
The NIST RPKI Monitor is a test and measurement tool designed to monitor the dynamics of the global Resource Public Key Infrastructure (RPKI) and the impact of RPKI Route Origin Validation (ROV) on Internet routing. Its purpose is to provide measurement data and analyses to the research, standardization, and operations communities necessary to improve the trust and confidence in the underlying technologies.
This is the second version of the National Institute for Standards and Technology (NIST) RPKI Monitor — developed to add more analysis features for understanding completeness, correctness, and stability of the global RPKI-ROV infrastructure.
Most of the analysis features of the original NIST RPKI monitor have been migrated to this new platform, but if you are looking for information from the prior version that you can’t find here, the original monitor is available here.
NIST’s Robust Inter-Domain Routing project is part of a larger Trustworthy Networking program focused on the research and development of technologies necessary to increase the security, privacy, and robustness of networked systems.
Uses
The NIST RPKI Monitor is a test and measurement tool developed by NIST’s Internet Technologies Research Group for the purpose of supporting research, and standardization of technologies to improve the robustness and security of the Internet’s inter-domain routing infrastructure. The monitor attempts to quantitatively characterize the state of deployment of the emerging RPKI in terms of its completeness, correctness, and robustness.
This latest version of the monitor provides all the analyses from previous versions, while adding new forms of analysis and new means to interactively explore data. The section below provides some highlights of the monitor’s capabilities. For full details see the NIST RPKI Monitor Methodology and User’s Guide page.
