
Every so often, cybersecurity breaches make the news. Some that you may have read about over the last two years include:
- June 2017: Ransomware attack on Maersk
- June 2018: NotPetya attack on Saint-Gobain
- March 2019: LockerGoga attack on Norsk Hydro
- May 2019: RobinHood attack on Baltimore City
The common theme across these compromises was that they were all attacks on Microsoft’s Active Directory (AD).
Although it’s not a new target, attacks on AD have expanded in recent years as it becomes an increasingly important system for managing permissions and access to networked resources. Fortunately, for admins and users, this has coincided with a greater awareness of monitoring and mitigating against cyberattacks.
In this post, I will outline what we know about AD attacks and how to protect against them.
Ageing Active Directory design
A key reason why AD has become a significant target is tied to our old way of thinking about AD and security.
Many current AD setups were designed ten or more years ago. At that time, AD breaches existed, but only a small group of people were able to exploit it. These antiquated AD designs only focused on the:
- Directory information tree
- Delegation model
- Group Policy Objects (GPOs) structure and accounts management
The security of the design was important, but it was managed through the delegation prism and not the pure AD sanity check angle.
A common mistake stems from how IT teams think about operating systems migration (moving from Windows 2008 to 2016, for example) and ignoring the entire AD design. Never mind the Windows version of your domain controllers; if the global design is permissive, the latest version of Windows will not save you.
To address these and other misconceptions and misconfigurations, Microsoft created a best practice document providing great advice on configuring AD — the Active Directory Tier Model Design.
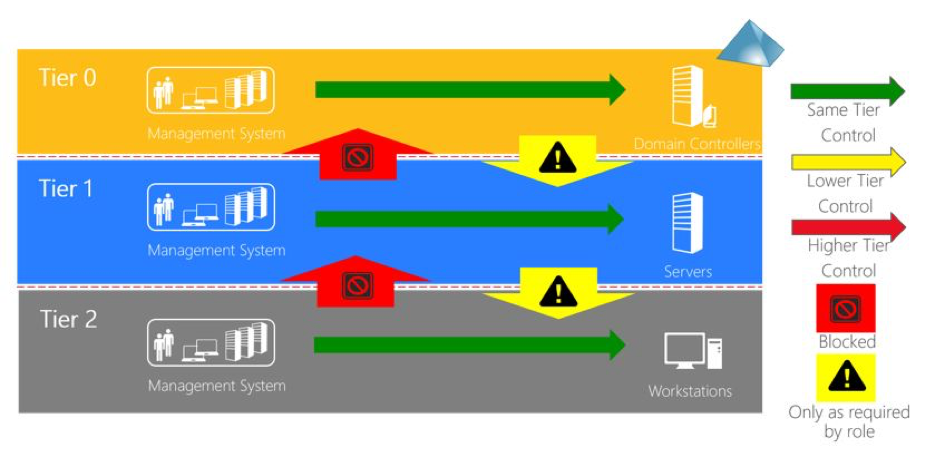
How is AD attacked?
Before developing any cybersecurity mitigation techniques you need to understand the methods of attack and the tools attackers are using. In the case of AD attacks there are two common targets leveraged by attackers:
- Windows systems vulnerabilities.
- AD misconfigurations.
