
Internet-wide scanning is an important tool for understanding network behaviour and security. However, as the adoption of IPv6 grows, the studies of scanning activities remain less comprehensive compared to IPv4.
The differences between scanning activities in IPv4 and IPv6 networks are significant. In IPv4 networks, exhaustive scanning tasks are relatively straightforward with modern tools like Zmap.
However, in IPv6 networks, the task of scanning is non-trivial due to the vast address space and sparsely populated hosts. Despite the challenge, scanning activities in IPv6 are still prevalent according to recent studies.
In this blog post, we will introduce our research presented at the Passive and Active Measurement Conference 2024, ‘Exploring the Discovery Process of Fresh IPv6 Prefixes: An Analysis of Scanning Behavior in Darknet and Honeynet‘, where my fellow researchers and I studied the characteristics of scanning activities and the process of fresh prefix discovery in the IPv6 network.
Measuring scanning activities
To measure scanning activities on the Internet, network telescopes or ‘darknets’ are commonly used. Researchers monitor traffic in unused network prefixes to capture scan traffic (1, 2, 3). Darknets are passive, as they do not interact with the scanners. Recently, researchers have also started using responsive network telescopes, or honeynets, which emulate the behaviour of real hosts by responding to scan traffic (1, 2, 3). Responsive honeynets typically attract more scan traffic compared to darknets.
We developed a scan detection system incorporating both passive darknets and responsive honeynets to study the characteristics of scan activities.
Attracting IPv6 scanning
Unlike IPv4, deployed services in IPv6 do not receive scan traffic unless they are explicitly exposed. Fresh IPv6 services and prefixes initially receive only minimal scan traffic, making IPv6 inherently more secure.
However, scanners actively search for potential targets, often using seeds from services like Network Time Protocol (NTP) and DNS or the public IPv6 hitlist, which contains the active prefixes and responsive addresses in the IPv6 network.
To analyse scanning behaviour, we attract scan traffic to our detection system by implementing address-exposing methods using our DNS authoritative server.
We employed four different DNS-based address-exposing methods:
- IPv4 reverse: We mapped both IPv4 and IPv6 addresses to the same domain. IPv4 scanners performing reverse lookups would discover the IPv6 address of the domain.
- IPv6 enumeration: We registered IPv6 addresses to PTR records, allowing scanners to traverse the domain tree with ‘NXDOMAIN’ semantics and discover existing IPv6 addresses.
- Special IPv6 addresses: We registered notable IPv6 addresses (for example, ‘wordy’ addresses like
2001:db80::cafe) to the pointer (PTR) records. - Popular service names: We registered domain names with popular service names (for example.,
admin.example.com) to the AAAA records.
Our findings showed that only the IPv4 reverse method successfully attracted significant scan traffic compared to the baseline, unexposed prefixes.
Observing IPv6 scan traffic
By exposing our experiment prefix to the Internet, we successfully attracted IPv6 scan traffic. When we responded to scans from the Hitlist project, our prefixes and addresses were added to the Hitlist around two weeks after deployment. We refer to the period from initial exposure to Hitlist registration as the address-exposing phase.
After being added to the Hitlist, we received an increasing amount of scan traffic from various scanners, which we refer to as the scan attraction phase. We observed a large-scale scan campaign during this phase from July to September 2023.
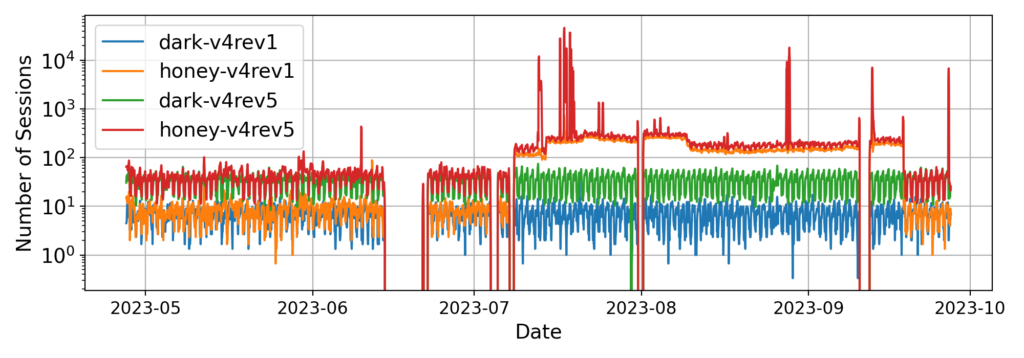
Types of scanners
We identified different types of scanners:
- Hitlist scanners: These scanners focus on responsive addresses from the Hitlist attempting to exploit them.
- Balanced scanners: These scanners probe the entire prefix, sending nearly equal traffic to both the darknet and honeynet, typically at a low but stable rate. This type of scanner includes research institutions (for example, Leibniz-Rechenzentrum) and cybersecurity companies (such as Constantine Cybersecurity).
