APNIC will be progressively rolling out changes to improve the security and privacy of all encrypted web services, starting on 6 May 2020 and finishing on 4 August 2020. While users should not notice any difference when using a modern web browser, there may be some impact on programming interfaces and automation tools.
In early 2020, all major web browsers are removing support for TLS versions 1.0 and 1.1 which were the successors of SSLv3. TLS is the fundamental protocol used in encrypting communications with websites using HTTPS, and encrypting email both from client to server (POP/IMAP) and between servers (SMTP). TLS 1.0 and 1.1 are out-of-date protocols that do not support modern cryptographic algorithms, and both contain security vulnerabilities that may be exploited by attackers. TLS 1.2 was released in 2008 and is still considered to be safe, along with TLS 1.3, which was released in 2018.
To ensure the security and privacy of our public visitors, Members and Member data, APNIC will stop support for TLSv1.0 and 1.1 on all encrypted services and websites. This will begin on 6 May 2020 (30 days from this announcement) with the change to all web servers that are typically accessed by a web browser. Examples of these sites include:
- www.apnic.net
- blog.apnic.net
- academy.apnic.net
- training.apnic.net
- my.apnic.net
- stats.apnic.net
- resources.apnic.net
On 4 August 2020 (120 days from this announcement), all other servers that are typically accessed by application programming interfaces (APIs), scripting, and automation tools will be configured to only allow TLS 1.2, and 1.3 where possible. Examples of these sites include:
- wq.apnic.net
- rpki.apnic.net
- rdap.apnic.net
- rrdp.apnic.net
- ftp.apnic.net
- 6to4.nro.net
APNIC will continue to offer unencrypted access without TLS for some services such as whois (on port 43/tcp), and both encrypted and unencrypted access for some other services such as ftp.apnic.net, which is available via FTP, HTTP, and HTTPS; and RDAP, which is available by HTTP and HTTPS. No unencrypted connections are being disabled at this time.
Some FAQs to help you navigate these changes
How will I be affected?
- If you are using a web browser that supports TLS 1.2, then you will not notice any change. The current version of all major browsers support TLS 1.2 and 1.3.
- If you do not use a web browser or HTTP client that supports TLS 1.2 then after the above dates you will lose secure encrypted access to APNIC websites and services.
How can I check my web browser?
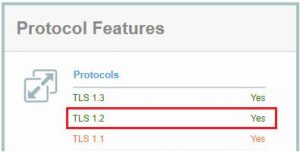
- Visit https://www.ssllabs.com/ssltest/viewMyClient.html and look for a ‘Yes’ next to TLS 1.2 in the Protocol Features section.
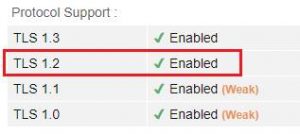
- If you cannot access the SSL Labs website, another option is to visit https://browserleaks.com/ssl and look for ‘Enabled’ next to TLS 1.2 in the Protocol Support section.
- Another simple service to use is https://tls-v1-2.badssl.com:1012/. If you can see the green webpage in your browser, or a block of simple HTML code from a CLI tool, then your program supports TLS 1.2.
Those websites say my browser doesn’t support TLS 1.2, what do I do?
- You should upgrade your current browser, or switch to a browser that supports TLSv1.2.
- APNIC makes no recommendations on which browser to use, whether they are shown as swirls, foxes, compasses, or otherwise.
I run a web server, should I also disable TLSv1.0 and 1.1?
- All messaging from PCI, IETF, and the major web browser vendors say all web servers should only support TLSv1.2 and higher.
- Web server operators should perform their own assessment and their own messaging to their users.
- There is an easy TLS configuration tool at: https://ssl-config.mozilla.org/ (intermediate configuration), which gives configuration examples for many different web and mail server software. Additional background on the decisions made by this tool is at: https://wiki.mozilla.org/Security/Server_Side_TLS
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.