
With Moore’s Law slowly reaching its natural end, perhaps it’s also time to bid a fond farewell to another concept that we in the industry continually use to sell hardware, that of the ‘killer app’.
It has, for as long as most of us can remember, been the connection to the user which makes the underlying hardware indispensable. It’s been the buzz maker. It’s been the features we’ve been convinced we can’t live without. It’s been the algorithm which launches a thousand start-ups. (This is fun, but I’m sure you get my point.)
We currently find ourselves in an unprecedented upgrade of the global Internet addressing protocol, wondering what it is about this protocol that the world cannot live without. What will create the buzz? Its features have been backported to IPv4. Its value proposition has been muted by the transitional mechanisms of DHCP, NAT and Happy Eyeballs. What will move the needle of adoption?
IPv6, sans killer app
Much has been written about the lack of a killer app for IPv6 and for good reason. With 2.7 million apps in the Google Play Store (Figure 1) and 1,434 apps being added to the App Store every day, it’s no surprise that that IPv6 hasn’t found its life partner.
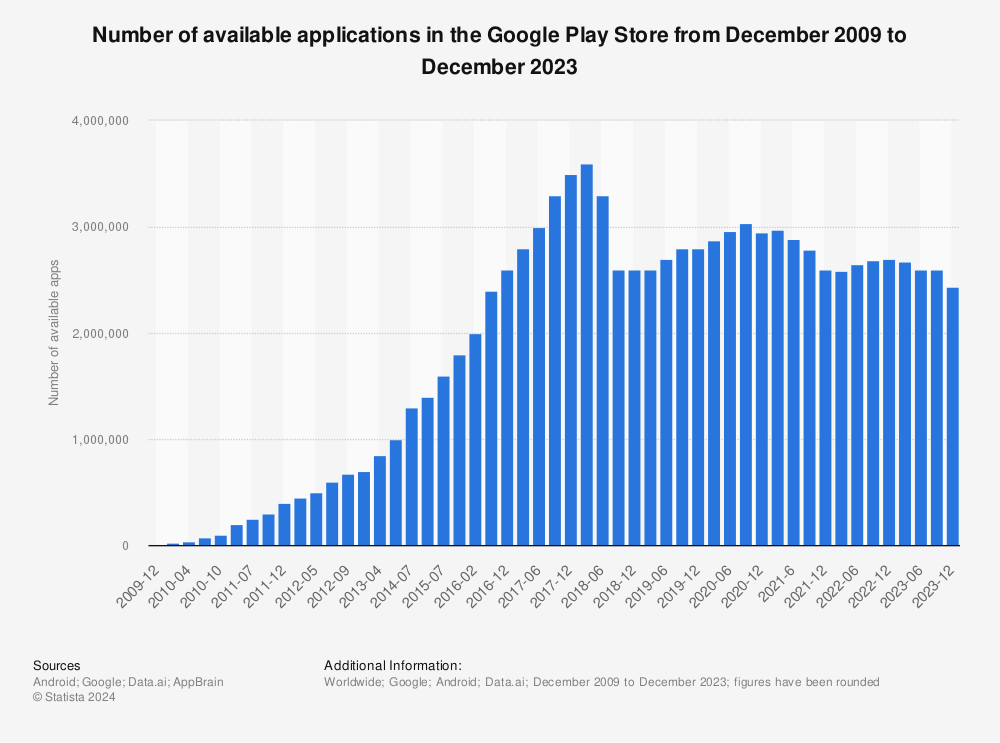
Figure 1 – Number of available applications in the Google Play Store from December 2009 to June 2019. Source: Statista.
The explosion of the global code base doesn’t bode well for lonely IPv6, releasing a combined total of 7,574 Android (6,140) and iOS (1,434) apps every day. The lifespan of an enterprise mobile app is estimated to be 14 months before it is re-written. There are just too many apps and they don’t last long.
The extreme volume and limited lifecycle of apps require that we redefine the concept of the value of the delivery mechanism for technology. The vertical definition of the value we’ve relied on for so long is no longer serving us. It’s time to go horizontal. It’s time to rethink how technology pitches its value proposition to its intended audience, whether it’s consumer or enterprise.
We’ve gone beyond thinking in features to thinking in solutions. For IPv6, let’s take the next step and begin thinking in terms of the Internet’s Prime Directive.
IPv6 offers solution to identity scalability
To get the conversation started, I found a throw-back description of the Internet’s Prime Directive: communicate + exchange + collaborate = exponential results.
Communicate + Exchange + Collaborate = Exponential results. Now more then ever we need to do so – for the 13 years / 10 years publishing
— Carole Guevin (@netdivermag) February 10, 2009
We, as a community, need to communicate the value IPv6 delivers across applications, infrastructure and solutions. IPv6 has many characteristics. However, I would like to focus on the characteristic which is fundamental to fulfilling the sum of the Internet’s Prime Directive: exponential results, which, for me, relates to identity.
Identity is the element necessary for delivering the value propositions of scalability and security. The sheer volume of IPv6 restores the unique device identity pillar of the Internet paradigm, compromised for so long.
Unique identity facilitates scalability. Knowing that the entity knocking on your firewall is the same entity who initiated the transmission is critical to perimeter penetrating security.
The Internet’s role as the backbone of the global economy was not the original intent of its creators and the IP address numbering system created reflects this. The explosion of connected devices is continuing unabated. The anticipated expansion of Internet use resulting from technologies specifically designed to induce expansion, such as 5G, IoT, Blockchain and Cloud, requires sufficient unique identifiers to meet the demand. The only identity enabler for this extreme scalability in connectedness is IPv6 and its unfathomable number of unique identifiers.
When individuals come to my home or business, I want to know that whomever shows up is invited or has a standing invitation to drop by. They’ve never broken in, stolen anything or left trash for me to find later. I expect them to enter the specified entry door, correctly identify themselves and conduct their business in a respectful manner.
I don’t invite flash mobs. Mobs are unruly; they break things and leave trash. Unknown individuals attach themselves to mobs as they travel. I don’t like mobs at my door and I don’t like them traversing the Internet by way of NAT/CGNAT.
I want to know who is knocking on my door and my firewall. Identity is a primary element to a perimeter-penetrating security strategy and IPv6 is the only enabler of adequate unique identity.
Perhaps it’s time to give IPv6 a focused dating pool by reconnecting with the Internet’s Prime Directive of exponential results — enabling us all, both enterprise and consumer, to live long and prosper.
E. Marie Brierley is the Founder and CEO of Saatvik Advisors, an IPv6 consulting firm.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.
