
HTTPS serves as a critical infrastructure for web security, protecting the privacy and integrity of communications between networks. An important aspect of the extension is the authentication process, which is powered by Web PKI via digital certificates that are issued by Certificate Authorities (CAs).
In the trust model of Web PKI, only certificates issued by trusted CAs can be authenticated. As a current best security practice, vendors of major operating systems and browsers maintain and preconfigure public lists of a hundred or so trusted CAs, called root stores. Some well-known CAs in public root stores include DigiCert and Verisign.
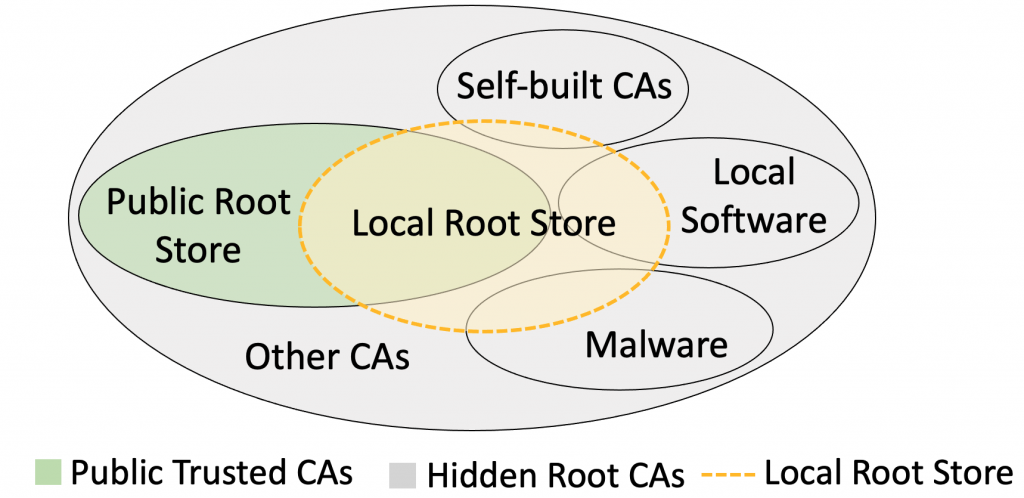
Unfortunately, despite being preconfigured, no concrete standards or best security practices have been established for managing client-side root stores. This is an issue as various third parties such as government agencies, VPNs or even malware could inject their hidden root certificates that are beyond public view into local root stores.
Furthermore, these hidden roots are not subject to public regulation, such as the Certificate Transparency project and as such may issue leaf certificates arbitrarily and intercept encrypted communication.
Researchers affiliated with Tsinghua University and the University of California, Irvine, recently provided a comprehensive measurement study of these hidden root ecosystems in a paper published at ACM CCS 2021. With the help of a popular browser vendor, they analysed five months of certificate chains and verification statuses of web visits from volunteers to shed light on the widespread and serious security flaws of hidden roots in the wild.
1.17 million hidden root certificates identified
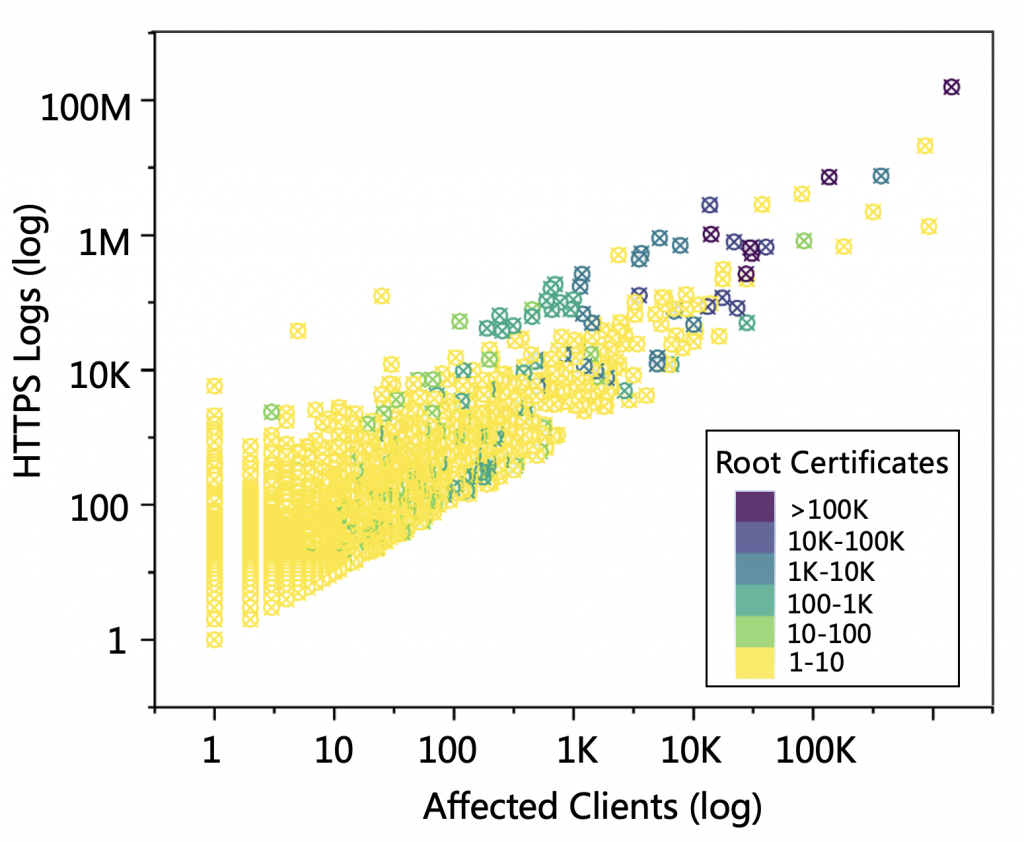
The measurement results demonstrated that client-side local root stores have been extensively manipulated. During the five months, 1.17 million hidden root certificates were identified as being installed into real-world clients.