The monitor continues to provide analysis of the application’s global RPKI data to global BGP trace data. Various views of the results of RPKI-ROV, both current snap shots and historical views (summarized by various criteria), are provided.
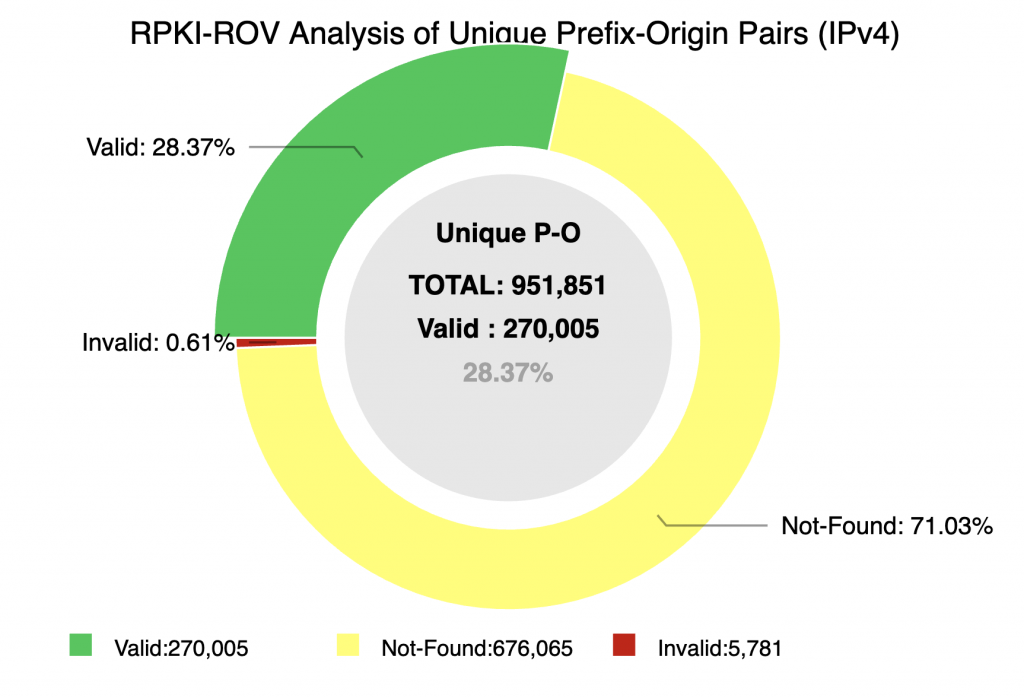
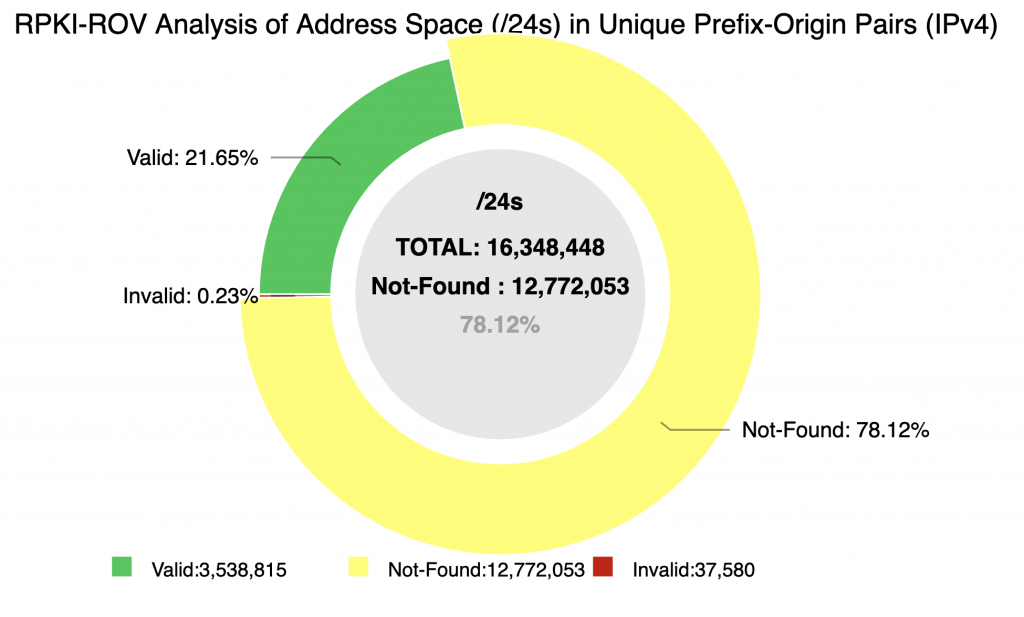
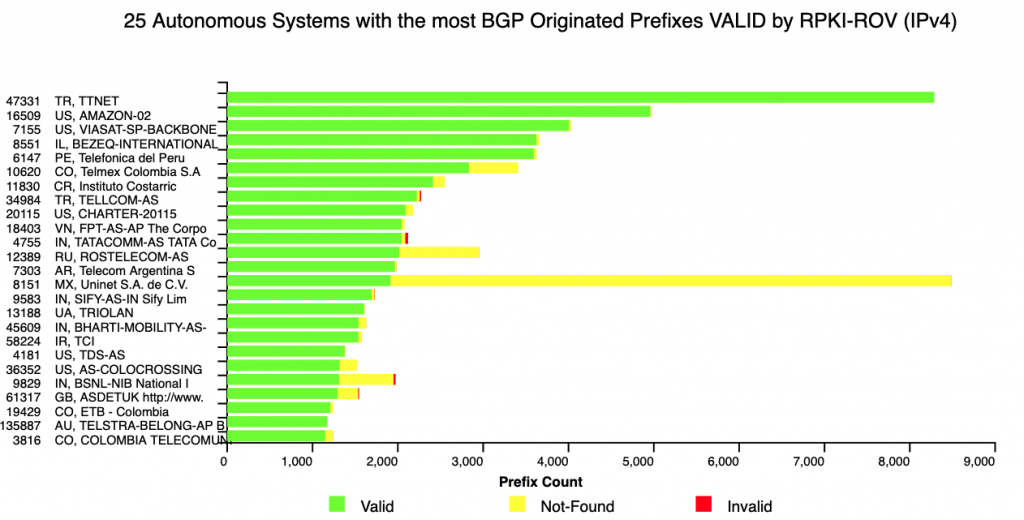
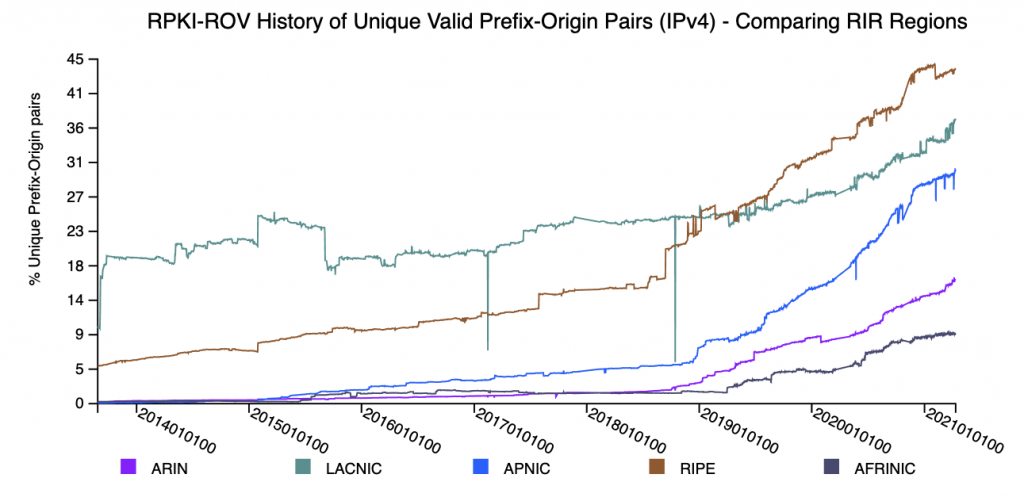
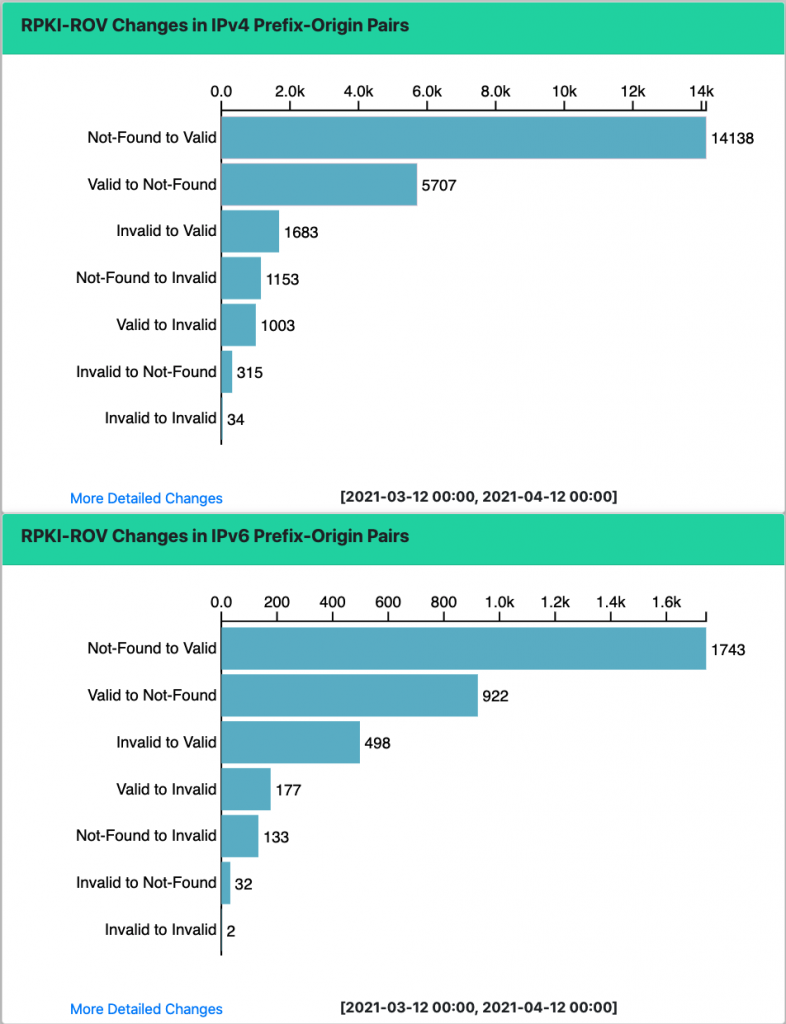
Many of the new analyses focus on understanding changes in the state of RPKI-ROV — both in terms of the volume of change and the details of individual validation changes. The monitor now allows one to see the details of the underlying RPKI changes that result in a change in RPKI-ROV for specific BGP originations.
