
DNS-based reflection has been misused as an attack vector in Distributed Denial-of-Service (DDoS) attacks for a long time. In a traditional reflection scenario, there is a one-to-one map in terms of the number of queries and responses. Thus, attackers leverage protocol-specific features to amplify the reflected traffic (bandwidth) as much as possible. A common example is to misuse ANY queries in combination with DNSSEC.
Recent research (‘Routing Loops as Mega Amplifiers for DNS-Based DDoS Attacks‘) has shown that bandwidth amplification is not the only way to saturate the resources of a target. A phenomenon, which we call echoing behaviour in our paper, triggers multiple responses for a single query, thus causing packet amplification. This can be leveraged to further amplify the power of reflection-based DDoS attacks.
In a collaboration among researchers from the University of Twente, the Université Grenoble Alpes, and the University of Sydney, we dived deeper into studying diversities among echoing DNS responses. We issued DNS queries for a domain name under our control toward all routable IPv4 addresses and captured the incoming queries on our authoritative nameserver and responses returned to our scanner.
In this post, we highlight some of our key findings and refer you to our paper for more details. Another independent recent study (‘On Blowback Traffic on the Internet‘) investigates this phenomenon from a different perspective by studying other networking protocols next to DNS.
Underlying causes of echoing behavior
Two known causes behind echoing resolvers are routing loops and middleboxes. In routing loops, an error in the convergence of the routing algorithm causes packets to loop. Middleboxes are instead known to manipulate packets and responses, at times causing packet amplification. In our research, we identified a third cause, which is directed broadcasting.
Directed broadcast
Contrary to the limited broadcast, which is bound to the local network of its origin, directed broadcast packets are treated as unicast packets by intermediate routers and traverse the Internet till they reach their destination network. If directed broadcast is permitted by the edge router of the destination network, hosts in that network might take action on this packet and send responses toward the source. RFC 2644 states that routers MUST block the receipt and forwarding of directed broadcast packets by default. However, this can be enabled if needed.
Considering that we do not possess knowledge regarding the topology of destinations that we probe, it is not possible to ensure that a remote address is assigned as a broadcast address. However, there are a number of observations that we use to attribute some echoing resolvers to directed broadcasts.
First, there is a one-to-one mapping between the number of responses that we get and the number of source IPs generating these packets (see the diagonal pattern in Figure 1). Second, the last octet for most of these IP addresses are numbers like 255, 127, 63, and 31, which are typically assigned as broadcast addresses. Third, the set of responding hosts excludes the queried destination itself, which is also relatable to IP broadcasting.
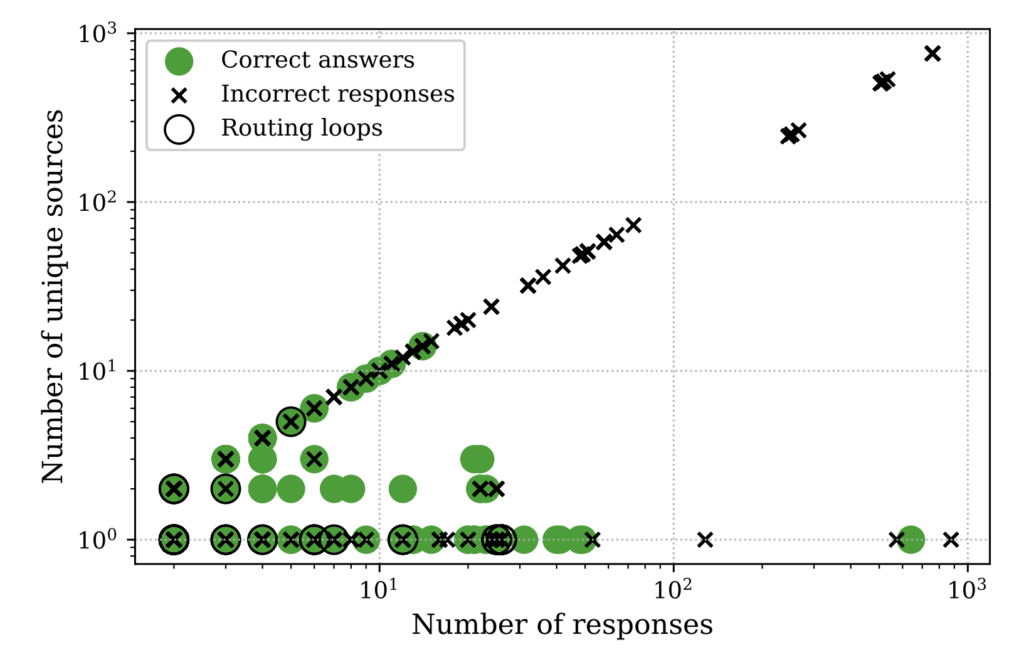
DNS censorship middleboxes
While we know that middleboxes partially play a role in echoing behaviour, our measurements so far were for a neutral domain name under our control, and we didn’t expect to trigger middleboxes yet. In order to quantify the impact of middleboxes, we issued DNS queries for a domain name that embeds a sensitive keyword as a label. For this purpose, we used facebook.com as a label under our controlled domain name. We chose facebook as a keyword since it is reported in the literature to be widely blocked by interception middleboxes.
