
I’ve been receiving a lot of queries recently from the community on how to set up their networks to allow their remote employees to access internal business services securely.
Instead of being prescriptive, since one setup may not fit all, I asked our Community Trainers and my APNIC infrastructure colleagues to share their setups and common practices to manage the needs of their networks and staff from the confines of their home. I’ve summarized this below.
Remote network access
For accessing network nodes, the most common setup seems to be a combination of a remote access Virtual Private Network (VPN) to a jumphost, and access from the jumphost controlled through a AAA server, as shown below:
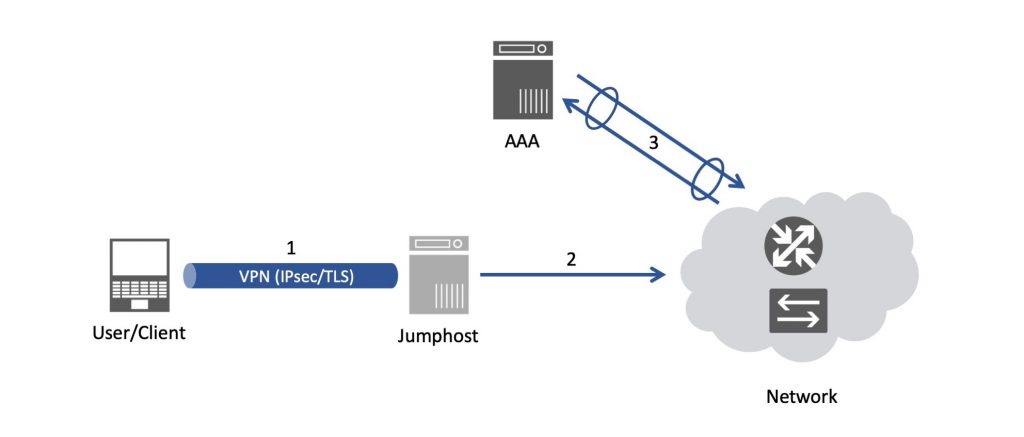
And, hopefully, this setup is with some form of out-of-band management — a suggestion is to use a dial-in modem, out-of-band if possible.
Corporate services access
There are many options when it comes to enabling corporate service access, based on your organization’s needs and the resources available to you. However, the easiest to set up is a VPN.
Note: scaling your VPN concentrator could be an issue if it was not designed to support most of your office simultaneously working from home.
There are a couple of options here with VPN access, each with its pros and cons.
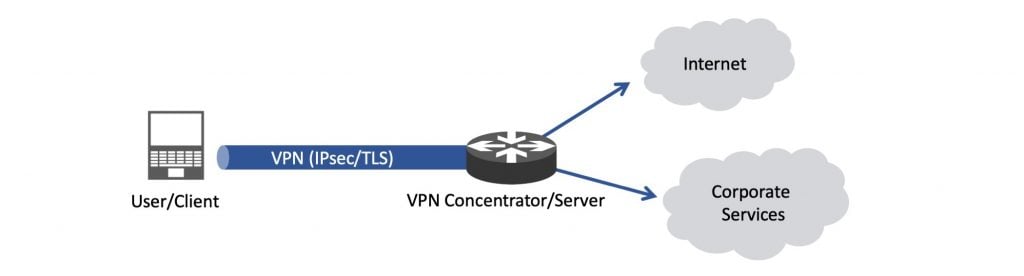
One option (Figure 2) is to have your remote staff/users connect to your internal services via the VPN (full-tunnel). This pushes all traffic over the VPN, allowing for central network security devices to inspect the traffic as if employees were in the office. Throughput could be an issue with this setup.
To improve performance, you could configure split tunnelling as shown below (Figure 3). This means only corporate sensitive traffic goes through the secure tunnel while other traffic (browsing and so forth) goes directly via their own home Internet connection.
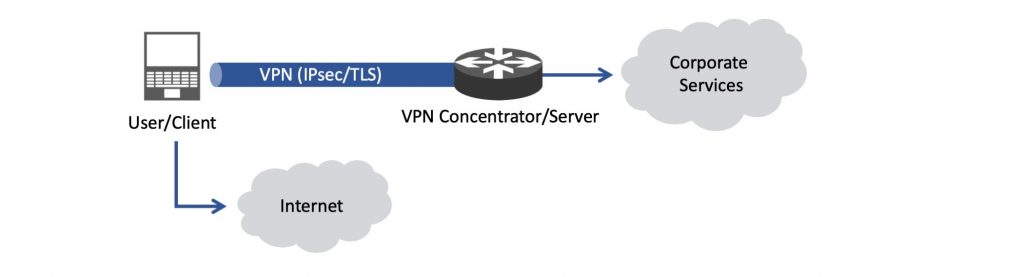
Security folks may not like this setup in case end users access websites with potential malware, without the normal security devices that usually exist in an office network. Or in extreme cases, if an end-user terminal is compromised, it might unknowingly allow access to the corporate LAN.
Single sign-on access
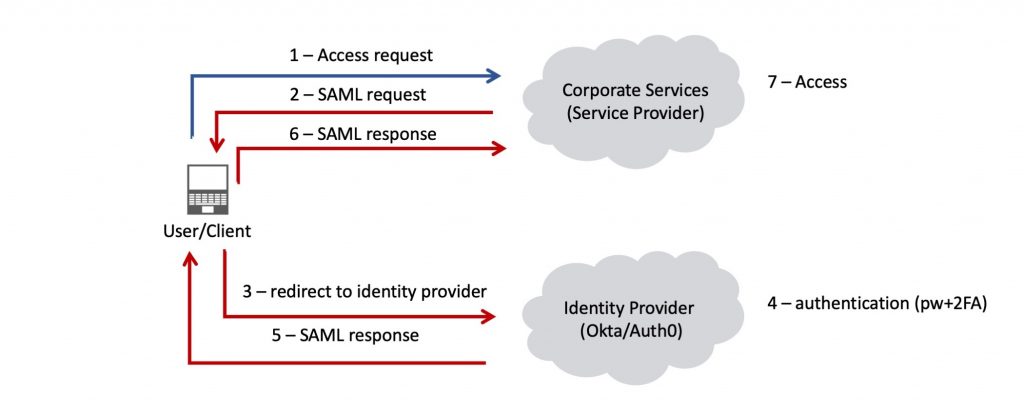
Single sign-on (SSO) requires the most work out of the options mentioned so far but can make accessing frequently used applications/services less tedious and most importantly, more secure.
The example below is a basic setup using Security Assertion Markup Language (SAML) based SSO with multi-factor authentication enabled. Other well known protocol options for SSO or federated identity management are OpenID or OAuth.
Communication tools
There is a broad range of tools that teams use to communicate while in the office, which works just as well outside of the office too.
The examples that Community Trainers are using include instant messaging services such as Slack, WhatsApp, Telegram, Signal and Dnote and web conferencing services such as Jitsi, Wire, 3CX, eduMEET, BigBlueButton and VMukti.
A common theme with the above is that they are mostly free or open-source and there is some form of end-to-end encryption, especially regarding messaging tools.
Comment below on what setup and tools you’re using to access your work network and communicate with your colleagues while working from home.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.