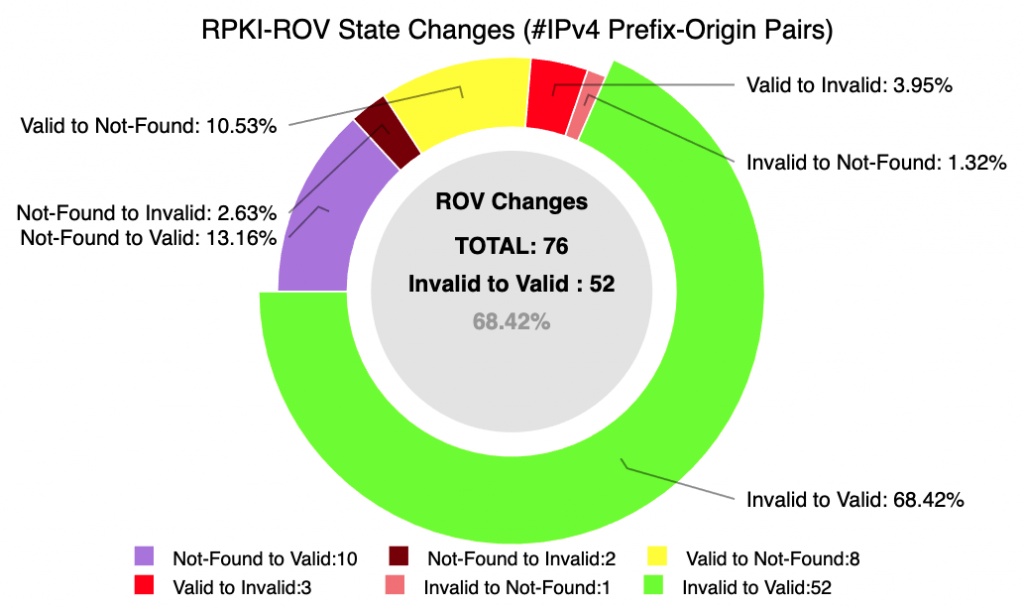
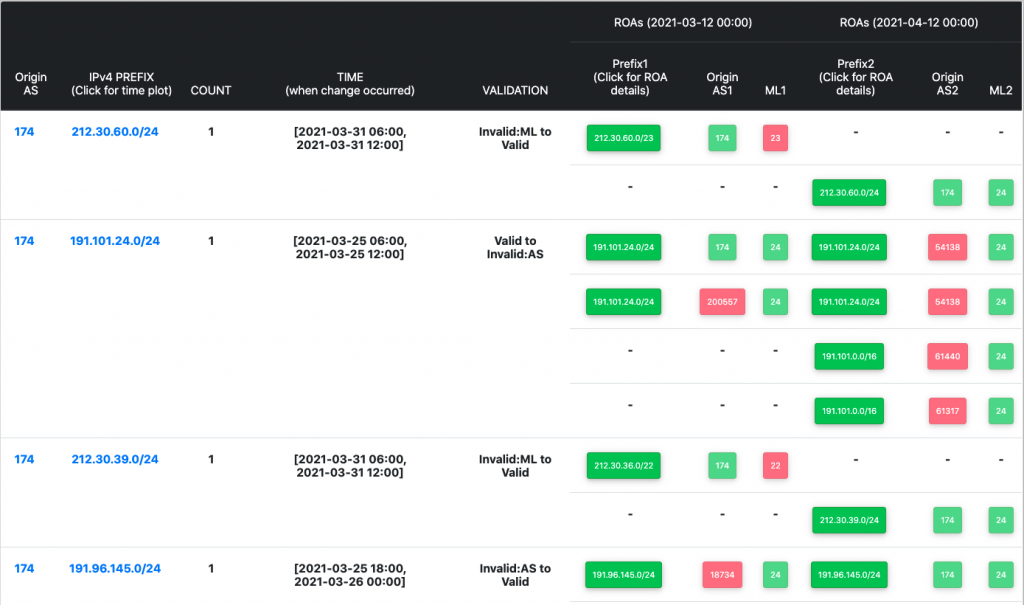
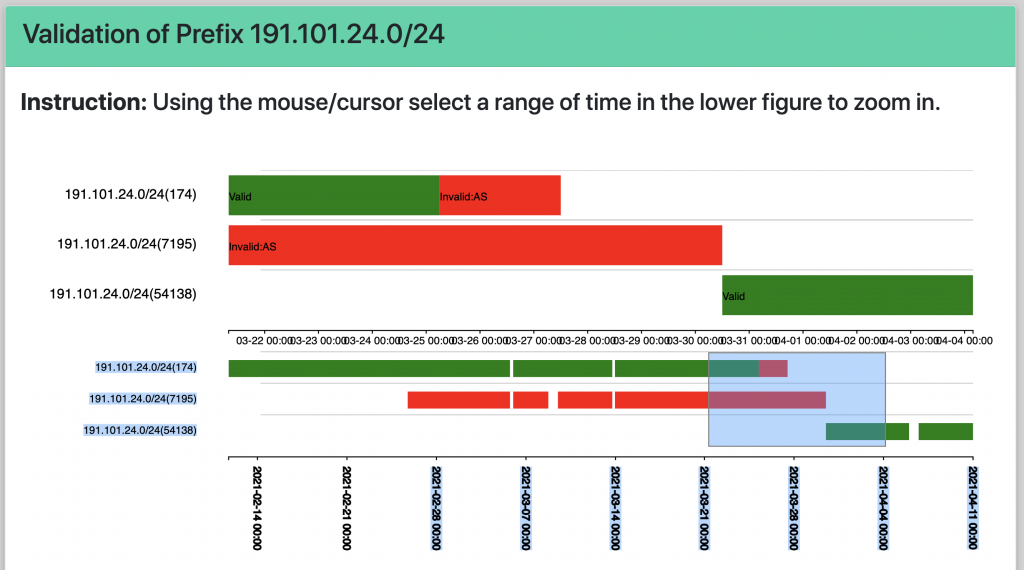
This version of the monitor provides the ability to filter the data and visualizations to focus on a specific set of prefixes, ASNs, regions or protocols (IPv4 or IPv6). The monitor also provides the ability to look back at results from specific dates, or to interactively explore a range of dates.
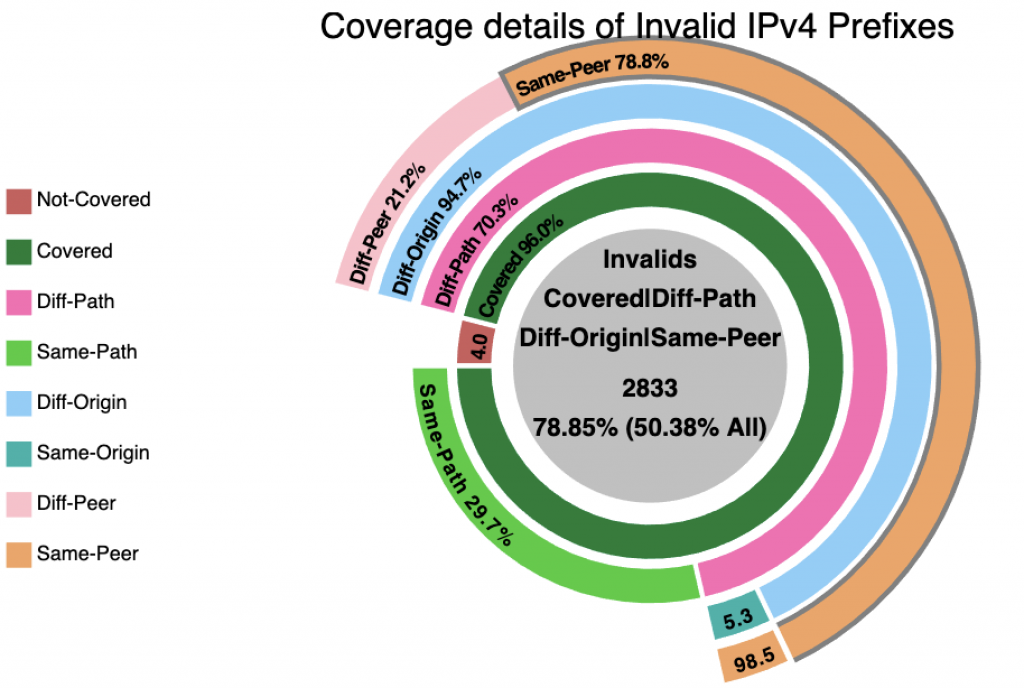
