In a previous post, I analysed IP address prefixes that would become unreachable in a RPKI Route Origin Validation (ROV) environment in which routers discard RPKI INVALID BGP announcements (as there is no alternative route available) — we will call these prefixes ‘RPKI-unreachable’ from now on — and used a number of prefix-origin pairs as the primary metric.
This time, instead of using the number of prefixes, I take the actual prefix size into account. I measure the amount of RPKI-unreachable address space in IPv4 and IPv6 and plot this on a global map.
Counting unique IP addresses only
Since the same IP address space can be covered by multiple BGP announcements, I make sure I count only unique (non-overlapping) unreachable IP address space. This is best illustrated by the following example.
115.168.0.0/14
115.168.0.0/17
115.168.37.0/24
The above three BGP prefix announcements are all INVALID (see here); but since all of them are covered by the first BGP announcement, I collapsed them into one entry (the first one) to avoid counting the same IP address space multiple times.
Breakdown by RIR (IPv4)
In total, there is around a /11 of IPv4 space (equivalent to 8,755 /24s) that is unreachable in a RPKI ROV environment.
If I break them down by RIR you can see that the APNIC region is the most affected. (The previous analysis by prefix-origin count suggested that the LACNIC region is most affected.)
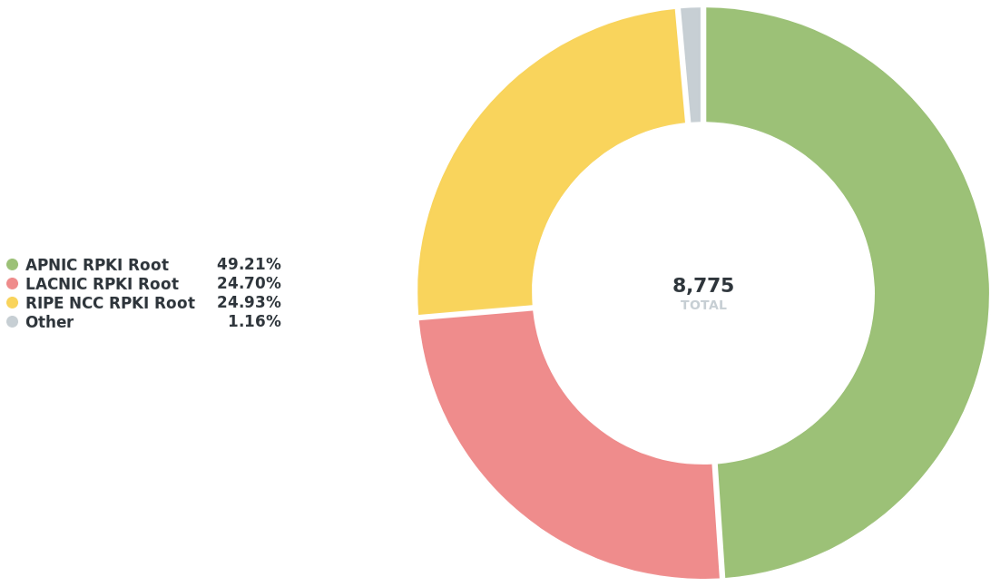
Figure 1 — Distribution by RIR of IPv4 space that would become unreachable in a RPKI ROV environment.
Breakdown by RIR (IPv6)
In total, there is around a /27 of IPv6 space (equivalent to 3,096,954 /48s) that is unreachable in a RPKI ROV environment.
In the world of IPv6, the most unreachable IP space (>61%) is located in the RIPE region.
