
Privacy-preserving DNS protocols like DNS over HTTPS (DoH), DNS over TLS (DoT), and DNS over QUIC (DoQ) have been around since 2014 but they have only recently been brought to the attention of the general public following Firefox’s announcement to make DoH a default.
- DoH resolver lists are not comprehensive, which makes it difficult for network administrators to entirely block DoH connections.
- Encrypted DNS traffic jumped with browsers making it a default.
- USA and Brazil are leaders in encrypted DNS usage, but other economies are catching up rapidly, including Italy and Argentina.
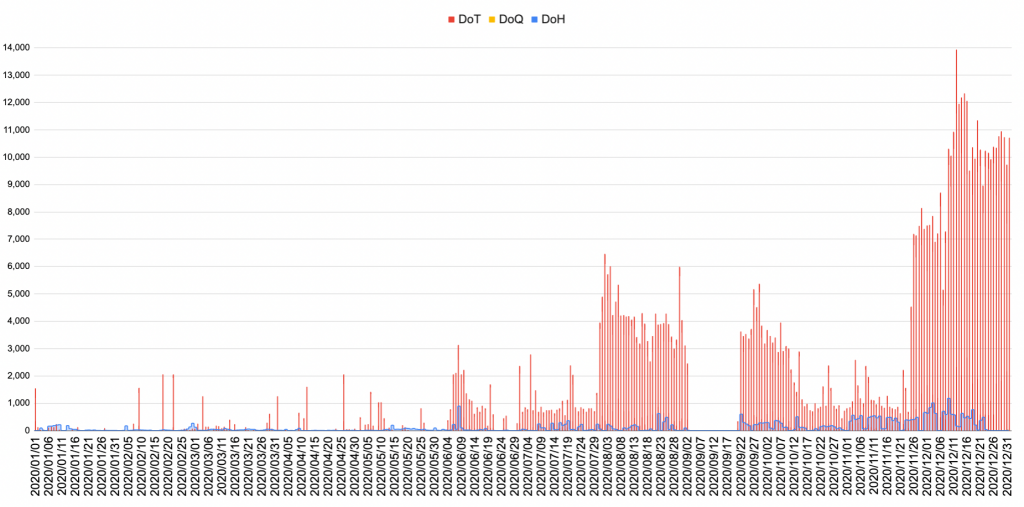
This announcement by Firefox has naturally led to an increase in the usage of these protocols (Figure 1, below) but not without contention, with multiple experts pointing to the security risks associated with these protocols, including how:
- Hackers and malware creators had already used encrypted DNS (notably DoH) to bypass threat detection.
- Many end-user security systems need unencrypted DNS communication to filter traffic, such as for parental control, enforcing security policy, and protecting against malware communication.
- Encrypted DNS cannot be easily inspected by security researchers to detect malicious activities. Additionally, DoH can’t be completely filtered as it is designed to blend into other HTTPS traffic.
Focusing on the the difficulty to filter encrypted DNS, each of these protocols could be filtered in different ways. DoT may be filtered using only the port number, but DoH can only be filtered by IP address, Server Name Indication extension of Transport Layer Security protocol (TLS SNI), and port matching in the firewall. This requires a comprehensive and well-maintained list of DoH resolvers, of which there are many, but each is different.
Because these lists are important security tools, researchers at the Czech Technical University in Prague, CESNET and Avast sought to measure the quality of these lists. In doing so, we compared what they were showing to what we could measure ourselves from active scans of the whole Internet to discover nearly four times more DoH servers than those currently recorded.
How many DoH resolvers are there?
We collected several publicly available lists of DoH resolvers to create a baseline for our active scanning measurement. This baseline list of ‘open knowledge’ active DoH resolvers consisted of 234 different IP addresses, 131 of which were IPv4.
To validate this list, we scanned the whole IPv4 address space and found servers with opened 443/TCP, using a simple TCP SYN scan in parallel. For the discovered IPv4 addresses, we tested for DoH found with the developed Nmap-NSE script. The script performed multiple DoH requests to each IP address and evaluated the answers.
From this, we discovered 931 DoH resolvers, seven times more IPv4 resolvers compared to the baseline. This does not include DoH resolvers that require knowledge of an SNI or HTTP Host Header for a successful request (usually when one IP serves multiple virtual hosts). Since the scan was only searching in the IPv4 address space, the host names were unknown and could not be provided to the scanning tools.
