I had the opportunity to do a three-day Network Security workshop at bdNOG – with a few other colleagues from IIJ, ICANN & and BDCERT. It was the first time for me doing a security training as an APNIC staff member and I definitely had a good time! Especially with the good response that we got from the audience. Thanks everyone!
When teaching security, I find that it is always useful to share with the audience examples of security breaches. Then you can link the lessons learned (or what went wrong) with best practices, controls, RFCs, frameworks, strategies and so on. For example if you are teaching best practices of passwords, it would be useful to show what can happen if systems use weak passwords or if users do not take care of the passwords.
This is where a honeypot could be useful as a teaching tool. Now, a honeypot is not exactly a specific technology but rather a bunch of tools that you can put together to learn about computer security and cyber attacks in general. Obviously you don’t do this on a production system.
So, in our Network Security workshop, I discussed about how the Internet can be a hostile place and therefore you must ‘harden’ your devices and follow some of the best practices out there. To demonstrate, I shared with the audience some observations from my SSH honeypot (aka Kippo) I set up specifically for the workshop a few weeks earlier.
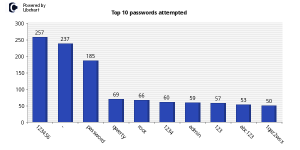
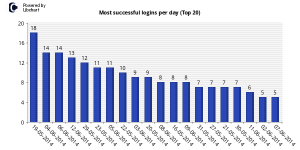
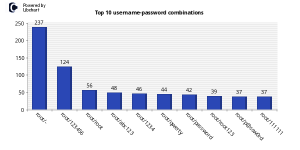
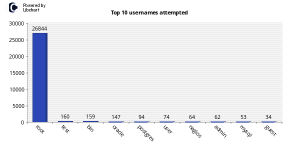
The whole idea was to setup an SSH server with weak credentials (i.e. u:root p:123456) and see what happens. The graph below should be self-explanatory.
Lessons “Learned”
So the following observations were made:
- Once you put a host / server / network appliance on the Internet, attackers can find them (using network scanners etc) and discover the services that are running on them
- Appliances or systems with weak username & password combination can be compromised
- Once attackers gain access to your systems they can do more with the privilege that they have (attack other systems)
The observations above are consistent with what most cyber security lecture tells us:
- Apply access control – who can connect to certain services or computers and from where
- Consider strong passwords or use two-factor authentication on critical systems
- Have an incident response plan. In the event that your systems are compromised so you’ll know how to recover, who to contact, who does what and so on
- Do risk assessment so that you will understand what are the risks and mitigation required.
The best part is that you can also go beyond talking about concepts & observations. You can get your hands dirty can perform analysis on the the ‘artifacts’ collected such as network traffic (pcaps), logs or scripts that the attacker had uploaded on your honeypot. This way the class get to play with relevant tools and will start to have a deeper understanding of the topic being discussed.
If you are keen to learn about honeypots then waste no more time and head over to the the Honeynet Project website. Happy Learning!
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.