This is the first of three posts describing CERT Australia’s experience in deploying an automated platform for cyber threat intelligence sharing, discussing lessons learned and exploring future opportunities.
The cyber threat remains not only pervasive and agile, but also manageable through the application of effective security controls and efficient detection and response procedures.
Security automation and cyber threat intelligence can play a significant role by filtering out the noise floor created by unsophisticated and untargeted threats, providing insight to the evolution of sophisticated adversary tradecraft, and validating defensive security and response measures.
Why did CERT Australia deploy an automated platform for cyber threat intelligence sharing?
While cyber adversaries are motivated, innovative and agile, they are also rational and seek an economy of effort. If an exploit they have crafted, or infrastructure they have commandeered remains effective they are likely to continue to use that capability.
Contrary to common perceptions, we see many malicious actors continue to target vulnerabilities that have been patched for months if not years or use features of target platforms (the macro capabilities of office applications for example) to facilitate illicit access to target networks.
Presumably, as network defenders, where we can force the cost of an attack to exceed the perceived value of the system or information being targeted, this will act as a significant disincentive to those with malicious intent. By sharing indicators about the vulnerabilities, infrastructure, and tactics, techniques or procedures (TTPs) used by an adversary with other potential targets we can increase the costs (time and money) and limit the effectiveness of that actor.
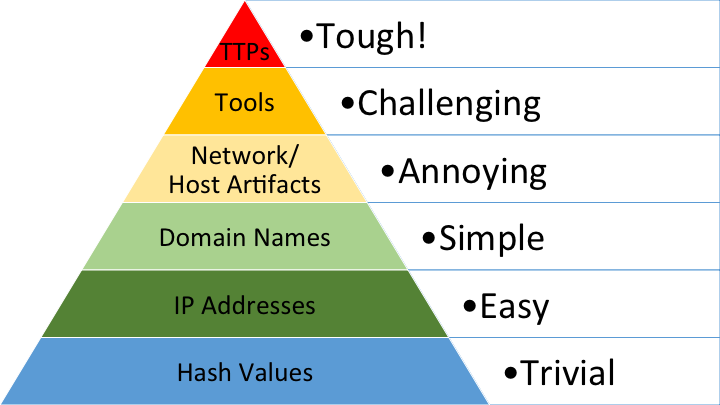
In 2013, David Bianco detailed the Pyramid of Pain. The pyramid details the types of indicators that can be shared by network defenders and the effort that an adversary would need to go to in adapting to disclosure of a particular type of indicator. As is understood by many incident response teams and indicated in Figure 1 below, the disclosures of a file hash or Internet Protocol (IP) address are trivial for an adversary to adapt to, while disclosure of characteristic TTPs requires significantly more effort, on the part of the adversary, to adapt to.
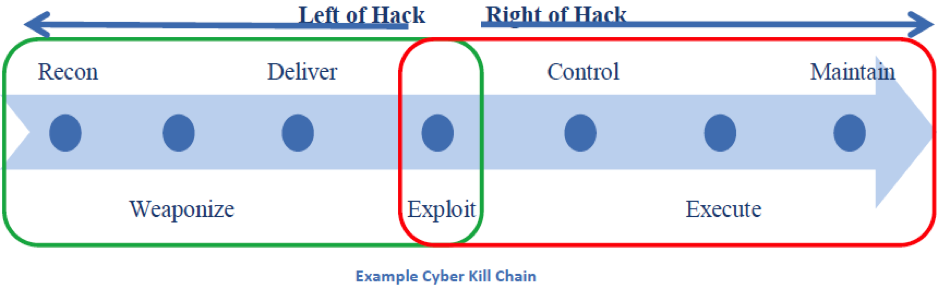
Importantly, a key factor to be aware of when discussing cyber threat intelligence as distinct from indicator sharing generally is the ability to represent the TTPs of an actor not just lists of malicious IP addresses or file hashes that may have been used at some point in time. This permits a greater focus on discovery, detection and response efforts earlier in the attack lifecycle, where network defence activity is able to have an impact left of hack (see Figure 2 below).
Automated exchange of indicators at near-real-time is also required as adversaries are attuned to the fact that the infrastructure and payloads they use may have a limited shelf life. Based on this reality, adversaries will couple the disclosure of capabilities with focused campaigns.
In recent ransomware campaigns, for example, we see domains being registered and activated merely hours before their use. Such tactics exploit the fact that there will be a window of opportunity to use this infrastructure prior to defenders being able to reconfigure the many devices in their security infrastructure.
The role for automated exchange of high fidelity, high confidence, cyber threat intelligence able to represent the breadth of adversary tradecraft is now well recognized as critically important, with some countries mandating more activity in this space (for example the US Cybersecurity Information Sharing Act 2015).
In my next post in this series, I will describe the cyber threat intelligence technologies that CERT Australia has chosen and how we have worked with our industry partners to make data from these technologies more easily available.
Jason Smith is the Technical Director of CERT Australia, Australia’s national computer emergency response team.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.