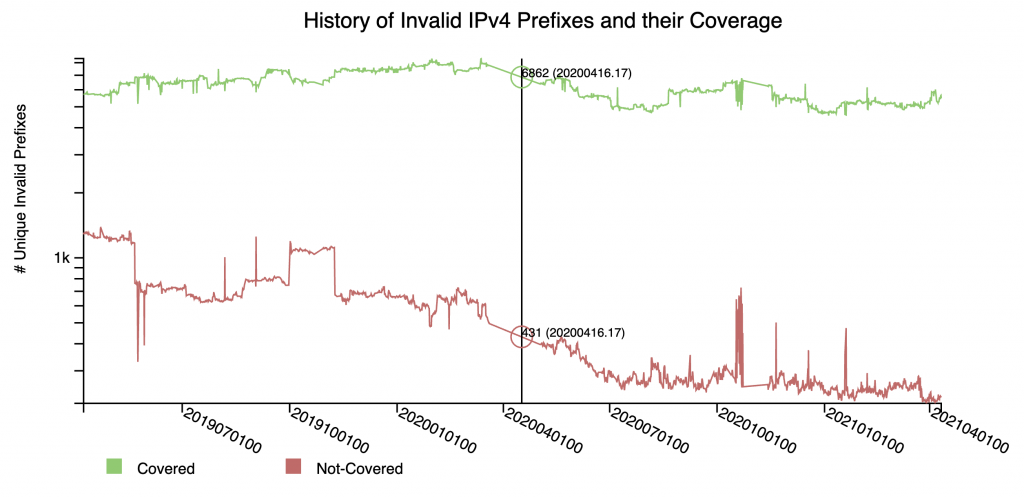
New analyses have been added to further examine the implications of RPKI-ROV invalid routes. In particular, the monitor provides analysis of the ‘coverage’ of invalid announcements — by other routes that are not invalid.
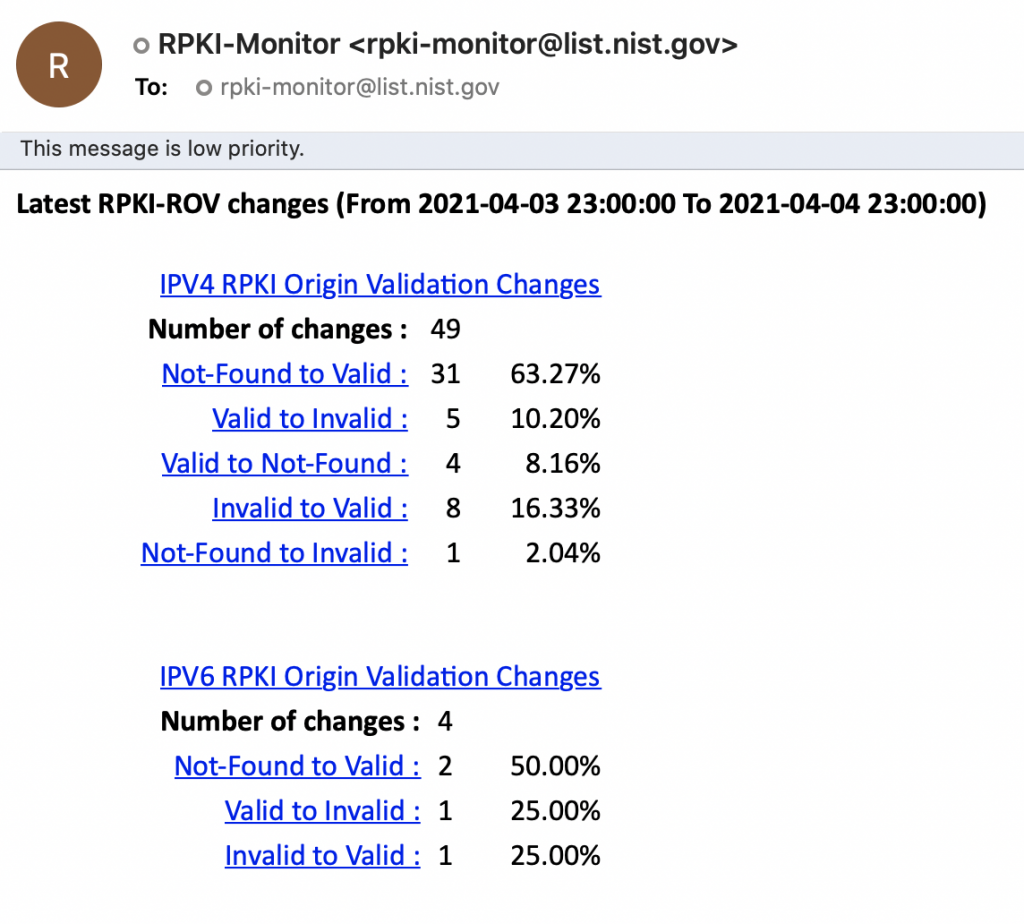
The monitor creates periodic summary reports for all RPKI-ROV state changes. The monitor also produces summary reports when it detects anomalies in the RPKI-ROV system (for example, unusually