
The FBI’s 2023 Internet Crime Report revealed that the Business Email Compromise (BEC) is the second-costliest type of crime tracked by the Internet Crime Complaint Center (IC3). According to the 21,489 complaints received by the IC3, the financial losses amount to USD 2.9 billion.
To protect against BEC, the FBI recommends to:
- Avoid a free web-based email if possible.
- Establish a company website domain and use it to set up company email accounts.
However, as highlighted in a previous APNIC blog post ( ‘Email is getting harder to self-host. Or is it?‘), the configuration of self-hosting emails can be challenging, particularly when dealing with anti-spoofing mechanisms such as DKIM, SPF, and DMARC.
To recap, DMARC encompasses two types of protections for a domain name: Handling policies and reporting systems. When set to p=quarantine or p=reject, handling policies instruct email receivers to treat emails failing the DMARC check (when SPF and DKIM are not aligned) as suspicious or to be dropped. The reporting system allows receivers to send reports on received emails to the email addresses specified within the RUA and RUF tags, either through aggregate reports (usually sent every 24 hours) to the email addresses in the RUA tag or failure reports to the email addresses in the RUF tag. This reporting system helps domain owners detect spoofing attempts and improve their DKIM/SPF configurations, please refer to Figure 1.
In our study on DMARC published in the Proceedings of the 2024 Passive and Active Measurement Conference (‘Spoofed Emails: An Analysis of the Issues Hindering a Larger Deployment of DMARC‘), we scanned 280.3 million active domain names looking for DMARC records and found that only 15.9 million (5.4%) domains adopted DMARC.
Compared to our measurements one year earlier, this proportion represents an increase of approximately 30%. Furthermore, the proportion of domain names with non-restrictive handling policies (p=none) decreased from 67.7% to 55.5% over the same period, which is encouraging — it is recommended that those who wish to apply restrictive DMARC policies start with p=none, use the reporting system to fine-tune their configuration, and then adopt more restrictive policies once they are sure of their setup.
We investigated the policy changes made by domain owners when switching from non-restrictive policies. Specifically, we compared the handling policies of domain names between 2022 and 2023, as shown in Figure 1.
Figure 1 — DMARC evolution between 2022 and 2023.
Overall, the DMARC population is growing, and the trend towards adopting more restrictive handling policies is primarily driven by new DMARC domains. Despite this progress, our measurements showed a slight decrease in the ratio of domain names adopting DMARC and containing the RUA or RUF tags from 43.4% to 42.9% — the influence of aggregate reports on policy modifications remains an open question.
As a consequence, we plotted the evolution between 2022 and 2023 of the handling policy modification or the presence or not of the RUA tags (see below). The first part of the diagram expresses the p and RUA tag modification when the tag was present in the DMARC record and the second when the tag was not present.
Figure 2 — DMARC evolution between 2022 and 2023. Domains having RUA in 2022 with modified p or RUA tags in 2023.
Globally, our comparison indicates that 59% of domain names used to have the RUA tags but this proportion decreased to 47% in 2023. Among the domain names with the p=none policy in 2022, 64.1% changed to p=quarantine, 21.8% moved to p=reject, and 14.1% changed their RUA tag status. Surprisingly, 70% of the domain names that shifted from p=none to p=reject did not have the RUA tags in 2022, 37% of domain names having RUA tag in 2022 with p=none and switched to p=quarantine also abandoned the RUA tag in 2023, and 35.8% of domain names that have toughened their policies did not have a RUA tag, which contradicts the hypothesis that domain names use the reporting system to transition to stricter policies.
Those unexpected observations raise questions. Why would the domain name owner adopt stricter handling policies without knowing the possible impact on their email deliverability? Why would some remove their RUA tags? More specifically, what are the issues in the DMARC reporting system that discourage domain owners from using it?
To learn more about the reporting system usage, we extracted the domain names of email addresses present in the RUA and RUF tags. Interestingly, we found that approximately 29,000 DMARC records contained placeholder email addresses such as ‘address@yourdomain.com‘, ‘me@example.com‘, and ‘youremailaddress@yourdomain.com‘. Nevertheless, as shown in Figure 3, 30% of all email addresses from the RUA or RUF tags belong to five companies: proofpoint.com, reportdmarc.nl, mailinblue.com, agari.com, and dmarcanalyzer.com. These findings suggest that many domain name owners prefer outsourcing the analysis of their DMARC reports to processing them by themselves.
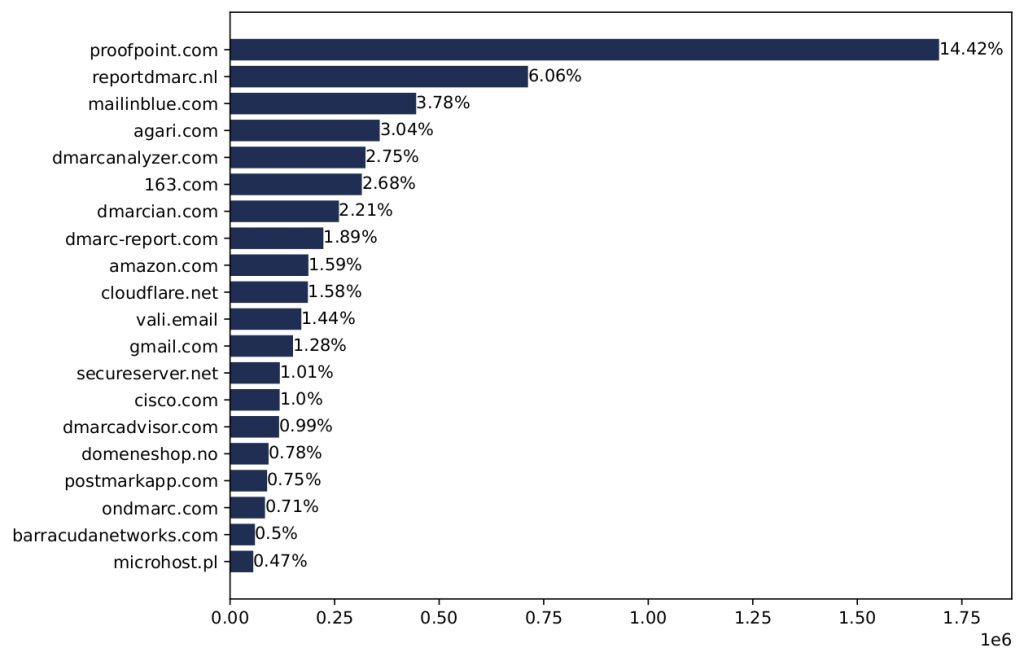
Figure 3 — Registered domain names in the RUA and RUF tags.
When looking at global measurements and related work, it becomes evident that DMARC adoption is on the rise, and restrictive policies such as p=quarantine and p=reject are becoming more prevalent. However, this growth in handling policies is largely driven by newcomers to the DMARC ecosystem. Domain owners do not appear to be inclined to change their handling policies, suggesting that the reporting system may be ineffective.
Our research aimed to provide a better understanding of the DMARC ecosystem by looking at the DMARC records. For more information, we invite you to read the full paper.
Olivier Hureau holds a Bachelor’s degree in Computer Science and a Master’s degree in Cybersecurity from Université Grenoble Alpes. He is currently pursuing his PhD at Université Grenoble Alpes, focusing on the topic “DNS — Gateway to a More Secure Internet”.
Jan Bayer, Andrzej Duda, and Maciej Korczyński contributed to this work.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.
