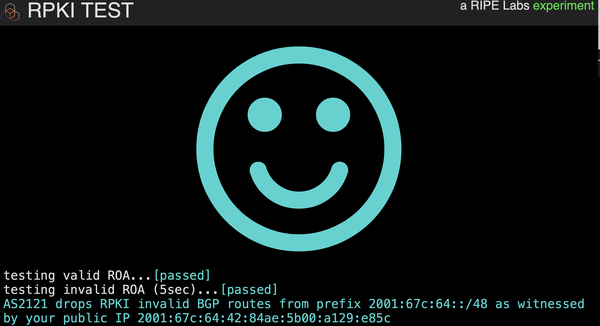
How can you quickly figure out if a network you are using is dropping invalid Resource Public Key Infrastructure (RPKI) BGP announcements? Simply open a web browser and visit the RIPE NCC’s RPKI test web page.
During RIPE 78, the RIPE community asked us at RIPE NCC to configure the meeting’s network in a way so invalid RPKI BGP announcements were dropped. This was indeed the current configuration, but it is not easy to check. So we built an experimental webpage where you can check if the network you are using is doing RPKI Origin Validation.
This is not a new trick, it was also used before for IPv6 testing. To adjust this to work for RPKI, we used two test prefixes (courtesy of NTT Communications):
- One that is covered by a valid Route Origin Authorization (ROA)
- Another one that is invalid (on purpose of course)
There is a webserver in both that serves content, so if you cannot fetch the content from the invalid and you can do so from the valid, then it’s highly likely the network you are on is dropping invalid RPKI BGP routes.
Please test this tool and check if the network you are on drops invalid RPKI BGP announcements.
Currently, this is only available on IPv4 as we wanted to have this finished before the end of RIPE 78. We are aiming to make it available to IPv6 too, and be future-proof soon!
Learn more about RPKI and how to validate ROA objects.
Contributors: Emile Aben, Jasper den Hertog, Job Snijders
Adapted from original post which appeared on RIPE Labs.
Nathalie Trenaman is a trainer and IPv6 Program Manager at RIPE NCC.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.