- Active host scanners: These scanners probe both the darknet and honeynet but perform concentrated scans on responsive addresses in the honeynet and nearby addresses, likely searching for new potential targets.
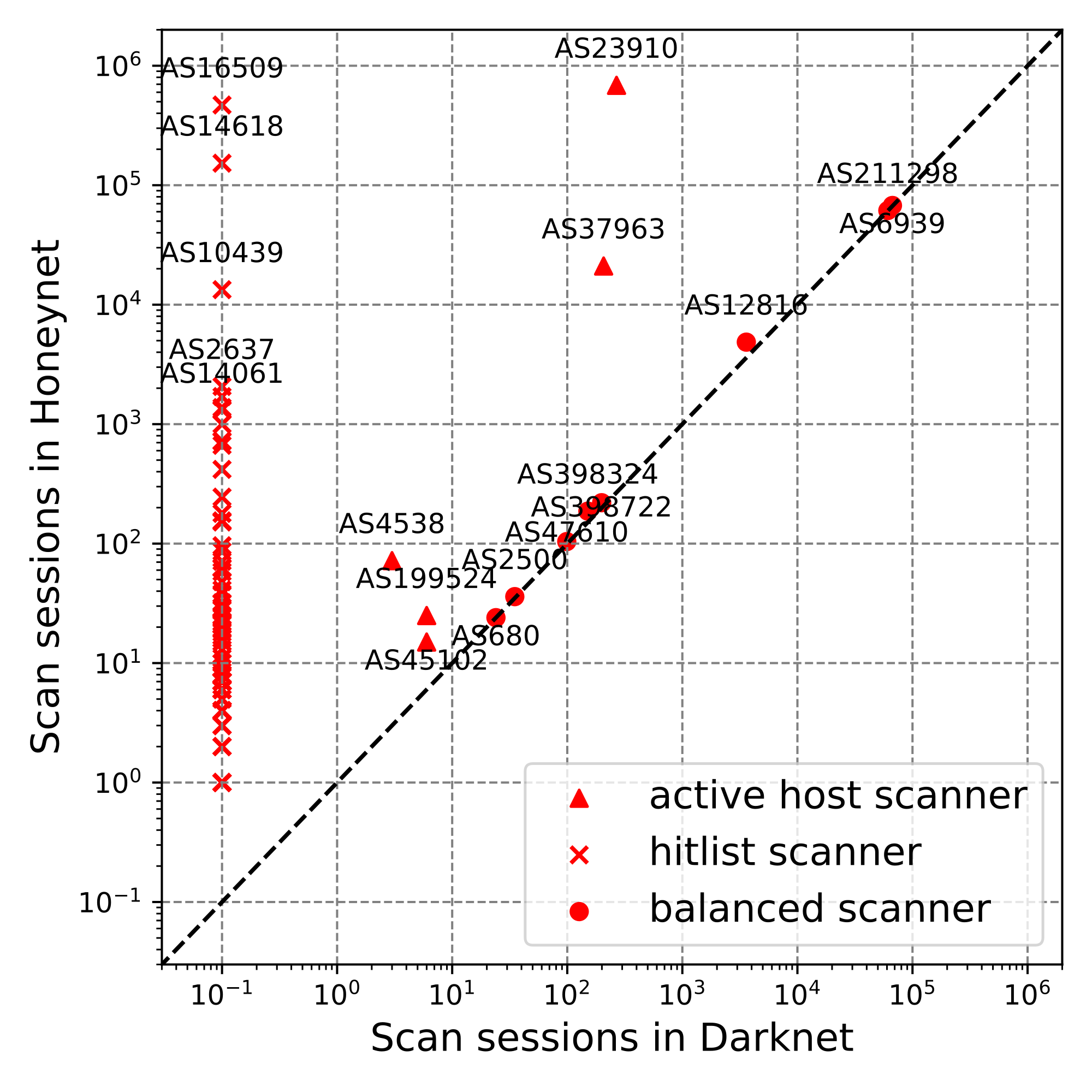
Conclusion
Our observations validate the process of a fresh IPv6 prefix from initial exposure to the Internet to attracting follow-up scans. Mapping IPv4 and IPv6 to the same domain name effectively attracts scan traffic, while simply registering IPv6 addresses to PTR and AAAA records on the DNS server did not attract much. Once exposed to the Internet, honeynets responding to scan queries attract more scan traffic than passive darknets. By analysing different scanning patterns, we inferred potential intentions behind the scanning activities.
I would like to thank my supervisor Kensuke Fukuda and my co-author Satoru Kobayashi for their contributions to this work.
Liang Zhao is a PhD student at Sokendai, Tokyo, Japan. His research interests include IPv6, network measurement, and traffic analysis.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.