The impact of hidden root CAs is far-reaching. The captured hidden roots signed leaf certificates for over 1.3 million websites, including high-ranking ones. They were also witnessed in 0.54% of all web connections, affecting 5.07 million clients and putting them at risk of interceptions.
Owners of hidden roots
We identified 5,005 organizations that operate these root certificates, including government/enterprise agencies and TLS-interception software (for example, packet filters).
| Categories | # organizations | # hidden roots | # affected clients | Example |
| Enterprise Self-built | 24 | 48 | 199,743 (3.94%) | CN = SZSE ROOT CA, O = Shenzhen Stock Exchange |
| Digital Authentication | 13 | 18 | 539,711 (10.65%) | CN = CFCA ACS CA, O = China Financial Certificate Authentication |
| Government Self-built | 13 | 16 | 62,032 (1.22%) | O = National E-Government Network Administration Center |
| Fake Authentications | 11 | 817,532 | 2,798,985 (55.21%) | CN = VeriSlgn Class 3 Public Primary Certification Authority - G4 |
| Packet Filter | 11 | 15,587 | 73,725 (1.45%) | CN = NetFilterSDK 2 |
| Proxy/VPN | 10 | 90,131 | 1,029,648 (20.31%) | CN = koolproxy.com, O = KoolProxy inc |
| Security Software | 2 | 7,187 | 4,719 (0.09%) | O = Beijing SkyGuard Network Technology Co., Ltd |
| Parent Control | 1 | 7,554 | 7,787 (0.15%) | CN = UniAccessAgentFW 2 |
| Unknown | 15 | 207,957 | 289,198 (5.07%) | CN = VRV NDF RootCA 2 |
Table 1 — Category of top 100 hidden certificate organizations.
Furthermore, we found a large number (0.8 million in 11 groups) of roots from ‘Fake Authentications’ that impersonated trusted CAs with deceptive subject names. For example, the largest organization held 254,412 hidden roots of ‘Certum Trusted NetWork CA 2’, impersonating Certum CA by replacing the lower-case ‘w’ in the legitimate CA with a capital ‘W’.
Threat intelligence indicates that some of the certificates may originate from malware such as Trojan and Coin Miner.
Implementation flaws
The security properties of hidden roots are of great concern. Unlike rigorously-audited public root CAs, many have serious operational flaws.
We found that potentially 75% of legitimate government and enterprise self-built root issued chains were invalid. This may be due to using weak algorithms, containing irregular certificate content, having an invalid validity period, and/or flawed issuance and management behaviours.
Action required to better manage root certificates
Considering the widespread and serious impact of hidden roots, various parties involved in Web PKI need to take action to better manage root certificates. Specifically, we recommend that:
- Operating systems should regulate root store policies to better monitor, log, and audit the modifications, and alert users of risks.
- Browsers could be extended to identify and block non-compliant hidden roots.
- Local software using custom root CAs should more carefully configure and manage their CAs.
In the long term, the community should look at more wide-ranging solutions including replacing current trust models with hierarchical authority architecture (for example, separate system root certificates from user root certificates, or using more granular trust levels).
For more details on our study, please refer to the paper ‘Rusted Anchors: A National Client-Side View of Hidden Root CAs in the Web PKI Ecosystem’ in the 2021 ACM SIGSAC Conference on Computer and Communications Security (CCS).
Yiming Zhang is a PhD student at Tsinghua University, under the supervision of Prof. Haixin Duan.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.