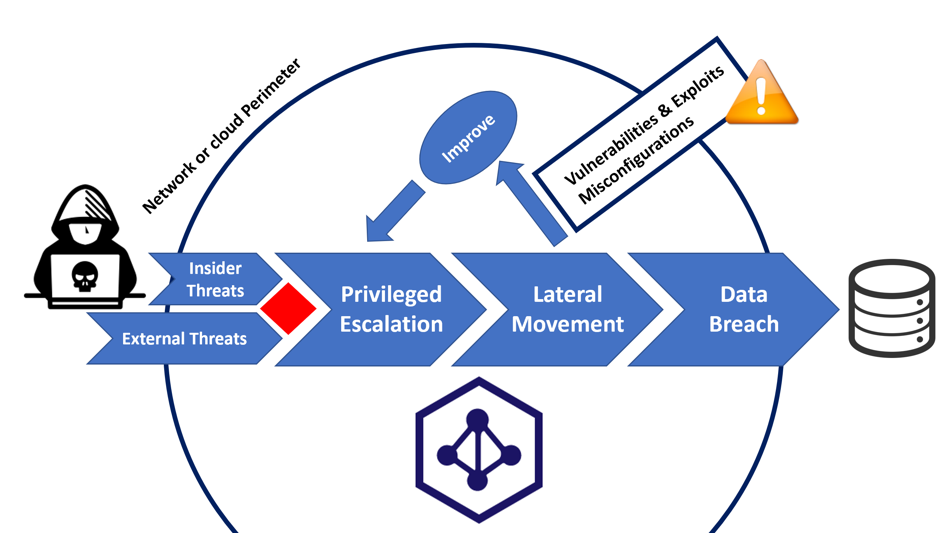
Vulnerabilities and exploits
Whatever the system (classic operating system, firewall, router), it is relatively simple to manage for vulnerabilities. Several tools and solutions can help you to scan your network and detect vulnerabilities. This is important to consider because it can give you good visibility on your patching priorities. Many of these solutions are using the public CVE database such as MITRE or NIST.
The more Windows systems you have, the more important the vulnerability scanning feature becomes — this is mainly because a lot of malware and ransomware are targeting Windows systems.
There are various paid for and open source vulnerability scanners on the market, such as Retina Network Security Scanner, Nessus and OpenVAS. In our opinion, there isn’t a huge difference between them, but some features are interesting to highlight. These include their ability to:
- Integrate with an existing Security Information and Event Management (SIEM) solution.
- Associate the number and nature of detected vulnerabilities with a Risk Score.
- Create a link between the Risk Score and the Privileged Account Management (PAM) platform: in this scenario, the systems login requirements will evaluate your authentication method considering the Risk Score.
Misconfigurations
It’s no easy task for a large organization to check the entire AD configuration. This is due to the following root causes:
- Lack of real AD cybersecurity competencies in the market.
- AD is based on a multi-master replication technology.
- The high number of changes made in AD on a daily basis.
- The difficulty for many IT managers to truly understand the production risks associated with AD misconfigurations.
Because of this, several large organizations don’t really manage their AD security, and, as such, a multitude of misconfigurations persist.
AD misconfigurations significantly increase the risk of malware or APT attacks. It’s urgent for these organizations to create remediation plans before they are hacked.
Only select solutions have the ability to catch a clear overview of the actual AD configuration and receive key information about how to fix the misconfiguration. Other important capabilities include true real-time overview of AD changes and a dashboard to follow the different actions made in AD. Continuous AD attack detection and remediation (threat hunting) are crucial to ensuring an hardened AD security posture.
Which tools are used by attackers to compromise your AD?
There are several existing tools that are useful for attackers or red teams. This is a non-exhaustive list of the main ones.
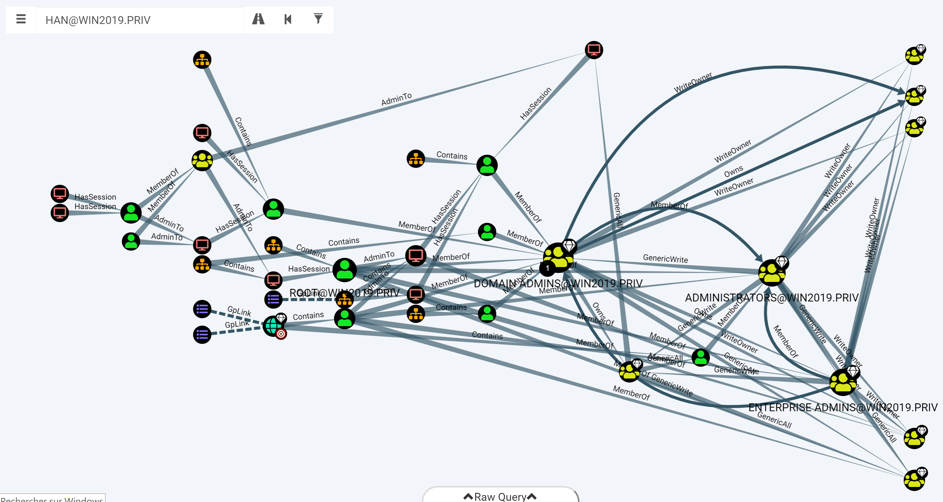
BloodHound
BloodHound is a fantastic tool that can retrieve all the information from AD using a classic user account (non-privileged user account) and inject the collected data in an easy-to-use dashboard. The BloodHound dashboard highlights the preferred attack paths and makes the red team’s job easier to analyse the target.