large number of RPKI or RPKI-ROV state changes, and so forth). Users can subscribe to an email list to receive these reports in a daily summary or more frequently. See the NIST RPKI Monitor Methodology page for instructions for joining these mailing lists.
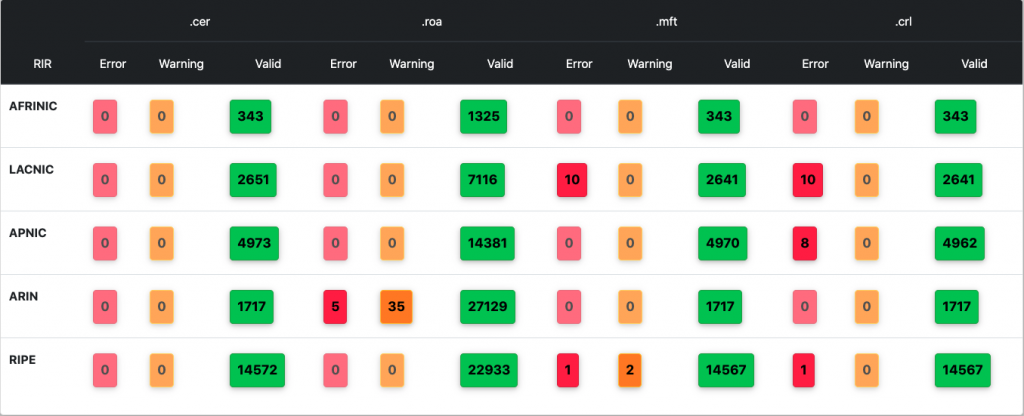
The monitor continues to provide analyses of global RPKI repositories, including various statistics on the size and shape of the RPKI infrastructure.
NIST’s full RPKI Monitor is accessible here.
The NIST RPKI Monitor software system was designed and implemented by Lilia Hannachi, Oliver Borchert, Kotikalapudi Sriram and Doug Montgomery.
Doug Montgomery is the Manager of Internet and Scalable Systems Research within the Information Technology Laboratory and was recognized as an IPv6 World Leader in the New Internet IPv6 Hall of Fame 2020.
This post was originally published at NIST Blog.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.
