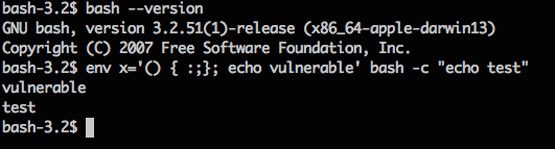
Got Bash?
The Internet is currently abuzz with news about the latest critical vulnerability that has the potential to affect many systems, for example, Linux, Unix, and Mac OS X that have Bourne Again Shell (aka Bash) installed. And you know that something serious is going on when you see remote and execute being mentioned in a single sentence. This vulnerability earned a CVSS Severity Rating of 10 out of 10 from the folk at NIST National Vulnerability Database, so this is serious.
Here’s an overview of this vulnerability from the same website (emphasis is mine of course):
GNU Bash through 4.3 processes trailing strings after function definitions in the values of environment variables, which allows remote attackers to execute arbitrary code via a crafted environment, as demonstrated by vectors involving the ForceCommand feature in OpenSSH sshd, the mod_cgi and mod_cgid modules in the Apache HTTP Server, scripts executed by unspecified DHCP clients, and other situations in which setting the environment occurs across a privilege boundary from Bash execution
Deja Vu?

Once again like the OpenSSL Heart Bleed incident or any major critical vulnerabilities affecting software that we have seen in the past, the security community is faced with a challenging task. Two things are of importance to address at this point, getting the word out so that sys admins can assess the situation and applying the relevant patch or upgrade if applicable, before the bad guys get to exploit it first.
In this region, the folks at NZITF were probably one of the first from the security response community to come up with a very straight-forward security advisory on this vulnerability – answering typical questions that system or security admins would ask.
- Is this serious? (what is the impact)
- How do I know if I am affected? (is this relevant to me)
- What are the attack vectors? (what are the ways this could be exploited; what action is required)
The advisory also included some references with regard to the technicalities. I think it is very important to have a concise advisory to help these admins get the job done.
On the topic of the OpenSSL Heart Bleed incident, we had an interesting panel discussion last week at the APNIC 38 Conference on the experience of handling critical vulnerability at the national level. The entire session was recorded and you can watch it online if you missed it. Barry (NZITF) and Megat (MYCERT) spoke about the impact the OpenSSL Heart Bleed incident had on their organizations during the first 24-48 hours. They discussed the technical and legal challenges in assessing the situation (that is: the severity of the situation) and the different methods for reaching out to their respective constituencies. Megat also highlighted that their findings a few months after the incident indicated some system owners still have not upgraded openssl despite being reminded to do so! As we are all aware, this sad scenario is not unique to the OpenSSL Heart Bleed incident only.
What I have also learned from the panel was that not only is vulnerability handling of national interest, but it takes numerous resources to translate the initial critical vulnerability announcement into something that could ultimately trigger a series of actions. So I wonder, in countries in this region where there is no national CSIRT or a community of security professionals like the NZITF, how is information about critical vulnerabilities being shared?
Please help spread the word if you can. And if you have systems affected by CVE-2014-6271 – happy upgrading!
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.
