
The Domain Name System (DNS) is known to be a valuable source of threat intelligence. With the mainstream introduction of the Response Policy Zone (RPZ) technology in popular resolver software, there is now a growing market of DNS service providers who are offering DNS firewall-style services. These include free, open-Internet resolvers, commercial platforms, and even a bolt-on feature within personal VPN services.
At Nominet, we’ve been operating the UK Protected DNS resolver service (UKPDNS) on behalf of the UK Government since April 2017. It comprises two DNS resolver elements — one accessible from the public Internet and another for use within a private-public services network. The service is ‘anycast’ from a set of distributed nodes. To use the service, approved organizations simply forward their DNS queries to one of two public IP addresses.
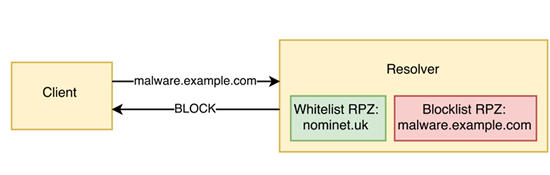
Figure 1 – A query for ‘malware.example.com’ is matched by the RPZ blocklist.
Within each resolver node, RPZ technology is used to interrupt DNS resolution on any queries where the domain names or resolved IP address matches known sources of malware. In this way, the policy can be enforced on both incoming queries (Figure 1) and responses received from the Internet (Figure 2).
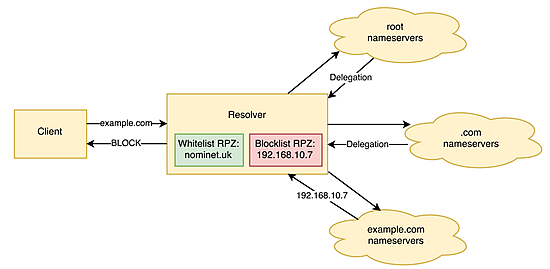
Figure 2 – A query for ‘example.com’ is blocked because the A record returned is for a blocked IP address.
The domain names and resolved IPs we block are stored in DNS zone files, the data for which we obtain from open source and commercial intelligence providers.
In exploring this data, we have found that the relative overlap between different data feeds is comparatively low. By ingesting a diverse source of intelligence data, it is possible to defend against a variety of malware classifications.
Having observed the churn of data from intelligence providers over the course of 2017, we have found that compiling new RPZ zones frequently throughout the day ensures that the latest data is available to protect the network and that the zones do not become stale with expired threats.
To mitigate the risk of blocking access to core business applications, we implement a whitelist of critical domains that should never be blocked, irrespective of the presence of malware. This includes search engines, cloud services, business applications and so on. The premise of this design choice is that the negative impact of blocking these resources would outweigh nearly all potential malware threats.
Once a nefarious query has been matched, several standard RPZ actions can be taken, such as returning a non-existent ‘NxDomain’ response, dropping the query entirely, or asking the client to try again over TCP. However, for the UKPDNS service, we have chosen to respond with an IP address of a webserver that hosts a ‘block page’. This webpage explains that DNS resolution has been interrupted and offers an escalation channel for the customer if they feel this action is unwarranted or is causing business disruption.
We have seen good customer engagement through this channel in the small handful of cases where it has been used. This approach works best when a blocked website is requested from a browser. It is less effective when individual website components are blocked, such as undesirable JavaScript. Although the block page arrangement is not perfect, on balance we have found it to be a useful tool in building trust with users.
The results from the service have been very positive, with thousands of malicious DNS queries being blocked each week. Combining the sources of blocked queries with malware indicators of compromise (IoCs) allows us to track threats as they traverse across customer networks. Some wins from 2017 include: identifying families of domain generating algorithms, monitoring for the presence of cryptocurrency mining, and tracking ransomware.
The implications of manipulating DNS queries can, at first, sound quite unsavoury. However, by curating robust RPZs and by being open and communicative with users, it is possible to make a positive difference to network security while also providing advanced threat analytics across an IT estate.
Watch James Richard’s presentation on using a DNS RPZ to protect against malware at UKNOF39.
James Richards works as a DNS data analyst at Nominet, UK. He investigates security and performance incidents across authoritative top-level domain and recursive DNS services.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.
