
One of the biggest advantages of IPv6, from a network administration perspective, is the ease of renumbering. While IPv4 networks can be renumbered using DHCP, the process of changing the address of every device on a network is always fraught with unexpected challenges. People (like me) have a habit of manually assigning printers and network-attached storage (NAS) devices a fixed address so they will be easy to find and use.
IPv6 was supposed to change all of this. First, Stateless Address Autoconfiguration (SLAAC), combined with EULA64 addresses, and then DHCPv6, were supposed to put all this manual addressing behind us.
Whether or not they have is another question — I still need to assign my NAS a fixed address to make some applications work correctly. Windows File Explorer, for instance, still seems to treat the IP address as a host identifier for many devices. It’s maddening to continue facing these sorts of ‘least common denominator’ situations in networks after all these years.
Easy renumbering of IPv6 addresses should, in theory, make some privacy protection methods easy to implement. Treating a device’s IP address as a permanent identifier makes it easy to collect and track information about devices — and the people attached to those devices — over time.
Let’s look at the figure below to understand how easy renumbering helps preserve privacy.
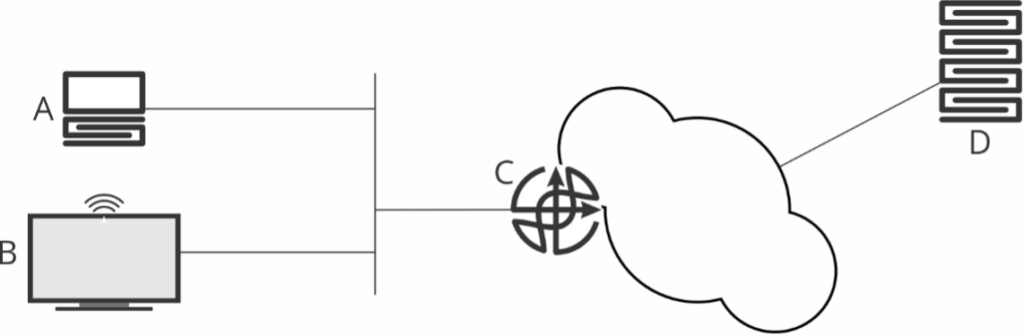
IPv6 has two kinds of addresses — link-local and global. The process to renumber, from host A’s (Figure 1) perspective, is:
- Create a link-local address using the FFE80:: prefix.
- Use this address to communicate with the DHCP server — in Figure 1’s example — router C, to obtain a global address.
The host, A, uses a local physical interface address to create a link-local address. Physical interface addresses are assigned to the interface, so they do not (or should not) change on wired links. The DHCP server, on the other hand, can assign a fairly random — within the assigned subnet — address to the host.
Every time the network is renumbered, host A’s entire address changes. There is no way for an observer at server D to relate host A’s address before renumbering and after renumbering. Some providers push new IPv6 prefixes to their customers regularly to force renumbering as a privacy measure.
This doesn’t block every way a host can be tracked; D could be fingerprinting the browser running at A, or using some other method to track A across IP address renumbering. But it does block one of them. In the worlds of privacy and security, you must solve all of the problems to solve the ‘whole problem’.
What about the television set, B? How does it handle renumbering? According to some fairly recent research (from April of 2022), many Internet of Things (IoT) devices just use an EULA64 address during renumbering. These devices build a global address combining a prefix provided by the router with a local physical interface address.
Even if the device is connected through Wi-Fi with MAC address randomization, the device has to use the randomly assigned MAC address when building an EULA64 address to get any real global improvement out of the feature.
Since physical (MAC) addresses are fairly unique in the real world, an observer at D can discover B’s old and new IP addresses by looking for IPv6 packets with B’s physical address in the lower 64 bits of the source address.
Is D’s ability to track B across IPv6 renumbering really a big privacy problem? Sure, D can still figure out what people in this house are watching on television, but at least A’s identity is still concealed, right?
Wrong.
A and B renumber at the same time, shifting from the old IPv6 prefix to the new one. An observer at D can correlate A and B, discovering they are attached to the same physical network, but noting changes in B’s IPv6 prefix.
This simplifies D’s discovery of A’s new IPv6 address. Combining the new IPv6 prefix with some basic characteristics about the host, A’s new address is fairly easy to discover — and A can now be tracked across IPv6 renumbering events.
How prevalent is the use of EUA64 addresses for IoT devices? According to researchers, it is very common.
There are solutions, of course. IoT manufacturers could use privacy-preserving random MAC addresses when building a public IP address. Some Wi-Fi networks already do this, but randomized MAC addresses need to be used for every device to get the full privacy boost.
If you run an enterprise network, you should turn on MAC randomization across all your devices. If you have devices that don’t support MAC randomization, push your vendors to include it in their feature set.
Russ White is a Senior Network Architect at Akamai Technologies.
This post is adapted from a series at Packet Pushers.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.

I think there is a typo… Should “but nothing changes in B’s IPv6 prefix” say “but noting changes in B’s IPv6 prefix”?
If the original text was correct then I’m horribly confused. 😛
Hi Nick, thanks for letting us know. Russ has gotten back to us and were correct. We’ve now updated the post. Thanks for spotting!