
ISO/IEC 27001:2022 is the latest revision of the internationally recognized Information Security Management Systems (ISMS) standard. It provides a systematic approach to managing sensitive company information, ensuring it remains secure through a risk management process that involves people, processes, and IT systems.
Why ISO/IEC 27001 certification matters
- Risk management: Helps organizations identify, assess, and manage security risks.
- Customer trust: Enhances trust with clients, partners, and stakeholders by demonstrating a commitment to information security.
- Compliance: Assists in meeting legal, regulatory, and contractual requirements.
- Competitive advantage: Differentiates your organization by showing adherence to globally recognized standards.
A step-by-step guide to ISO/IEC 27001:2022 certification
In this post, I will give detailed information to guide you through the ISO 27001 certification process, from getting ready to conduct an internal audit to final certification. Bear with me on all these steps, and if you find anything interesting to add, feel free to do it in the comments box.
Step 1: Understanding the requirements
Before diving into implementation, it’s crucial to understand what ISO/IEC 27001:2022 requires. This includes familiarizing yourself with the following key components:
- Annex A controls: A list of around 93 security controls divided into four domains — organizational, people, physical, and technological.
- Context of the organization: Understanding the external and internal issues that can affect the ISMS.
- Leadership and commitment: The role of top management in establishing and maintaining the ISMS.
- Risk assessment and treatment: Identify information security risks and define how to manage them.
- Performance evaluation: Monitoring, measuring, analysing, and evaluating the ISMS performance.
- Continuous improvement: Updating and refining the ISMS to respond to the evolving security landscape.
Use case: A large healthcare provider starts by studying Annex A controls to ensure patient data protection aligns with the specific controls required for sensitive health information, such as encryption and access control. The leadership team conducts a workshop to understand how the broader context, including regulatory requirements like HIPAA, impacts their ISMS.
Step 2: Securing management support
ISO 27001 certification requires significant time, effort, and resources. Therefore, securing management support is essential. Top management must:
- Allocate resources: Ensure the availability of resources, both human and financial.
- Define roles and responsibilities: Clearly outline who is responsible for what within the ISMS framework.
- Promote a security culture: Lead by example to create an organization-wide commitment to information security.
Use case: A financial services firm seeking ISO 27001 certification secures executive buy-in by presenting the benefits of accreditation during a board meeting. The CFO allocates a budget for hiring a consultant and the necessary tools. The CEO sends a company-wide memo highlighting the importance of information security and announcing the initiative.
Step 3: Conducting a gap analysis
A gap analysis helps to determine the current state of your organization’s information security practices compared to ISO 27001 requirements. This involves:
- Reviewing existing policies and procedures: Identify any policies that are missing or need to be updated. If not, build one based on asset inventory and related components.
- Assessing risk management processes: Determine if your current risk management practices meet ISO 27001 standards.
- Evaluating security controls: Assess the effectiveness of existing security controls and identify areas for improvement. Build a team to do this and report accordingly.
Use case: A tech startup uses a gap analysis template to compare its security practices with ISO 27001 standards. They discovered that their incident response plan needed more comprehensive and formal documentation, including the report format, the responsible person, and the team handling the incident response. This prompts the development of a more robust incident response strategy.
Step 4: Defining the ISMS scope
Clearly defining the scope of your ISMS is crucial for effective implementation. The scope should include:
- Assets to be protected: Determine which information assets fall under the ISMS.
- Boundaries: Define the physical and logical boundaries of the ISMS.
- Stakeholders: Identify internal and external stakeholders interested in your ISMS.
- Dependencies: Consider any dependencies on third-party services or infrastructure.
Use case: An international manufacturing company initially defines the ISMS scope to include only its European operations, where GDPR compliance is critical. They focus on protecting customer data, intellectual property, and operational data in their European facilities and decide to expand the scope later to include global operations.
Step 5: Developing an ISMS policy
An ISMS policy outlines the organization’s approach to managing information security and sets the direction for the ISMS. Key components include:
- Information security objectives: Define clear, measurable security objectives aligned with business goals.
- Risk management strategy: Outline how risks will be identified, assessed, mitigated, and documented in the risk registry.
- Roles and responsibilities: Specify the roles of employees and management in maintaining the ISMS.
- Compliance requirements: Include references to legal, regulatory, and contractual obligations.
Use case: A SaaS company drafts an ISMS policy with objectives like achieving near-zero security incidents and maintaining 99.9% uptime. They align these objectives with customer SLAs and regulatory compliance (for example, GDPR for European customers). The policy is reviewed and approved by the company’s CISO.
Step 6: Conducting a risk assessment
Risk assessment is a critical part of ISO 27001. It involves:
- Identifying assets: Catalogue all information assets, including data, software, hardware, and personnel.
