
Log records are normally produced by any information system to perform monitoring during normal operations and for troubleshooting in case of technical problems.
Log information is equally important for retaining the security of an information system, as security-relevant events are recorded and can later be monitored for unusual patterns, which may indicate an attack attempt. Examples include log on and log off, startup and shutdown, network service access, network filter rule application and storage access.
Log records may also contain valuable information about a system that a potential attacker intends to compromise. If attackers are able to successfully compromise a system, they are also able to tamper with log records, potentially hiding their traces.
This makes forensic analysis extremely difficult, as no reliable data source about system behaviour immediately before the attack is available to a security analyst performing an incident investigation. Therefore, log information should be appropriately protected.
The challenge of protecting logs on board an aircraft
There are multiple possibilities to protect log details, each of which have their strengths and weaknesses per application. At Airbus, we looked for a solution that could also be applied to resource-constrained systems subject to special operating conditions, such as airborne communications systems.
In our search for an appropriate solution, we came across fundamental work done by our internal cryptography experts together with academic partners who developed a cryptographic scheme that guarantees log archive-forward integrity and confidentiality based on clear assumptions and a well-defined threat model.
This scheme provides tamper-evident logging that adequately protects log records of an information system and additionally provides a sensor indicating attack attempts. It achieves this by authentically encrypting each log record with an individual cryptographic key used only once and protects the integrity of the whole log archive by a cipher-based message authentication code.
Each attempt to tamper with either an individual log record or the log archive itself will be immediately detected during log archive verification. Therefore, an attacker can no longer tamper with log records without being detected.
But the question remains: How to put such a scheme into practice without impairing the system performance, increasing system integration complexity or creating an additional burden on behalf of the operator?
For example, where and how is log verification performed if the central data collector, in our case an airplane, does not have continuous connectivity. This means that log records will need to be stored on board the airplane until a download can be performed, creating a significant time lag between log record creation and log record analysis — see Figure 1.
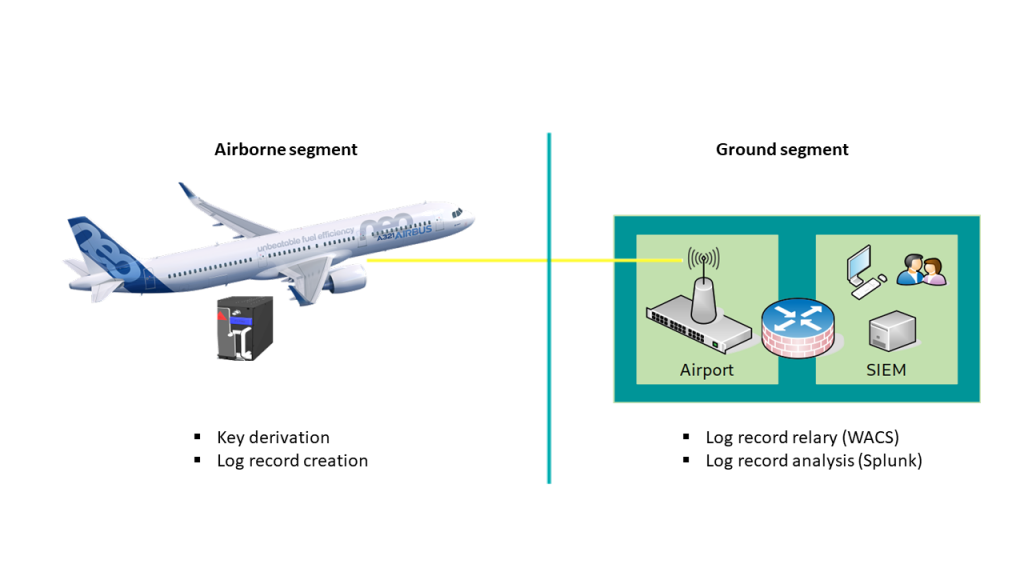
Open-source log protection for everyone
Although the aviation industry traditionally has been more conservative than other industries when it comes to embracing new technologies and methods, the open-source software development model is gaining momentum in the aerospace community as well. Thanks to this model, an efficient solution for the implementation of an effective log archive protection was finally found in the form of syslog-ng — an open-source implementation of a system logging service.
In addition to the standard RFC 5424 capabilities, it provides enhanced features for input and output as well as capabilities for log-message filtering, rewriting, and routing. It also features a plugin mechanism that allows for extensibility by supplying additional functions in the form of a suitable module. Furthermore, it can be used as a drop-in replacement for existing system log daemons on most modern operating systems.
The log archive protection was implemented as a module in syslog-ng, see Figure 2.
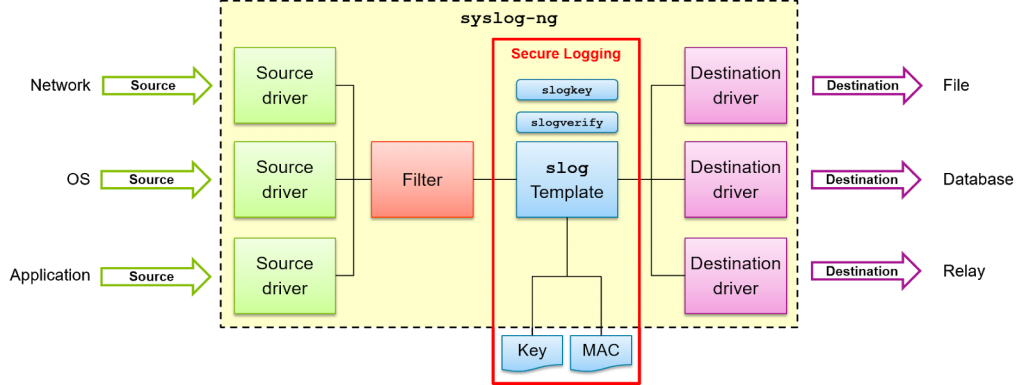
Cryptographic operations use OpenSSL. The configuration mechanism relies on the standard syslog-ng facility. This allows for easy integration into existing installations of syslog-ng, as in the case of the Airbus airborne communication system. Only a single line needs to be added to the configuration file in order to activate log archive protection. Furthermore, the performance impact is minimal where special hardware instructions supporting cryptographic operations are available.
The principle of log archive protection is not limited to airborne applications but can be employed in any information system, from small embedded devices to large cloud-based environments. The code is freely available on GitHub.
We are currently in the process with the syslog-ng core developers to integrate our module into the mainline syslog-ng source tree. Once this is finished, everyone installing syslog-ng will benefit from log archive protection.
To learn more, see the presentation we gave at FOSDEM earlier this year, leave a comment below, or email us.
Stephan Marwedel is working as a product security engineer for avionics systems at Airbus in Germany.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.
