
A bug bounty is a reward paid to hackers who have found and reported a weakness or vulnerability within an organization’s system(s). This reward may be a cash or in-kind reward or recognition of another kind.
Hackers who report these vulnerabilities to organizations are known as White Hat Hackers or Cyber Security Researchers and are not considered criminals, but collaborative members of an organization’s security system.
Why a bug bounty program?
While a bug bounty program may appear to be ‘fighting fire with fire’, it is more about preventing the fire. It invites a White Hat Hacker to think, explore and report before a bad guy creeps in. In other words, bug bounties help an organization get (and stay) ahead.
As organizations upgrade to keep up with the latest technology, malicious actors are also becoming more sophisticated. Organizations and their IT staff are aware of this danger, but many believe they are satisfactorily protected, or that their organizations are too small to be targeted. But in reality, every organization is susceptible to attack. Security bugs exist in every software or system. No one is protected or immune by default, so you must be prepared and get protected.
This is where the Cyber Security Researcher comes in, assisting organizations in looking at the bigger picture of cybersecurity and resilience.
Why are they important?
Bug bounty programs are an important tool in finding potential vulnerabilities or flaws, but they are often misunderstood. The US Senate called a hearing last year to understand the nature and purpose of bug bounty schemes.
“Hackers are the Internet’s immune system”
Keren Elazari
Cyber Security Researchers and White Hat Hackers must think beyond the ‘hacker’ mindset and act ethically and responsibly. Organizational security and IT teams are very much capable, but they operate within the organization’s protocols (the box) and are busy with day-to-day routines.
On the other hand, a Cyber Security Researcher operates beyond the set organizational protocols, thus looking outside and beyond the box. They make a hobby of breaking the box. This is why many organizations these days are seeking the assistance of external Cyber Security Researchers to look into their systems (according to an agreed scope of engagement), to find and report on any system weaknesses, vulnerabilities, or exploits. As cybersecurity expert Keren Elazari says, these hackers play an important role as “the Internet’s immune system”.
How to set up a bug bounty program
The step-by-step process requires you to evaluate your:
- Organization
- Systems
- Hardware, network systems, software and the physical environment of server rooms
- IT team
- Security team
- End-users and their access levels
- Create a Vulnerability Rewards Program (VRP) policy
The latter of these requires you to:
- Discuss the findings of step 1 and implement changes if required.
- Prepare a draft Vulnerability Disclosure Policy.
- Decide on a bug bounty reward program or system.
- Define the rules of engagement, including the scope, focus areas and guidelines.
- Decide with unquestionable clarity the authorized conduct and engagement of the Cyber Security Researcher.
- Decide what proof is needed to confirm a vulnerability and how both ethical hackers and the organization will communicate with each other and share findings.
- Define how you will evaluate possible Cyber Security Researchers or platforms.
- Decide how you will approach platforms or researchers, and whether this outreach will be private or public.
- Discuss with your team and evaluate the above steps one more time.
- Discuss with senior management, the board of directors or IT steering committee.
The next steps are documentation, validation, authorization/approval, and publication on the organization’s website.
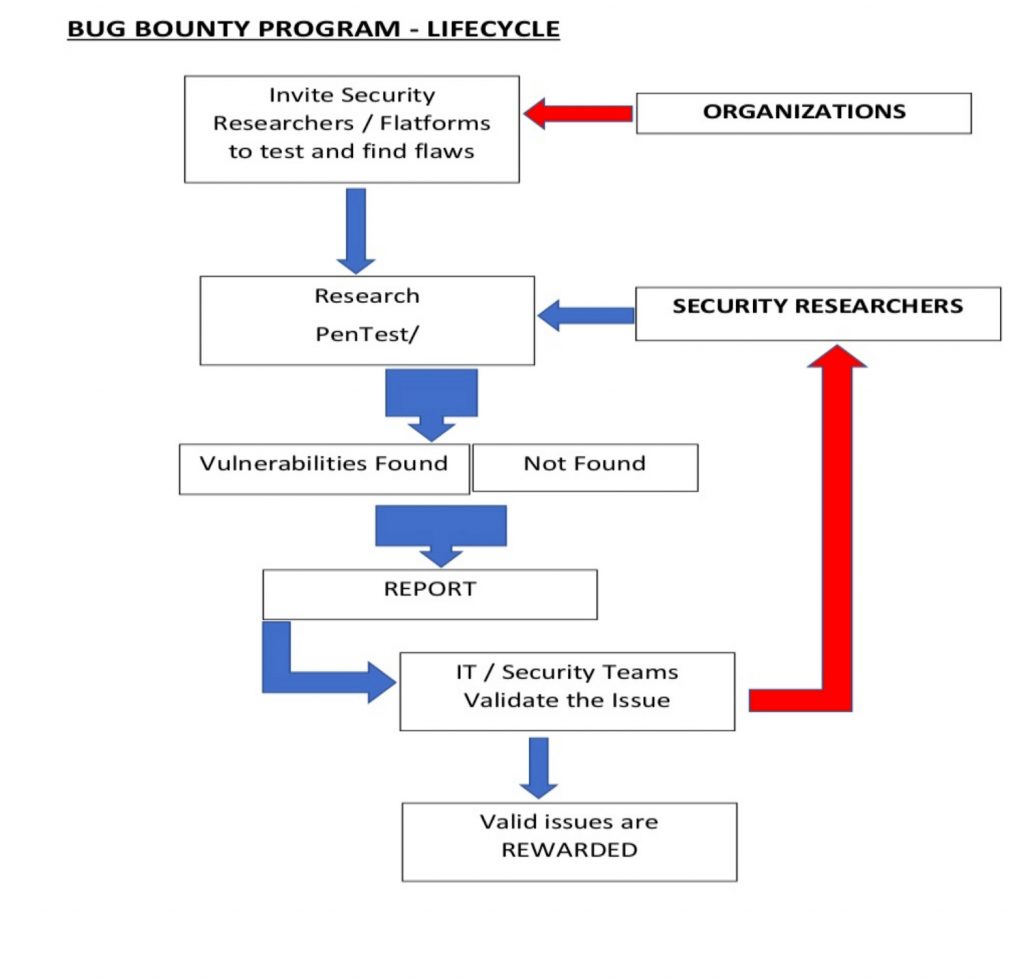
Finally, it’s very important to select your point person carefully and make sure their contact details are well publicized. They must be very responsive and technically savvy.
Remember to provide clear instructions about the program, along with the specifications of the overall surface, which may be an IP address, domain name, type of test, type of report, and so on. And be sure to emphasize any exclusions.
Pasan Ravana Lamahewa is a Cyber Security Researcher, Bug Bounty Hunter and Civil Aviation Pilot Trainee, who has been identifying flaws and loopholes his whole life.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.
