
Attestation… simplified! This post explains how attestation can provide system-level remediation and resiliency. It can be conducted remotely and at scale, ensuring transparency of compliance with industry security controls and benchmarks.
Posture assessment: Shift left and build in security!
Attestation performed across the full hardware and software stack can be used to provide system-level posture assessment. The capability to perform attestation throughout the stack would shift responsibilities to vendors for continuous assessment capabilities.
This shift then enables new options and capabilities for organizations to use selected profiles that meet expected security levels. A small number of highly skilled professionals are then responsible for creating these profiles, eliminating the need for experts to establish configuration at each organization. This transition, and similar architectural patterns, will help to reduce the 3.5-million-person deficit of security professionals.
How is attestation scalable?
Given the above capability, the question that requires consideration is: How can remote attestation be used with this method to enable a scalable architecture for posture assessment?
Using attestation to assess assurance for a set of policies and/or measurements is widely deployed for firmware and BIOS, for both traditional hardware manufacturers and cloud offerings by hyperscalers.
Read more in this series:
- Trusted assurance simplified
- Where does zero trust begin and why is it important?
- Transforming information security to secure businesses
Providing assurance on higher layers of the stack, such as at the container or application layer, has been more difficult because systems and processes halt if set policies and measurements are not met. Having said that, container validation via attestation is now possible for at least a limited set of security policy requirements by several vendors.
The pervasiveness of attestations in the stack has increased and will continue to do so. In the firmware example, the root of trust typically relies upon the use of a Trusted Platform Module (TPM) or equivalent hardware-based security chip. To continually assess more than the firmware, the attestations on evidence would likely be performed using a hardware security module, in order to scale and avoid a possible bottleneck. A virtual TPM could be used for this function — possibly with a lower assurance level than a hardware-based TPM. Verification values for policies and measurements must be protected, whether on system or performed using remote attestation capabilities.
Enabling remote attestation
The previously mentioned, examples have largely been focused on providing assurance within a system. The next hurdle is how we enable remote attestation to provide posture assessment for all systems in a network that would be part of a larger governance, risk, and compliance (GRC) program.
Remote attestations are typically gathered via a RESTful interface, where access to the attestations is protected through authentication, authorization, and data protection controls. For devices, this is possible now. The attestations are accessible using YANG with RESTconf or NETCONF, which is described in more detail in the IETF draft, ‘TPM-based Network Device Remote Integrity Verification.’
In this case, the individual attestations, on evidence for comparison, are made available for assessment and even remote verification. This separation allows for detection of alterations to the policies and measurements by a sophisticated attacker, since they are also verified remotely.
For desktops and servers, the sheer number of individual attestations on evidence from boot and runtime on hardware and software from firmware to applications is quite large. Periodic runtime verification aligned to zero trust principles means that the full set would be transferred if remote attestations were performed in this way. Since the attestations are made available via a RESTful interface, the system can be polled on a timeframe suitable to the management station.
Attestation at scale
As we consider posture assessment across systems, scale is imperative, as is effectiveness of controls. Security assessment controls are typically specific to a software package or operating system as you go up the stack. This is evidenced by the numerous sets of benchmarks published by the Center for Internet Security (CIS) or a DISA STIG.
The CIS Benchmarks or DISA STIGS provide systematic guidance to harden an operating system, container, application, or device. DISA STIGS, in some cases, are detailed in CIS Benchmarks for ease of implementation.
Attestations are typically used within a system and are designed to be validated, providing assurance across the full set specified for the component (such as hardware, firmware, software, and libraries). It is important to perform this validation on a system and allow for remediation to occur if necessary. Remediation may be limited to notification in some cases if it could cause an impact to availability. Once the full set of attestations can be validated on a system, a single attestation may be created to assert the assurance level assessed by the local verification process. This attestation on the set of controls, verified with local attestation, could then be made available as a remote attestation.
In this case, the system generates a single attestation designed for remote access (remote attestation), providing assurance at a specified level on the set. The higher-level attestations could include event logs, such as those generated by the TPM event log, to ensure transparent visibility to the full set of controls verified. The posture assurance system could also be preprogrammed to understand how the attestation on a set of benchmarks or controls maps into and across the security controls frameworks in use (such as ISO 27001/2).
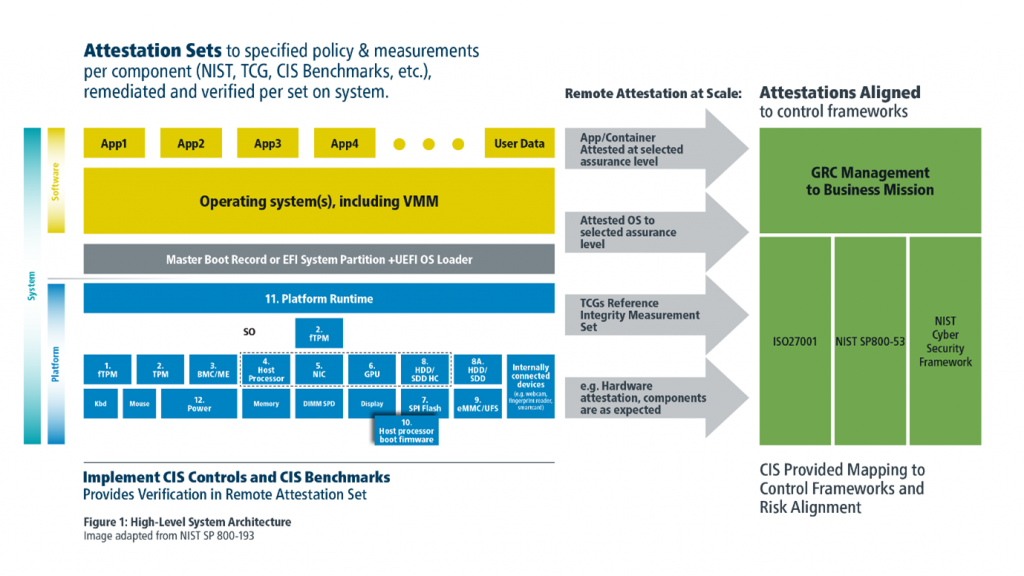
The sets of attestations would be guided by defined policy and measurement requirements, or industry accepted benchmarks, and potentially preconfigured to levels of assurance. This method enables a simplified posture assessment capability providing detailed insight to controls for those with skilled resources, and ease of management to accommodate businesses of all sizes.
This concept has been codified in the IETF draft on Remote Attestation Sets, which is available for comments and improvements in the IETF Remote Attestation Procedures (RATS) working group.
Kathleen Moriarty is Chief Technology Officer at Center for Internet Security and former IETF Security Area Director. She has more than two decades of experience working on ecosystems, standards, and strategy.
This post was first published on the Center for Internet Security Blog.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.