- Identifying threats and vulnerabilities: Assess potential threats and vulnerabilities impacting these assets.
- Evaluating risks: Analyse the likelihood and impact of identified risks.
- Risk treatment plan: Develop a plan to treat identified risks, which could involve avoiding, transferring, mitigating, or accepting the risk.
Use case: A university’s IT department performs a risk assessment focused on its online learning platforms. They identify the risks of unauthorized access, data breaches, and Distributed Denial-of-Service (DDoS) attacks as significant threats. The department develops a risk treatment plan that includes upgrading its firewall, implementing Multi-Factor Authentication (MFA) for students and faculty, and deploying DDoS handling services.
Step 7: Implementing security controls
Once risks have been identified, you must implement appropriate controls from Annex A or custom controls suited to your environment. This includes:
- Technical controls: Firewalls, encryption, access control systems, intrusion detection systems, and more.
- Organizational controls: Security policies, employee training, incident response plans, and so on.
- Physical controls: Secure locations, access controls, environmental controls, and so on.
Use case: A retail company implements encryption for all customer data stored on its servers. It also establishes organizational control by conducting regular employee training on recognizing phishing attempts, a common threat identified during its risk assessment.
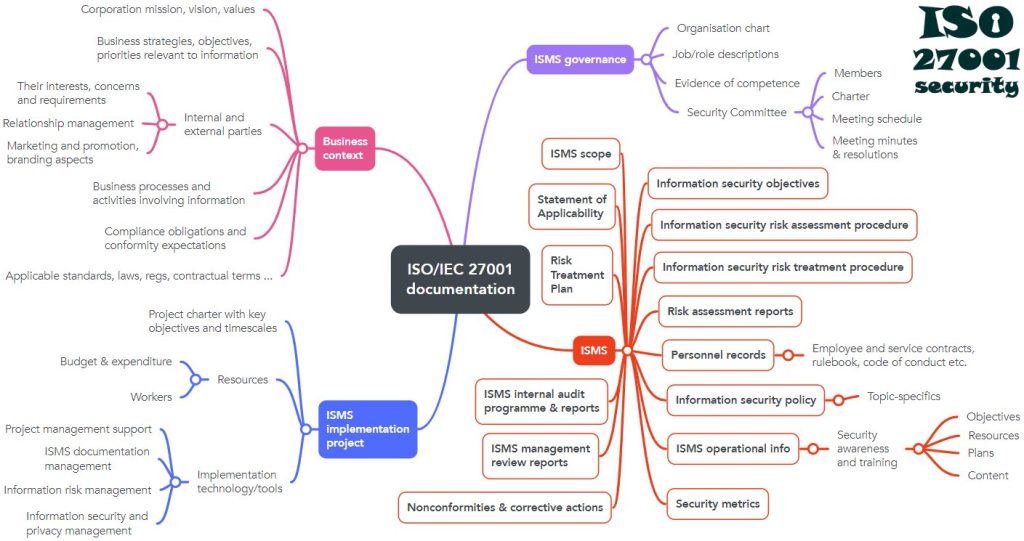
Step 8: Developing documentation
Documentation is a significant part of ISO 27001 compliance. Essential documents include:
- ISMS policy
- Risk assessment report and risk registry
- Statement of Applicability (SoA): Lists all controls and justifies their inclusion or exclusion.
- Risk treatment plan
- Security procedures: Documented procedures for critical security activities.
- Internal audit reports: Records of internal audits conducted to ensure compliance.
Use case: A global logistics company uses a document management system to store all required ISMS documentation. They maintain detailed records of their risk assessments, SoA, and security procedures, ensuring they are easily accessible for internal audits and external review, along with the version control of all those documents.
Step 9: Training and awareness
For the ISMS to be effective, all employees need to be aware of their roles and responsibilities regarding information security. This involves:
- Training programs: Regular training sessions on information security policies, procedures, and best practices.
- Awareness campaigns: Ongoing communication about the importance of information security.
- Role-based training: Specific training for employees with security-related responsibilities.
Use case: A healthcare provider implements a mandatory training program for all staff, including modules on handling patient data securely, understanding phishing threats, and responding to security incidents. IT staff receive additional training on the technical controls and protocols specific to their roles.
Step 10: Monitoring and reviewing the ISMS
Continuous monitoring and regular review of the ISMS are essential for its success. This includes:
- Internal audits: Regularly scheduled audits to check compliance with ISO 27001.
- Management reviews: These are periodic reviews by top management to assess ISMS performance and address any issues, as well as to get permission and signal any changes in the policy and practices.
