Transport Layer Security (TLS) is one of the most important cryptographic protocols in the Internet, used by hundreds of millions of people and devices every day. It assists with encrypting more than 60% of web traffic, including online banking, popular web services — including Gmail and Facebook — mobile applications and even back-end operations of large organizations.
In order to stay secure, it has had to constantly evolve in the face of each new attack and vulnerability including, BEAST, Lucky 13, POODLE, HeartBleed, FREAK, Logjam, and multiple attacks against RC4.
In a large-scale, longitudinal study that we performed in collaboration with researchers from the IMDEA Software Institute, Stony Brook University, International Computer Science Institute, Royal Holloway University, and IMDEA Networks Institute, we examined the evolution of the TLS ecosystem since 2012, using a dataset of 319.3 billion TLS connections collected from large universities and research centres across North America.
The following post is a summary of the key findings from our study that will be presented at the ACM Internet Measurements Conference (IMC’18) happening in Boston, USA, later this week.
Use of cipher suites has been affected by attacks
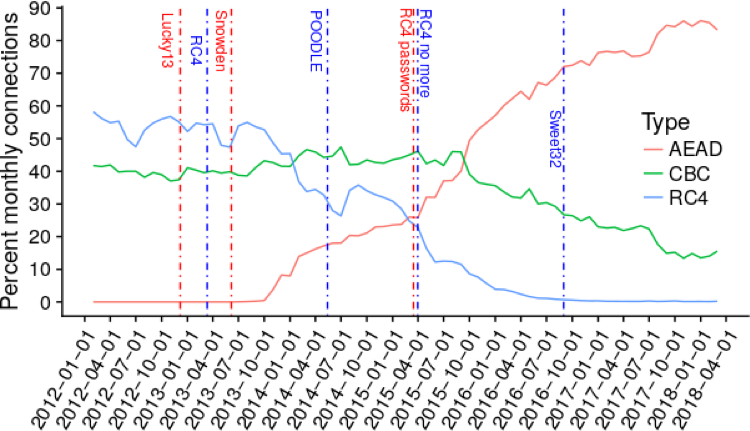
Correlating major changes in the support and use of cipher suites and extensions with the timing of specific TLS attacks, we observed a few cases, such as Heartbleed, where the ecosystem changed very quickly. However, it took several years for RC4 usage to reduce significantly after attacks against RC4 were discovered.
Moreover, we have not observed a change in our traffic after the CBC attacks (BEAST, Lucky 13, and POODLE), possibly due to the lack of better available options at the time or the existence of patches. Also, server support for SSL3 is still embarrassingly high, despite the severity of POODLE and RC4 attacks.
Taking a closer look at client software, we observed that while clients, especially web browsers, are quick to adopt new algorithms, they are slow to drop support for older ones. We believe this happens due to backward incompatibility, software abandonment, and the difficulties faced by developers in keeping up-to-date with proper TLS usage.
We also encountered significant amounts of client software that probably, unwittingly, offer unsafe ciphers. Supporting old and unsafe ciphers is problematic not only because of downgrade attacks that have surfaced time and again, but also because it leaves room for misconfigurations.
TLS has grown significantly since 2012
On a more positive note, we observed significant improvements in the TLS ecosystem over the last six years.
In 2012, 90% of TLS connections used TLS 1.0, while today, 90% use TLS 1.2. In 2012, the use of RC4 and CBC-mode for encryption was prevalent; today RC4 has almost completely disappeared in response to attacks, while CBC-mode accounts for about 10% of traffic (Figure 1).
Figure 1 — The rise and fall of popular cipher suites AEAD, CBC and RC4 from 2012 to 2018.
Known weak cipher-suites have been largely replaced by modern Authenticated Encryption with Additional Data (AEAD) schemes, one of the most popular being AES-GCM.
Moreover, we observed significant declines in the advertisement and use of export cipher suites, anonymous cipher suites, and vintage algorithms such as 3DES.
We also recorded a rise in the use of forward-secret cipher suites, now accounting for more than 90% of connections. Interestingly, the start of this shift correlates in time with the Snowden revelations.
Ephemeral elliptic-curve-based Diffie-Hellman key exchange (ECDHE) now dominates RSA key transport in TLS handshakes, with Curve25519 gaining in popularity and accounting for more than 20% of connections today.
Support for TLS 1.3 is already strong
Finally, we already see significant support for TLS 1.3 even before the standardization process has been concluded. Where in the past there was a gap of years between standardization of a technique and its deployment, today this time gap can be practically zero.
All these improvements point towards the fact that encrypted communication is seen as a much more important topic today than it was even as recently as 2012. This is due in no small part to the influence of a few large vendors (including Cloudflare, Facebook and Google) becoming more actively involved in the standardization bodies such as the IETF and vendor forums.
Platon Kotzias is a PhD student at the IMDEA Software Institute and Universidad Politécnica de Madrid (UPM). His research interests include malware detection, analysis and classification as well as intrusion detection.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.