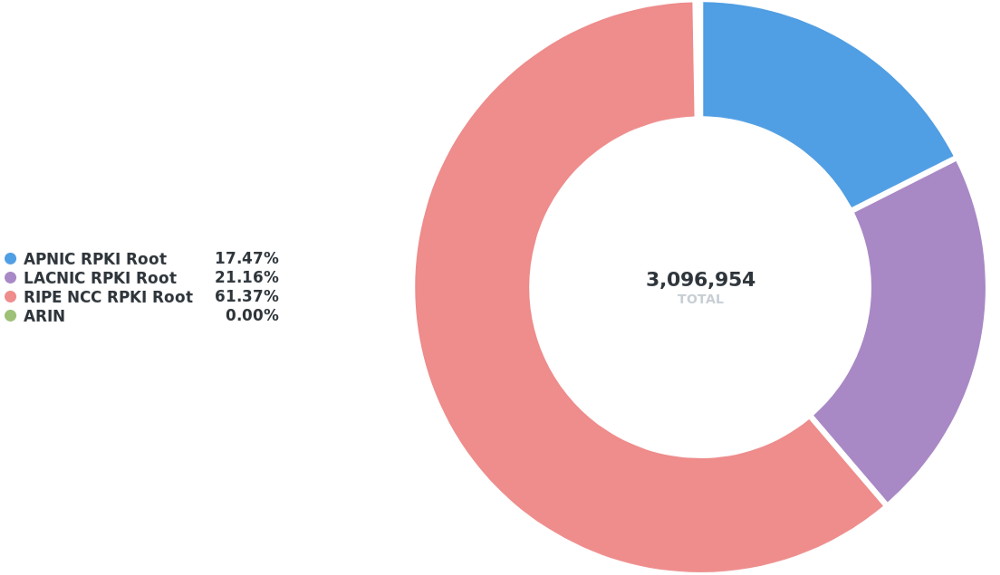
Figure 2 — Distribution by RIR of IPv6 space that would become unreachable in a RPKI ROV environment.
RPKI-unreachable IPv4 networks by economy
I used RIPEstat to map the announcing Autonomous System (AS) (not the IP address) to an economy.
More than 44% of RPKI-unreachable IPv4 space is located in China (21 prefixes were responsible for this at the time of the analysis). Other economies with a significant fraction of RPKI-unreachable prefixes are Argentina and Colombia.
Since ARIN was basically invisible in both of the above analyses (Figure 1 and 2), I did not expect the US to show up in the per economy distribution. However, after taking a closer look, it turned out that most of the time where an ASN’s geolocation indicated it was in the US, the issuing RIR was actually LACNIC (for IPv4).
Geolocation is never perfect, so take the maps bellow with a grain of salt.
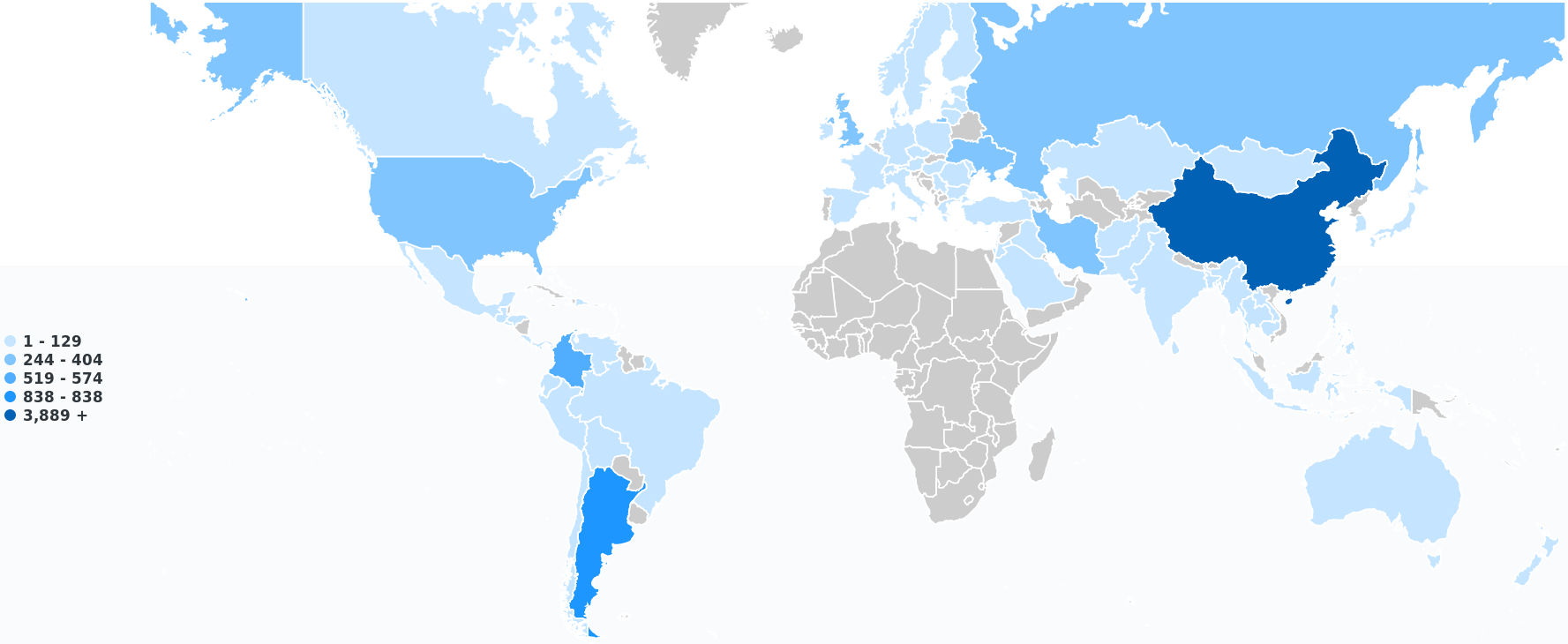
Figure 3 — Geographical distribution of IPv4 space (in /24 equivalent) that would become unreachable in a RPKI ROV environment.