- Continuous improvement: Identifying opportunities for improvement and implementing corrective actions.
Use case: A telecommunications company schedules quarterly internal audits of their ISMS, focusing on different aspects each time, such as access controls or incident response. After each audit, the management team reviews the findings, and any identified issues are addressed through corrective actions.
Step 11: Conducting an internal audit
Before the certification audit, conduct a thorough internal audit to identify and address any non-conformities. Steps include:
- Planning the audit: Define the audit’s scope, objectives, and criteria.
- Conducting the audit: Review documentation, interview staff, and assess the effectiveness of controls.
- Reporting findings: Document any non-conformities and create an action plan for remediation.
- Follow-up: Verify that corrective actions have been implemented.
Use case: An e-commerce platform conducts an internal audit focusing on its data encryption and customer data protection practices. The audit uncovers that some encryption protocols need to be updated. The company updates these protocols and documents the corrective actions in its ISMS records.
Step 12: Preparing for the certification audit
Once your ISMS is fully implemented and you’ve conducted an internal audit, you can prepare for the certification audit:
- Choose a certification body: Select an accredited certification body specializing in ISO 27001.
- Stage 1 audit (documentation review): The auditor will review your ISMS documentation to ensure it meets ISO 27001 requirements.
- Stage 2 audit (on-site audit): The auditor will assess the effectiveness of your ISMS in practice. This includes interviews, process reviews, and control testing.
- Addressing non-conformities: If any non-conformities are identified, address them promptly and provide evidence to the auditor.
Use case: A software development company chooses a certification body with experience certifying technology firms. During the Stage 1 audit, the auditor reviews the company’s ISMS documentation and identifies that some controls related to third-party data processing need more detail. The company updates the documentation before the Stage 2 audit, where the auditor visits their office, interviews staff and verifies the implementation of controls.
Step 13: Achieving certification
If your organization successfully passes both audit stages, the certification body will issue an ISO 27001 certificate. This certificate is valid for three years, during which surveillance audits will be conducted annually to ensure continued compliance.
Use case: A cloud services provider receives their ISO 27001 certification after successfully passing the audit stages. They proudly display the certification on their website and use it as a competitive advantage in marketing materials, helping to win new contracts with businesses concerned about data security.
Step 14: Maintaining and improving the ISMS
ISO 27001 is not a one-time effort. It requires ongoing maintenance and improvement. To maintain certification:
- Conduct regular audits: Ensure continuous compliance through regular internal and external audits.
- Update the risk assessment: Regularly review and update the risk assessment to account for new organizational threats or changes.
- Review policies and procedures: Continuously review and update security policies and procedures.
- Engage in continuous improvement: Use the Plan-Do-Check-Act (PDCA) cycle to make incremental improvements to the ISMS.
Use case: A large multinational corporation regularly updates its ISMS based on changes in the threat landscape, such as the rise of ransomware. They conduct semi-annual internal audits to ensure all offices worldwide are compliant with ISO 27001 and use the findings to continuously improve their security posture.
Practical resources and tools
Here are some practical resources to help you through the ISO/IEC 27001:2022 certification process:
- Free ISO 27001 checklist: High Table offers a free, no-signup-required ISO 27001 checklist in XLS and PDF formats. This checklist is designed to cover all aspects of the ISO 27001:2022 standard, helping you ensure that all necessary steps and documentation are in place.
- ISO 27001 documentation repository: This repository offers useful templates and working documents for implementing ISO 27001. It includes resources for internal audits, risk management, and management reviews, helping you maintain compliance with the standard.
- ISO 27001 toolkit: The ISO 27001security.com toolkit includes various resources, such as a gap analysis questionnaire, mandatory documentation checklists, and other tools essential for implementing and maintaining an ISMS according to ISO 27001:2022.
These resources will provide the practical tools and templates needed to streamline your ISO 27001 implementation and ensure that your organization is well-prepared for certification.
Conclusion
Achieving ISO/IEC 27001:2022 certification is a rigorous process that requires commitment from all levels of an organization. By following this step-by-step guide and utilizing the practical resources provided, your organization can systematically approach the implementation of an ISMS, mitigate risks, and enhance your overall security posture.
Remember, the certification journey is not just about achieving a certificate but about embedding information security into the fabric of your organization, thereby ensuring the confidentiality, integrity, and availability of your information assets.
Shamim Reza is the Chief Technology Officer at cybersecurity service provider Pipeline and the founder of TheTeamPhoenix, a non-profit initiative dedicated to enhancing the community’s well-being in cybersecurity and technology. He’s also an APNIC Community Trainer dedicated to knowledge support in the APAC region.
Originally published on A. S. M. Shamim Reza’s Medium.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.
