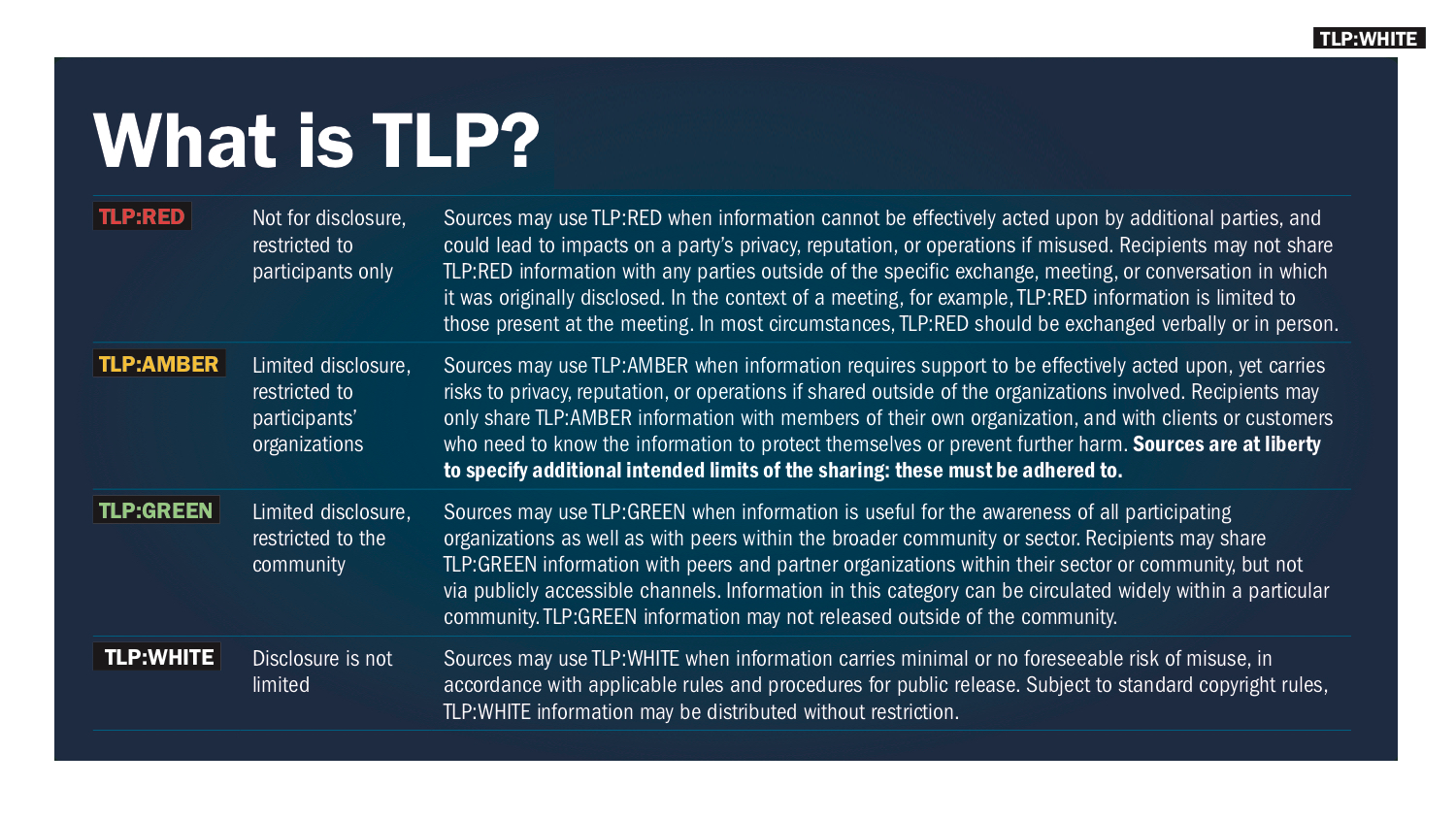
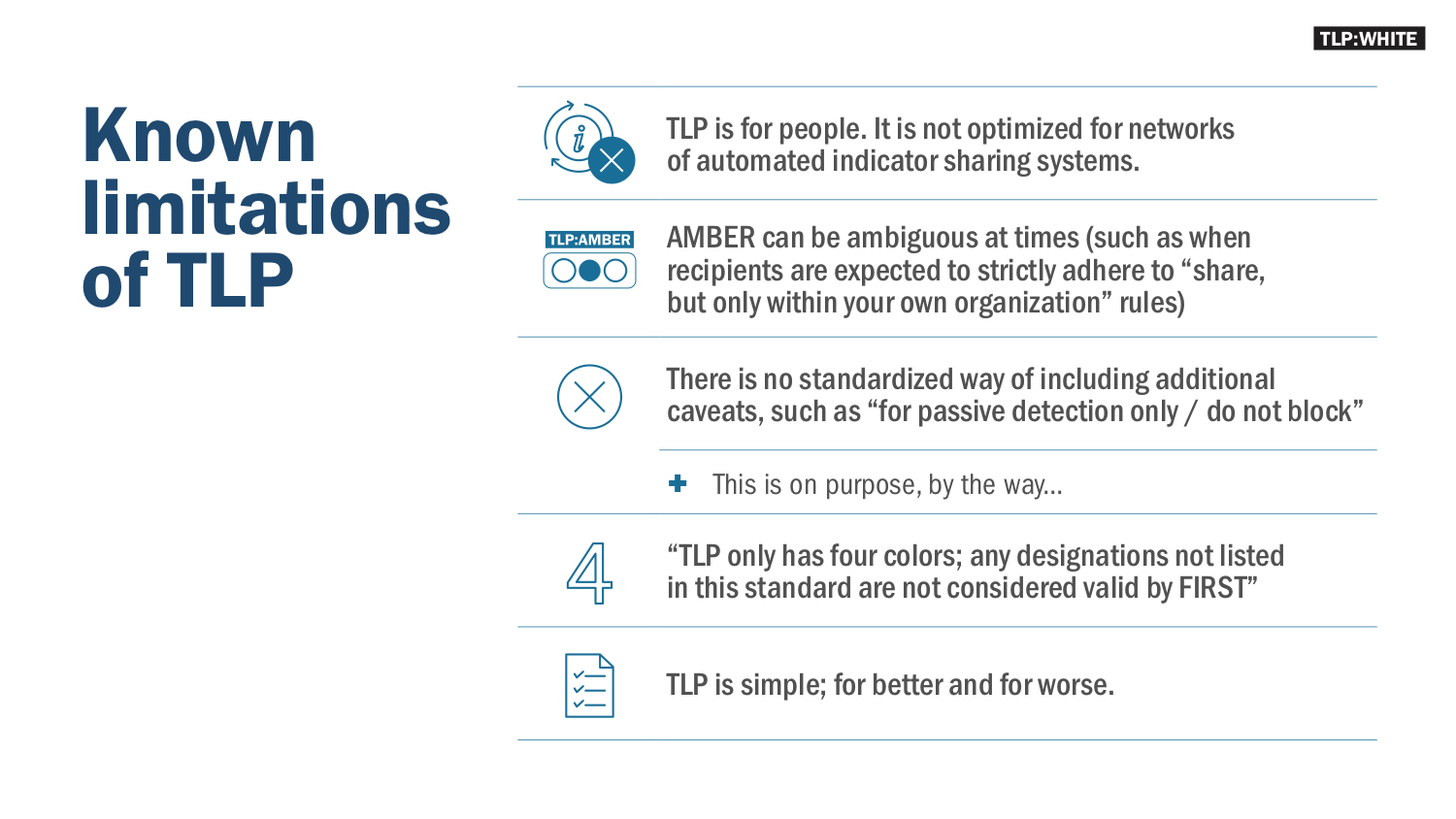
Traffic Light Protocol (TLP) was created to jumpstart sharing in small trust communities made up of teams from different organizations.
It began as an example of how to designate shared information so that people could be confident their information would get to only the right people and not leave those boundaries, and how to do so without a lot of negotiating beforehand — ‘Here’s TLP, this is what it means, let’s all use this.’
Other, superficially similar ‘protocols’ I’m aware of are all classification marking schemes used by national security and intelligence organizations, and those become relatively useless when you’re trying to encourage sharing, rather than strictly limit it to those with proper clearance.
Most in the Computer Security Incident Response Team (CSIRT) community (like FIRST members) know about TLP, but may not use the FIRST TLP standard, opting for their own slightly different definitions instead. A lot of other folks in intelligence, defence, cyber policy, public relations/public affairs, and in ICT or Internet governance, however, don’t know much about it or don’t understand it — and it would be really helpful in many cases if they did. That’s one reason the TLP Special Interest Group (TLP-SIG) is planning to produce a training module to put on its website to help provide an introduction to TLP for all sorts of audiences.
TLP has been incredibly beneficial in the CSIRT and cybersecurity community. It even helps delimit phone conversations sometimes. You can talk about one topic, call it TLP:WHITE, and then switch to another topic and make sure everyone understands it’s at TLP:RED. It even helps me when I’m taking notes or creating slides like the ones I developed for the FIRST Conference 2018 below (note the TLP:WHITE in the corner) — see the full presentation.
There are criticisms of TLP, for sure, mostly around how ambiguous TLP:AMBER can sometimes be, but, overall it’s really useful, which you can see by how many teams in FIRST have adopted it, even before FIRST created its standardized version.
Reducing TLP limitations with Information Exchange Policy