Figure 4 — Top 10 economies/regions for IPv4 space that would become unreachable in a RPKI ROV environment. Note: ‘EU’ represents additional ‘European’ allocations that are not associated with a particular EU economy.
RPKI-unreachable IPv6 networks by economy
Iran, Venezuela, the US and Australia have a significant portion of RPKI-unreachable IPv6 address space.
For the US, most of the time, the RIPE NCC is the issuing CA (explaining the low RIR fraction of ARIN again).
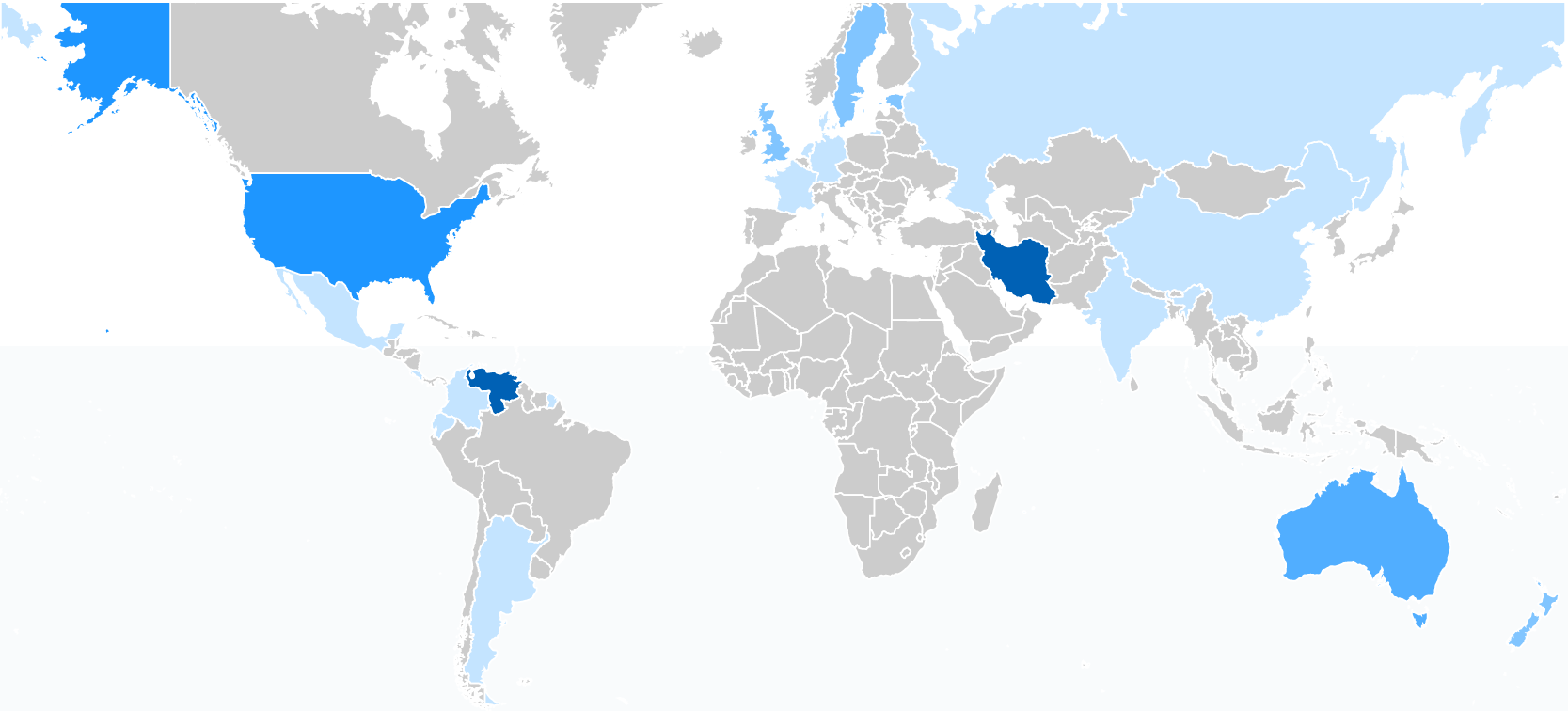
Figure 5 — Geographical distribution of IPv6 space that would become unreachable in a RPKI ROV environment.
