
When most people think of cybersecurity, they picture firewalls, phishing emails, or the occasional data breach.
But zoom out for a moment — what about the Internet itself? The actual infrastructure that powers our digital lives? That’s where the real battle is happening, and it’s mostly invisible.
At the Global Cyber Alliance (GCA), we’ve spent the last decade working to make the Internet safer, not through flashy headlines, but through deep, global infrastructure work. You might not know our name, but chances are you’ve benefited from our efforts.
A simpler time, a harder problem
There was a time when banking required a branch visit, and a computer was just a box on your desk.
Today, our digital lives are infinitely more complex — and so are the threats. With complexity comes a vastly larger attack surface. That means more opportunities for bad actors to exploit weak links.
Securing today’s Internet is difficult because:
- The Internet doesn’t recognize borders.
- Infrastructure is globally distributed, but laws are locally enforced.
- Security decisions are often made in silos, without considering their ripple effects.
I’ve seen this first-hand. While travelling to Thailand, I couldn’t access my pay stub online. The site blocked Thai IP addresses — maybe for security, maybe for compliance — but the result? A broken, fragmented Internet.
This is what we mean when we talk about Internet integrity — an Internet that’s reliable, global, and consistently secure. Right now, that’s under threat.
Cybersecurity isn’t just a tech problem
Let’s look at recent headlines:
- In 2024, UnitedHealth’s Change Healthcare division led to a USD 0.92 drop in share price —seemingly minor, unless you consider how many businesses and patients were impacted by the disruption.
- A CrowdStrike software outage grounded flights worldwide. It wasn’t even a cyberattack — just a patch gone wrong.
These events highlight a hard truth — cybersecurity is no longer just a technical concern. It’s a boardroom issue. A business continuity issue. A societal risk.
What our data shows
Through its AIDE project, GCA maintains a global ‘honey farm’ — a network of decoy systems designed to attract attackers. With over 200 sensors monitoring activity around the clock, we see what others don’t.
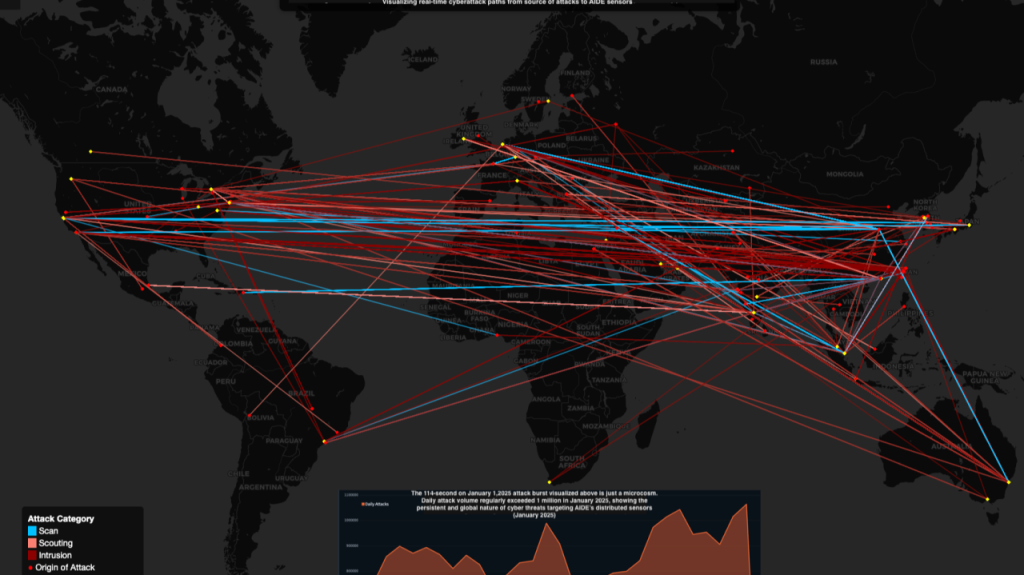
What we’ve found is alarming:
- Every single open IPv4 port is being constantly probed.
- Attacks originate from all over the world — this isn’t just random scanning, it’s coordinated.
- Compromised infrastructure is often used to attack other networks.
We’ve observed specific threats like:
- Volt Typhoon — Targeting U.S. critical infrastructure.
- Flax Typhoon — Focused on Taiwan, embedding malware in legitimate systems.
- CAPSAICIN — Exploiting outdated D-Link routers still in use globally.
What’s worse, some of this malicious activity comes from networks that don’t even know they’re compromised. That puts everyone at risk.
So, what can we do?
Here’s the good news: The Internet still works well because people have worked together.
From pushing IPv6 adoption to developing MANRS (Mutually Agreed Norms for Routing Security), collaboration has always been key to Internet health.
At GCA, we’re leaning into that spirit with our Internet Integrity Program, focusing on:
- Names (DNS).
- Numbers (IP addresses).
- Routes (BGP and routing infrastructure).
We analyse threat data, partner with infrastructure providers, and recommend actionable changes to reduce risk and fragmentation.
The core idea for addressing campaigns like Volt Typhoon? Networks need to stop bad traffic from leaving their own systems, not just worry about incoming threats.
This means:
- Identifying compromised devices.
- Hardening default configurations.
- Participating in global security norms like MANRS.
The takeaway
There is no silver bullet for Internet security. But there is a shared responsibility.
The longer we ignore outbound malicious traffic or overlook outdated infrastructure, the more we put ourselves — and others — at risk.
If you run a network, manage IT infrastructure, or influence security policy, ask yourself:
Is my organization part of the problem, or part of the solution?
Together, we can reduce the global attack surface. We can preserve the openness and reliability of the Internet. But only if we act collaboratively and proactively.
Let’s raise the bar. For everyone.
This post is a summary of Leslie Daigle’s keynote presentation at ARIN 55 in April 2025. Watch the whole presentation.
Leslie Daigle is Chief Technical Officer at Global Cyber Alliance.
Adapted from the original post on LinkedIn.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.
