
The 24th DNS-OARC meeting was held last week in Buenos Aires – a two-day DNS workshop with amazingly good, consistent content. The programme committee are to be congratulated on maintaining a high quality of presentations.
Here are my picks of the workshop. They fall into three groups, covering themes I found interesting.
DDoS and the DNS
These presentations related to the ongoing problem of DNS as a source of reflection attacks, or a victim of attempted DDoS; although the main target is probably not the DNS top-level infrastructure, but the domain holder, or the reflection target. None the less, the DNS high-level servers (high in the tree, near the apex of delegation) see a problem and have to scale to meet it.
Recent DDoS attacks against RIPE NCC’s DNS servers – Anand Buddhdev (RIPE NCC)
Anand gave a run-down on the effects of DDoS attacks on the RIPE NCC server farm, and how it’s pushing them to upgrade capacity in links and explore their kernel IP filtering options to try and limit the damage. With only three anycast nodes, RIPE NCC feels over-exposed to risks of attacks getting ahead of their capacity and are looking to rescale service and introduce some diversity into their nameserver set. This is going to be an issue for anyone offering DNS secondary services (as the RIPE NCC do; as do other DNS service providers, often as a community benefit). Another issue is the cost of DNS hosting infrastructure is increasing.
Review and analysis of attack traffic against A-root and J-root on November 30 and December 2015 – Matt Weinberg and Duane Wessels (Verisign)
Matt’s talk was on the same problem as Anand’s but from the perspective of an Anycast DNS provider with a large investment in global and local nodes. An interesting twist on things is that some of the 13 Root DNS servers missed being attacked because the attackers relied on old information about the root server addresses. As a consequence, they were sending packets to old IP ranges, either not running the service or not routed.
That said, a significant increase in traffic was seen relating to two distinct queried hosts, probably the target of the attack. This led to some loss of service quality in smaller nodes but no overall loss of integrity in service at the root level.
As part of the presentation, Duane Wessels presented a novel use of the Hilbert curve to visualize the “walk” through source IP space from the attack over time and has made some code available for this kind of visualization of IP address data over time.
Tools aiding DNS analysis; new emerging DNS analysis activity
Real-time analytics of DNS packets – Javier Bustos-Jiménez (NICLabs)
From an earlier DNS-OARC meeting, held in Amsterdam, Javier and Nic.cl have developed a very interesting DNS measurement framework which can leverage portspan and data mirroring methods to construct a DNS analytics model. The code is available from http://ratadns.niclabs.cl/.
DNS-stats collector project – Sara Dickinson (Sinodun)
Sara presented a lightning talk on a similar development to Javier’s – the DNS-stats package which is now nearing a 2.1.0 release. This code, which relates to the hedgehog DNS measurement and charting system used in ICANN, is another open-source DNS analytics framework. It is exploring multi-backend models of data feeding other systems like DSC, and testing newer representations of packet capture and DNS packet flows as compressed data feeds.
gTLD servers data analysis – Paul Hoffman (ICANN)
Paul has begun an exploration of qualities in the gTLD space, looking at a weeks data with the intention of designing a more long-lived ongoing measurement of behaviours across the gTLD space as seen at the L-Root view.
Continuous data-driven analysis of root server system stability – Bart Gijsen (TNO)
Bart summarized the contract work TNO has taken with ICANN to measure the behaviour of the root system. This is an initiative which is leveraging a range of data sources including the DNS OARC packet captures from “DITL” and other sources of quality DNS information.
Multi-vantage point DNS diagnostics and measurement – Casey Deccio (Verisign)
Casey presented on the DNS viz tool, and some new developments which are being provided by Verisign. A “looking glass for DNS” model is capable of using the tools, which permits a debug of DNS problems as seen at other places in the ecology of server and resolver, rather than inside your own network dependencies. We use DNS viz heavily at APNIC, which has been a very good mechanism for checking DNSSEC integrity in APNIC experiments.
New emerging DNS capabilities
How we are developing a next generation DNS API for applications – Sara Dickinson
Along with Willem Toorop from NLnet Labs, Sara presented on the getDNS API. It is a significant advance on the existing DNS query interfaces, which provides a fully asynchronous, DNSSEC-aware interface at a high level. There is now a good basis for software developers to talk to getDNS, and get a better path into services backed by DANE. This work was supported by Allison Mankin from Verisign Labs, and is a significant community benefit in the open-source space.
State of the “DNS privacy” project: running code – Stéphane Bortzmeyer (AFNIC)
One of the issues with the DNS is its open visibility. QNAME minimization is an approach to removing some of the question from people who don’t need to know your specific query endpoint, and so “minimize’ the visibility of where you connect to.
Stephane reviewed the standards of the “DNS privacy” project. These are now mostly cooked; with some still in discussion, but mainly, the focus was on running code and deployment – see the implementation status below taken from the Sinodun website:
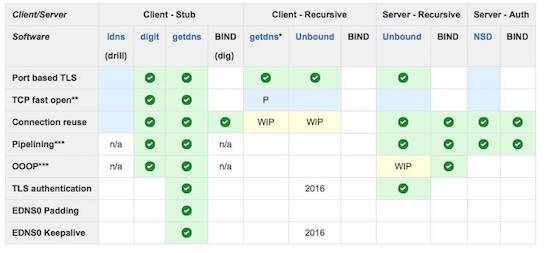
This table lists the current status of DNS-over-TLS related features in the latest stable releases of a selection of commonly used DNS software – Sinodun
Basically, QNAME minimization is in two servers. Unbound 1.5.7> Knot-Beta.unbound is off by default; knot is on by default.
There are problems in the real world, with broken authoritative servers that don’t expect to see this. They give broken “non-empty terminal” responses during exploration of the DNS to find the intermediate data. The takeaway? Running code, but at close-to-zero deployment.
Sara Dickinson did note, in getDNS API they follow the “DNS over TLS pinning-set” draft mechanism, which is part of the emerging privacy in DNS issue.
Ralph Dolmans from NLnet Labs also talked about QNAME minimization in the Unbound resolver, with a very nice and simple minimization flow diagram.
Brief, amusing and thoughtful presentations
For two lighthearted but amusing presentations, why not look at these ones:
The quest for the missing keytags – Roy Arends (ICANN)
Roy was trying to get DNSSEC key tags of specific value to play with the space – in principle, there are 65,000 key tags, and he wanted to see if he could generate keys to get two specific values. What he found was a mathematical conundrum about why he saw significantly LESS than 65,000 key tags when he ran the algorithm. In his presentation, he explored the problem as an exercise in mental arithmetic, which had most of us straining our brains to keep up with the problem.
DNS zombies – Geoff Huston (APNIC)
Geoff presented on a rather odd behaviour in the 24,000,000 unique DNS queries with 1sec TTL seen over a window in time. From his 6-month experiment, up to 50% of the queries seen were “zombies”. Given the experiments are one-time queries (everyone is a unique name) – it’s silly. This is a huge amount of wasted effort in the DNS. Over the longer baseline, around 25% of all 44 billion queries over time are zombies and 50% of the web zombies die out at 4 days. As such, the DNS zombies have a different life with no correlation web/DNS.
Read Geoff’s report on this experiment
Geoff explored who is doing the queries, and where we might find the people who need to upgrade software. For laughs, he models a simple persistent data store in the DNS with read/write but no delete, all living forever in the DNS (apparently, with some queries seen over 4 years old).
For a complete rundown on the workshop, including slides, see the DNS-OARC website and Geoff Huston’s summary of the event at APNIC Labs.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.
