
A recent study by Cisco shows cyber incidents, particularly malware, have cost more than half (51%) of 3,700 small and medium-sized businesses (SMBs) in the Asia Pacific region USD 500,000 or more in the last 12 months.
SMBs indicated they were most prone to malware attacks (85%) followed by phishing (70%) and DNS tunnelling (68%). As a result of these incidents, malicious actors are getting their hands on valuable data including customer information (75%), internal emails (62%) and intellectual property (61%).
SMB networks are the first step to larger partners’ networks
The report notes that attackers’ interest in SMBs is likely because of the ‘perceived notion amongst the hacking community that SMBs are relatively weaker on the cybersecurity front compared to large organizations, making them an attractive target.’
The authors go on to note how attackers are not just interested in attacking SMBs but are interested in using their networks as a gateway to larger partner corporations that SMBs are connected to. ’The hope hackers have is that if they are able to infiltrate a particular SMB’s network, they may be able to use that as a launch pad to then access the network of a larger corporation that this SMB may be working or carrying out digital transactions and digital communications with.’
Such ‘supply chain’ attacks attributed to 40% of successful attacks in the region in 2020 and are projected by some agencies to quadruple by the end of 2021.
Asia Pacific organizations are getting better and more proactive at detecting compromises in their own network
Importantly, these risks are not lost on SMBs with four out of five that participated in the Cisco study having recently improved their security posture by carrying out scenario planning and/or simulations for potential cybersecurity incidents, and having a response plan in place. Also, 82% have a recovery plan ready to roll out if needed.
The effects of such proactivity also show in other studies. According to the FireEye Mandiant investigations M-Trends 2021 report, organizations in the region are getting significantly better at discovering compromises internally, as opposed to being notified by external sources such as law enforcement.
The percentage of internally detected compromises increased from 27% in 2019 to 52% in 2020, comparable to Europe, Middle East and Africa (EMEA).
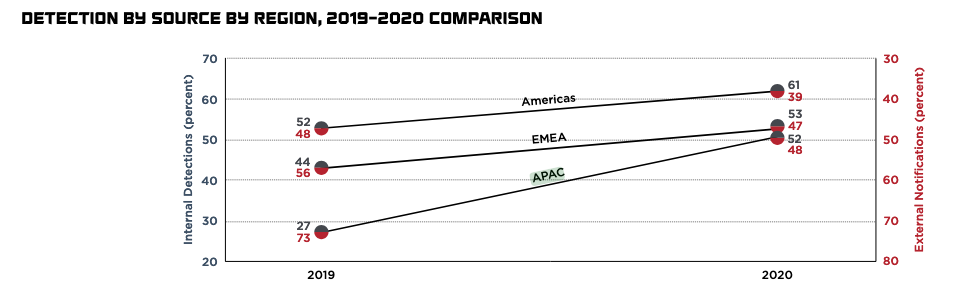
According to the report, this trend of ‘organizations detecting the majority of intrusions within their environments is in line with the overall trend towards increased internal detection observed over the last decade,’ and ‘shows a continued dedication to the expansion and enhancement of organic detection and response capabilities.’
Dwell time has fallen 90% since 2017
While the trend of organizations taking a more proactive approach to monitoring their networks for vulnerabilities and compromises is promising, the speed at which they are detecting these is a work in progress.
The median ‘dwell time’ — the time that attackers penetrate an organization’s network until the time they are exposed — for internal detection in the Asia Pacific region rose from 18 days in 2019 to 33 days in 2020, almost triple the global median for internal detection in 2020 (12 days). However, this figure is nearly a 90% improvement from 2017, which was nearly a full year (320 days)!
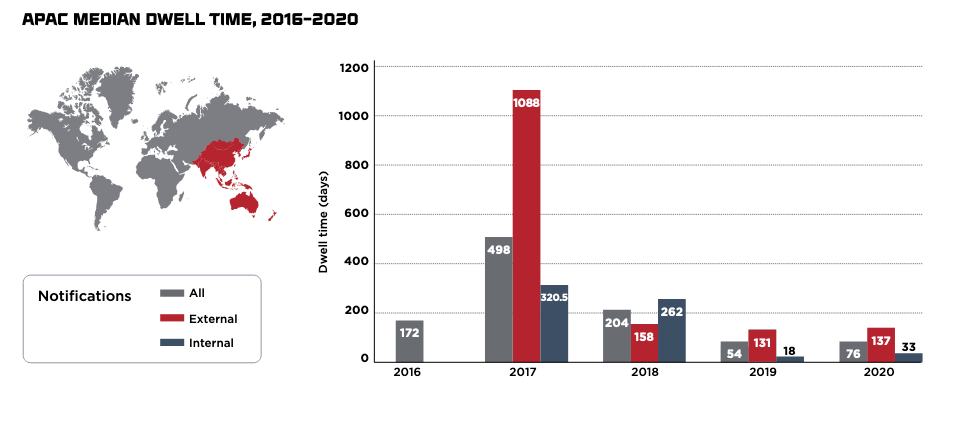
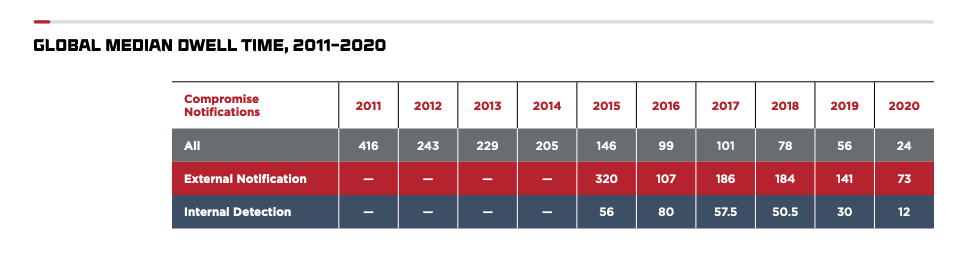
Reducing dwell time is important as it gives attackers less time to embed themselves and/or move within a network, thereby reducing the likelihood of stealing sensitive or critical data. However, it is a complex challenge, particularly for SMBs that tend to not have the resources available, particularly dedicated staff to proactively monitor for intrusions, and instead rely on automated systems.
But it is not an insurmountable challenge as we’ll see in our 2021 Network Security Week Series on threat hunting.
How threat hunting can help
Threat hunting has grown in popularity in the past decade as organizations of all sizes have come to experience that sitting and waiting for the fallout of a security breach can be far more costly than taking a proactive approach to monitoring and finding these breaches.
‘Threat hunting is the human-driven, proactive and iterative search through networks, endpoints, or datasets in order to detect malicious, suspicious, or risky activities that have evaded detection by existing automated tools.’
Hunt evil – Your practical guide to threat hunting, via threathunting.net
88% of the 3,000 IT leaders from 13 economies who participated in the VMware Carbon Black 2020 Global Threat Report acknowledged that threat hunting had strengthened their company’s defences against cyberattacks and found malicious activity that they would not normally have found.
While there are no definitive figures on how much money implementing threat hunting can save an organization, one analyst calculated that it could save an average business upwards of USD 400,000 annually. This doesn’t consider the indirect costs associated with reputational damage, competitive advantage and/or lawsuits that have transpired from the attack.
In this series, we will showcase some of the simple, open-source resources available to help you get started, and importantly, show how to use them. While this is only scratching the surface — The Threat Hunting Project is a great place to continue learning more about the subject — we hope it will allow you to discuss the merits of incorporating it within your security posture and possibly trial it.
As always, we welcome feedback on what you’d like to learn more about and future series ideas we can curate on the APNIC Blog.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.
