| DMARC | Receiver | _dmarc.<domain name> | TXT | v=DMARC1… |
| MTA-STS | Receiver | _mta-sts.<domain name> | TXT | v=STSv1… |
| DANE | Receiver | _25.tcp.<mail server domain name> | TLSA | n/a |
| TLSRPT | Receiver | _smtp._tls.<domain name> | TXT | v=TLSRPTv1… |
Table 1 — DNS resource records and signatures required when setting up the security mechanism.
Easy-to-deploy security mechanisms are more widely adopted
Table 2 shows the percentage of DNS servers that have adopted each security mechanism. The key takeaways are:
- DNSSEC and DNS Cookies have a high adoption rate in the DNS core, such as Root and TLDs.The adoption rate for domain names used by well-known websites is low.
- The adoption rate of SPF and DMARC is higher than that of other security mechanisms.
- The adoption rate of DANE is less than 1% for all data sets.
DNS Security Adoption 2021
| DNS Servers | DNSSEC (%) | DNS Cookie (%) | CAA (%) | MX (%) | SPF (%) | DMARC (%) | MTA-STS (%) | DANE (%) | TLSRPT (%) |
| Root | 100.00 | 100.00 | 0.00 | 0.00 | 0.00 | 0.00 | 0.00 | 0.00 | 0.00 |
| ccTLD | 56.69 | 81.10 | 0.00 | 6.30 | 0.00 | 0.00 | 0.00 | 0.00 | 0.00 |
| gTLD | 100.00 | 45.45 | 0.00 | 0.00 | 0.00 | 0.00 | 0.00 | 0.00 | 0.00 |
| Top 10 | 0.00 | 20.00 | 30.00 | 30.00 | 100.00 | 88.89 | 33.33 | 0.00 | 33.33 |
| Top 100 | 4.00 | 21.00 | 48.00 | 48.00 | 96.51 | 84.88 | 5.81 | 0.00 | 5.81 |
| Top 1K | 9.20 | 13.80 | 22.70 | 22.70 | 92.85 | 74.01 | 1.48 | 0.57 | 1.82 |
| Top 5K | 8.60 | 18.58 | 14.90 | 14.90 | 89.86 | 58.49 | 0.75 | 0.84 | 0.98 |
| Top 10K | 7.67 | 17.40 | 12.98 | 12.98 | 88.66 | 54.09 | 0.51 | 0.84 | 0.74 |
Table 2 — The percentage of DNS servers that have adopted each security mechanism.
Overall, we can infer from these results that an easy-to-deploy security mechanism has a high adoption rate.
Setup cost is also key to adoption of security mechanisms
Next, we examined the relationship between setup difficulty and the percentage of security mechanisms adopted.
Table 3 shows how we defined our evaluation indicators, with 1 being easy to set up and 3 being difficult. The more types of servers we need to set up, the more scores we add.
Third-party intermediaries represent something that cannot be completed by a single DNS resource record or server configuration, for example, the coordination of parent-child zones in DNSSEC. It needs to be validated by multiple organizations, hence the score of 3.
| Number | Description | Point |
| 1 | DNS resource records need to be configured. | 1 |
| 2 | DNS server configuration needs to be changed. | 2 |
| 3 | Mail server configuration needs to be changed. | 2 |
| 4 | Web server configuration needs to be changed. | 2 |
| 5 | A third-party intermediary is required. | 3 |
Table 3 — Ease of set up score for DNS configurations (1 being easy to set up and 3 being difficult).
Finally, we defined the setup difficulty level of each security mechanism (Table 4).
Setup difficulty DNS Security Mechanisms
| Mechanisms | Indicator Number | Difficulty Level | ||||
| 1 | 2 | 3 | 4 | 5 | ||
| SPF | 1 | 1 | ||||
| DNS Cookies | 2 | 2 | ||||
| DMARC | 1 | 2 | 3 | |||
| CAA | 1 | 2 | 3 | |||
| MTA-STS | 1 | 2 | 2 | 5 | ||
| TLSRPT | 1 | 2 | 2 | 5 | ||
| DNSSEC | 1 | 2 | 3 | 6 | ||
| DANE | 1 | 2 | 3 | 6 | ||
Table 4 — Setup difficulty level for each DNS security mechanism.
Figure 1 shows a scatterplot of the setup difficulty and the adoption rate, with a logarithmic axis owing to the significant difference between SPF and other security mechanisms. Logically, the lower the setup difficulty, the higher the adoption rate. This observation suggests that the key to increasing security mechanisms’ adoption rate is lowering the setup cost.
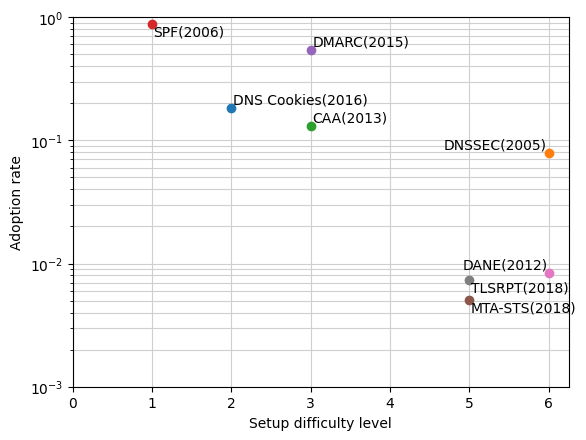
HTTPS’s rapid adoption in recent years lends itself to this theory, particularly the establishment of Let’s Encrypt, which has made it free and easy for anyone to generate/install TLS certificates.
Simultaneously, web browsers changed to show a negative security indicator for websites that do not deploy HTTPS. These facts would have motivated web server administrators to actively adopt HTTPS.
Contrary to this DNSSEC has been noted as difficult to operate flawlessly, even for large and well-known companies, with communication failures from DNSSEC mismanagement still occurring regularly.
As more services like AWS’s Route 53 support DNSSEC, it will become easier for ordinary domain name administrators to use DNSSEC in the future. If these security mechanisms are made readily available to ordinary domain name administrators, the DNS security mechanisms’ adoption rate will increase.
DNS security is worth the effort
We recommend that domain name administrators should regularly review security mechanisms’ settings to make sure they are correctly configured for DNS servers, web/mail servers, and TLS libraries they manage and take note of any changes and operational software emergence.
You can read more about our study in our upcoming paper ‘Measuring Adoption of DNS Security Mechanisms with Cross-Sectional Approach’, which we will be presenting at the IEEE Global Communications Conference: Communication & Information Systems Security (Globecom 2021 CISS).
Masanori Yajima is a graduate student at Waseda University, Tokyo, Japan. He is interested in the security of the DNS ecosystem and Internet measurement.
Discuss on Hacker NewsThe views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.