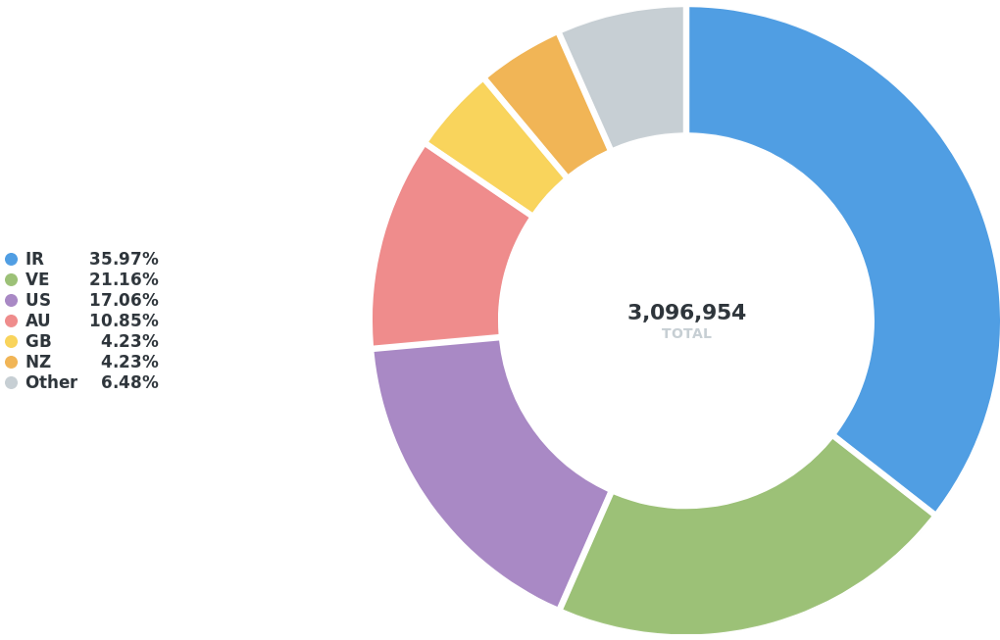
Figure 6 — Top 6 economies for IPv6 space that would become unreachable in a RPKI ROV environment. Note: ‘EU’ represents additional ‘European’ allocations that are not associated with a particular EU economy.
RPKI-unreachable IPv4 networks by (announcing) AS
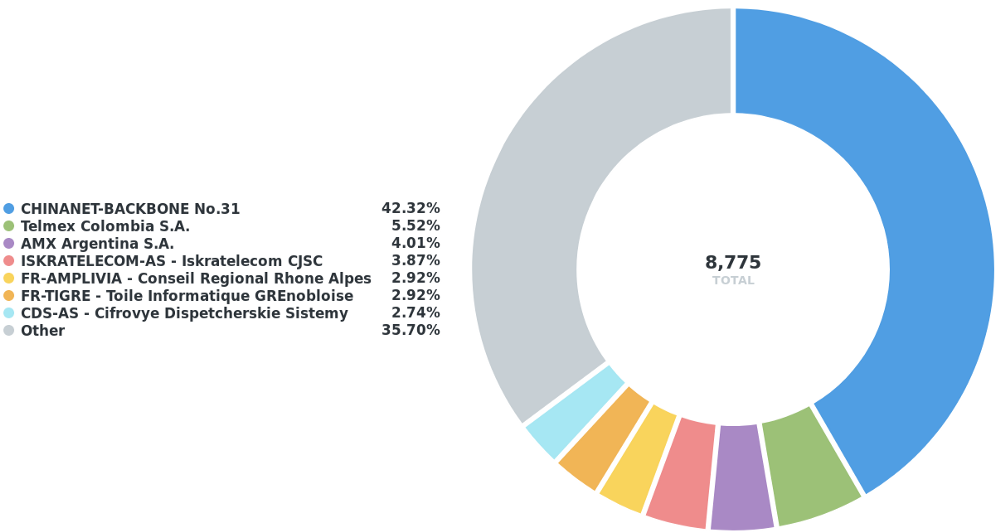
Figure 7 — ASes with the largest fraction of IPv4 space that would become unreachable in a RPKI ROV environment.