Naturally, we explored the discovered DoH resolvers further by issuing reverse DNS requests on the resolver’s IP addresses and evaluating the support of HTTP1, which is not recommended by the DoH standard due to the inability of creating concurrent DNS requests. Unexpectedly, 45 IP addresses only support HTTP1! Additionally, from the 931 IP addresses found, 251 did not have reverse DNS records. This fact suggests that these servers are run on a small scale by individuals. These small, privately-operated DoH resolvers are the main reason why DoH can’t be entirely blocked.
How popular is encrypted DNS?
The second part of our study focused on the adoption of DoH, DoT, and DoQ.
To evaluate DoH usage, three organizations — a large European ISP provider, a large European university, and a global security company — shared their experiences and performed large-scale measurements to gather statistics about DoH usage on their user base. The DoH measurements were based on domain names of the most popular DoH resolvers matching in the flow data.
We could measure DoT and DoQ based on port numbers since IANA has assigned them each a well-known port (853/TCP and 784/UDP).
In our first attempt, we tried combining the measurement data from all three institutions. Each of the institutions, however, had entirely different data. This is due to different levels of monitoring in end-point devices, university networks, or backbone ISP networks. We found that measuring encrypted DNS adoption across the user base of all organizations would be imperfect.
All three organizations could, however, agree on these conclusions:
- There is almost no DoQ in any measured network.
- ‘Classical’ DNS creates at least three orders of magnitude more traffic than encrypted DNS traffic.
- Everyone saw the same uptick in encrypted DNS usage in 2020 when Firefox and Chrome announced setting DoH as a default (you can see this in Figure 1), which pushed the encrypted DNS adoption to the current level.
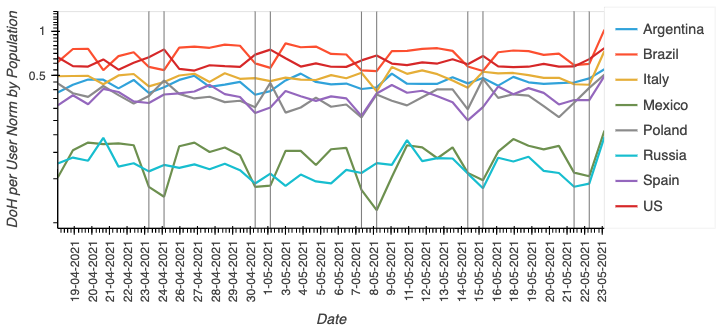
Additionally, since Avast has a global presence, we were able to explore the state of adoption in multiple economies. We found that encrypted DNS is very popular in Brazil and the USA (Figure 2) followed by Italy, Argentina, and Spain. Please refer to our paper for more details about our methodology.
There’s still work to do with DoH
Although there are many privacy benefits for users who encrypt their DNS requests, there are strong voices against the mass deployment of encrypted DNS, especially DoH. Data centralization is one of the main arguments against DoH usage and users are mainly afraid of bulk inspection and tracking by DoH providers.
A solution has been proposed in the RFC draft of Oblivious DoH (ODoH), where the user IP address is hidden behind an intermediate proxy. Even though ODoH mitigates users’ privacy concerns, it does not solve the security threats brought by encryption and lack of visibility, especially for common security systems deployed at the perimeter of networks or the ISP level.
Read: Improving the privacy of DNS and DoH with oblivion
Therefore, we advocate for further research in the field of security monitoring of encrypted DNS to enable users to resolve domain names privately and securely.
Contributors: Tomáš Čejka, Sebastián García, Armin Wasicek, Joaquín Bogado, Dmitrii Vekshin.
Karel Hynek is a researcher at CESNET and a PhD student at Czech Technical University. He primarily focuses on encrypted traffic classification and measurement.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.

DoQ: the title sounds like it’s been there for years, but I wouldn’t be confident to say it’s already there today. The RFC is not finished and there were incompatible changes recently (even the port number)… I believe there have been no IANA allocations for DoQ so far.
As for the final sentences, switching a protocol doesn’t really imply anything about centralization. Actually, the most prevalent centralization today is *unencrypted* Google’s public DNS.