The outcome was a surprise. Not only did the number of echoing resolvers increase from around 14k to roughly 1.68M, but also a group of high-profile echoing resolvers emerged that have a packet amplification factor of up to around 30k times (see Figure 2), all located in a single network, namely AS4538 (China Education and Research Network Center). Finally, the majority of the newly emerged echoing resolvers are geo-located to China, which suggests that the Great Firewall of China could be responsible for this behaviour.
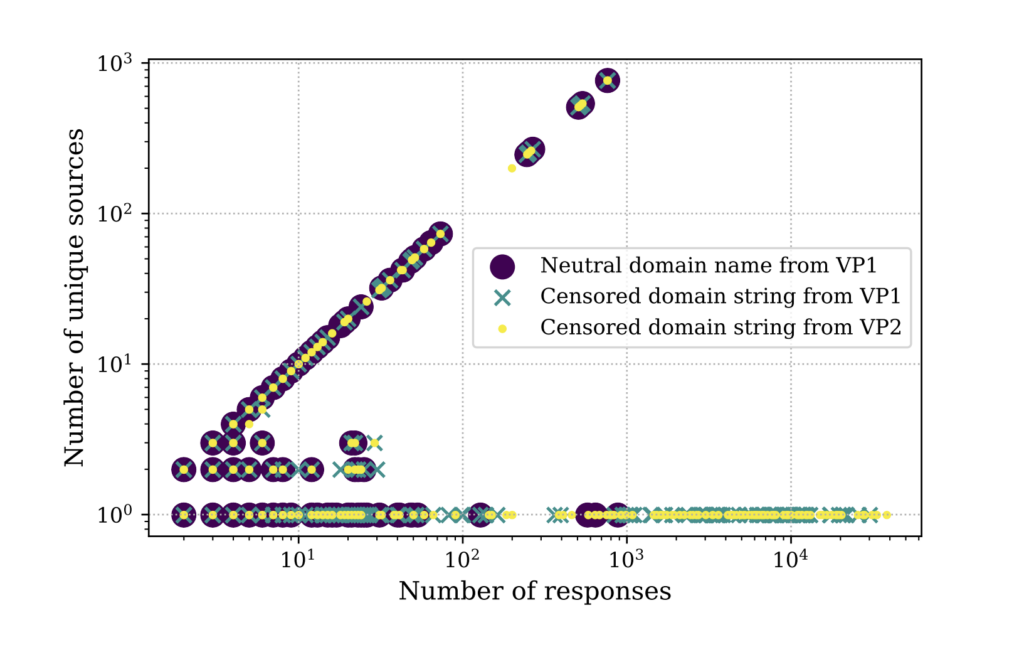
Previous studies show that middleboxes treat certain DNS query types differently. We ran measurements using A, AAAA, TXT, MX, and CNAME record types to investigate this. We found out that AAAA queries result in slightly more echoing behaviour compared to other query types. This increase is mainly caused by three Autonomous Systems, AS4538, AS4837, and AS4134, all geolocated in China.
Persistence over time
In order to misuse echoing resolvers, attackers either need to run rediscovery scans, or reuse the previously discovered resolvers. The former is an additional overhead and increases the chance of being detected by security systems. The latter, however, means that as time passes, a number of resolvers will disappear, for example, due to IP churn. Thus, as an attacker, echoing resolvers with a long lifetime are an ideal target.
We studied echoing resolvers over a time period of 74 weeks and noticed that a small percentage (~5%) of resolvers were persistently active during the entire measurement period. Although these resolvers make up a small percentage of the complete set, in absolute numbers they are substantial enough to be exploited by attackers. They would redeem an attacker from frequent rediscovery scans.
Vulnerability disclosure
As a final step, we notified the operators of broadcast-associated echoing resolvers that triggered more than 10 responses for each query. We received a number of replies (either automated or manual), some asking for more details to reproduce the issue. We provided those network operators with additional information. Although we did not receive confirmation from network operators regarding our notification, the fact that we observed fixes in a number of those networks during our follow-up measurements suggests that operators took action on our disclosure.
Conclusion
Echoing resolvers extend the boundaries of DNS amplification by multiple orders of magnitude. We show that various factors play a role in the efficacy of echoing responses in the context of DDoS attacks.
While little is known about the actual abuse of echoing reflectors in DDoS attacks, ongoing research and cooperation between researchers and network operators remains crucial in safeguarding against emerging DDoS attack vectors.
Ramin Yazdani is a PhD student at DACS research group (Design and Analysis of Communication Systems) at the University of Twente, the Netherlands. His main research interests are network measurements, DDoS, and DNS.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.