RPKI-unreachable IPv6 networks by (announcing) AS
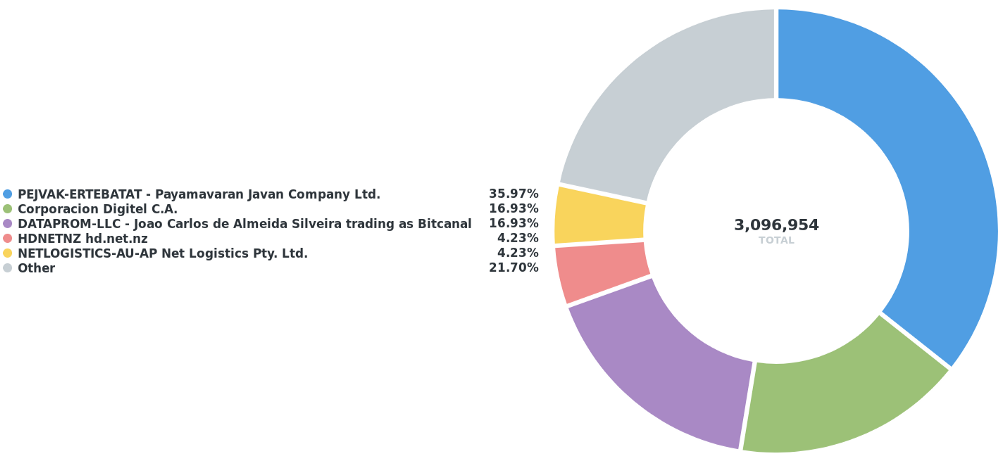
Figure 8 — ASes with the largest fraction of IPv6 space that would become unreachable in a RPKI ROV environment.
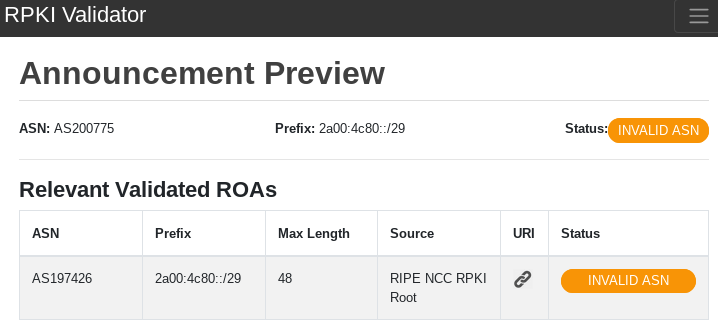
The cautious reader will note that Bitcanal ranks quite high, however, on closer inspection (Figure 9) I discovered that they messed up their ROAs — AS200775 and AS197426 both have the same name (Bitcanal).
Figure 9 — Bitcanal: Invalid prefix (2a00:4c80::/29) announced by AS200775 but ROA authorizes only AS197426.
Future work
I currently count partial INVALIDs (example shown below) as complete INVALIDs, which causes a slight false-positive rate in the number of unreachable IP space. Currently the following example (Figure 10) is counted as two unreachable /24 blocks, but it should be counted as one unreachable /24 block.
Figure 10 — Two unreachable /24 blocks, which I propose should be counted as one unreachable /24 block to reduce false-positives.
For network operators
If you are a network operator and would like to find out if the reachability of any of your prefixes are affected by RPKI misconfigurations, visit the RPKI Observatory.
Note that Cloudflare has announced they will enforce RPKI ROV by the end of 2018, which means that affected networks will not be able to talk to Cloudflare networks unless the BGP announcement or ROA is corrected.
Adapted from original post, which appeared on Medium.
Nusenu cares about Privacy Enhancing Technologies and likes Internet Metrics. He came across RPKI and routing security when measuring how resilient the Tor network is against BGP hijacking attacks.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.