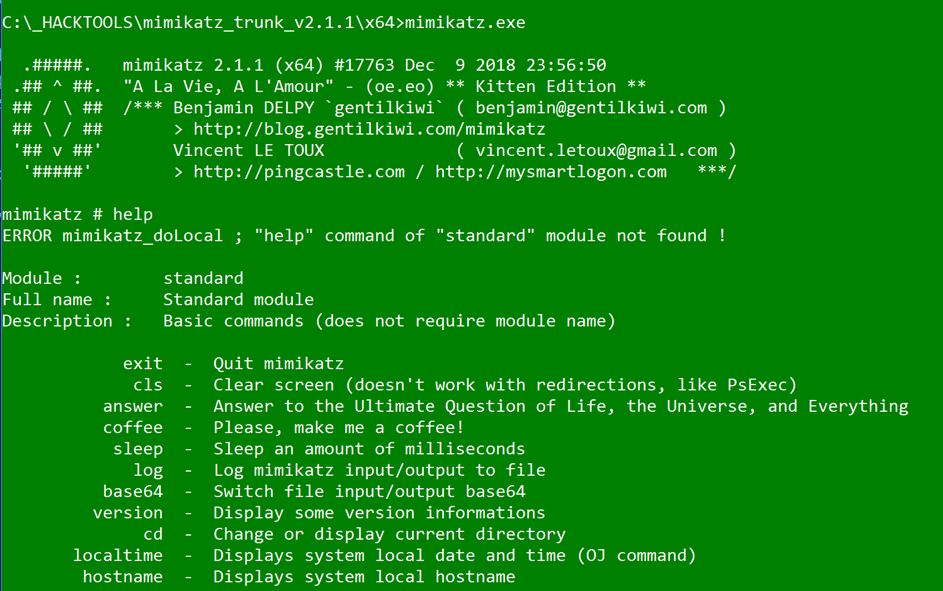
Mimikatz
Mimikatz is a super toolkit to use when you want to perform attacks from the workstation and use Kerberos’s weaknesses. It will help facilitate classic attacks such as pass the hash or pass-the-ticket, but it will also bring some advanced features hidden from the blue team monitoring such as the DC-shadow method.
Metasploit
Metasploit brings together some micro-tools to build a massive toolkit for the red team. You can use Metasploit to explore vulnerabilities and to perform specific AD attacks, as well. It can help discover the attack methods used by attackers to contaminate your network.
What can I do to protect my AD?
Of course, the answer to this question depends on your organization. However, you can use some tips and tricks that are still relevant for any medium or large companies. We recommend the following actions:
- Perform an AD security audit by a specialized consultant.
- Take advanced training on AD security. In any case, you will need to be trained to be fully operational and understand the details.
- Evaluate software solutions allowing you to greatly improve your AD security level. Start with the Alsid and Retina solutions to cover misconfigurations and vulnerabilities.
- Test different attack tools to check how attackers can use your weakness — understand how your enemies’ weapons can help you better understand the attack models: BloodHound, Mimikatz, and Metasploit.
- Implement a plan for continuous improvement of your AD infrastructure.
- Regularly perform targeted intrusion tests on AD via an external firm or via your internal red team.
Sylvain Cortes, Security Evangelist at Alsid.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.

Great to see someone doing something with BloodHound and the other variants which is a great idea but has serious challenges when it comes to real world use.