It is safe to say that news of BGP prefix hijacks, either by an attack or by ‘fat fingers‘, appear with greater regularity than Internet network operators would like. Besides the impact of the hijack itself — service unavailability, theft, or impersonation — news of a hijack is reliably followed by a storm of opinion about what a network operator should, could, or ought to have done about it.
A recent survey set out to discover exactly what network operators are doing about prefix hijacks by questioning 75 network operators from across the globe.
The survey revealed that 40% of network operators surveyed had been victims of BGP prefix hijacks in the past, with most of those attacks lasting an hour or more. A majority of the operators surveyed said that they expect hijack incidents to have a severe impact.
Despite confirming the potential seriousness of hijack events, the operators surveyed did not appear to consider RPKI to be a practical measure in preventing such incidents. 71% of respondents had not deployed RPKI in their network, citing the financial and technical cost of deployment, especially given that it relies on broad global adoption for its effectiveness.
The survey found that most operators’ mitigation strategies revolve around filtering, extensive peering, and in the event of a hijack incident, contacting the offending network’s operator and announcing more specific routes (de-aggregating).
The researchers hope that the information gathered from the survey will inform “the design and implementation of new concepts and methodologies, as well as more secure inter-domain routing protocols in general”.
The survey
A team of researchers from FORTH-ICS and CAIDA developed the survey, which focused on the following areas:
- Operator awareness of BGP prefix hijacking attacks
- Defences currently in use against BGP prefix hijacking
- Operator willingness to adapt new defence mechanisms
- Hindrances to the deployment of defences
Impact
The survey was able to quantify the seriousness of the threat of BGP prefix hijacking, discovering that 40% of respondents had been victims of a hijack or hijacks in the past. Affected operators reported that 57% of hijacks lasted an hour or more, and 25% lasted longer than a day.
76% of the operators surveyed said that they expect BGP hijack attacks to have a “severe and lasting impact” of several hours or more.
Defence mechanisms
The survey found that 71% of network operators have not deployed RPKI in their networks. The most common proactive measures in use were found to be route filtering, extensive peering, and de-aggregation.
61.3% of the operators surveyed rely on a third-party service to detect and notify them when their network is affected by a prefix hijack.
Reactive measures
A majority of operators said that they would respond to a prefix hijack by announcing more specific prefixes (de-aggregating) and would contact the offending network to report the event.
The researchers noted that these approaches have significant shortfalls, for example, “de-aggregation is not efficient when a /24 prefix is hijacked (due to upstream filtering), and contacting network operators is usually done manually and thus adds significant delay to the mitigation process”.
The survey results rank the importance of defence system characteristics according to the network operators.
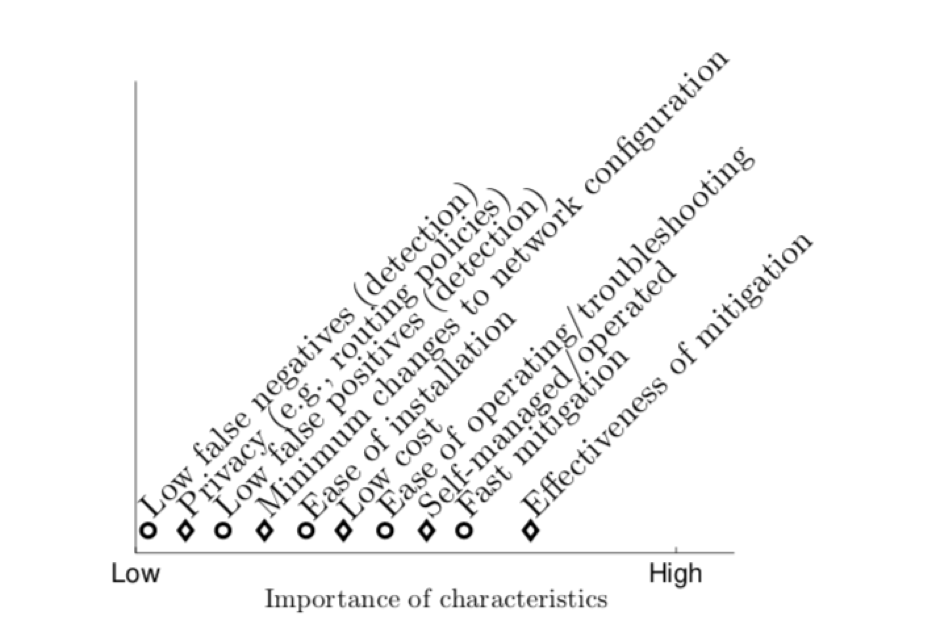 Figure 1: Defence system characteristics, ranked in order of importance according to survey respondents.
Figure 1: Defence system characteristics, ranked in order of importance according to survey respondents.
When questioned about their willingness to adopt new mitigation mechanisms, network operators were largely unwilling to outsource this work, citing cost and privacy of information.
Given that the survey confirmed the researchers’ suspicions about the impact and severity of BGP prefix hijacks and gained valuable information about how these attacks are (and are not) mitigated, the researchers hope that this information will “contribute towards designing new defense mechanisms that satisfy the requirements of the operators.”
The survey results were originally presented as an editorial note in the ACM SIGCOMM Computer Communication Review in January 2018.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.