Information Exchange Policy (IEP) is fully compatible with TLP, but tackles things that TLP can’t.
TLP really only answers the question ‘Who may I share this with?’ — and not in an especially nuanced way, if we’re being honest.
IEP adds the ability to express things like, ‘You can share this with your own company, if you take out the victim’s PII first’ or ‘You can share this with the entire cybersecurity community of practice, but encrypt it in transit and keep the source anonymous.’
It can also answer other issues related to what types of defensive measures can be taken, or how far and wide to share information, in a much more granular and detailed way than TLP can. It is a flexible and extensible framework built to address many of the shortcomings that have been identified with TLP over the years.
To my knowledge, outside of very particular licensing and sharing agreements in very small communities, there hasn’t been anything else like IEP, certainly nothing as extensible. IEP is built to provide for inter-community sharing and interoperability between different sharing schemes — this is what gives it incredible potential.
On the downside, like any new concept, IEP is going to create some ‘first mover’ disadvantages for teams that adopt it early. There won’t be a lot of other teams ready to implement it fully, and there will be some pitfalls and design mistakes uncovered in the process — there always are.
However, we have seen this before with other things that set out to address the challenge of enabling better inter-community sharing, like Structured Threat Information eXpression (STIX), and as long as you have a strong network of adopters willing to work through the challenges because they can see the potential in it, eventually the network effects come along and communities you’ve never heard about are picking up the idea and running with it.
Thomas Millar is a Technical Advisor to the Under Secretary of the National Protection and Programs Directorate in the US Department of Homeland Security and co-chair of the FIRST Traffic Light Protocol SIG and FIRST Ethics SIG.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.