
A fundamental vulnerability in the Network Processing Unit (NPU) chipset has been uncovered recently, which can be exploited by attackers to eavesdrop on data transmitted over a wireless network, affecting over 89% of real-world Wi-Fi networks.
Hardware acceleration is a widely adopted technique in various domains. For instance, in Wi-Fi networks, Access Point (AP) routers may use the NPU chipset to directly transmit wireless frames to the destination, which can reduce the interaction latency with the upper level of the network protocol stack and significantly improve the data transmission rate. However, such hardware-assisted techniques also bring potential security concerns.
A security flaw in the NPU’s wireless frame forwarding procedure was recently discovered by my fellow researchers from Tsinghua University and George Mason University. The flaw can be leveraged by attackers to launch a Man-in-the-Middle (MITM) attack on Wi-Fi networks without the need for rogue APs. This attack can bypass link layer security mechanisms like WPA3 and intercept a victim’s plaintext traffic. Our research paper detailing the attack has been accepted by the 2023 IEEE Symposium on Security and Privacy.
Figure 1 illustrates the scenario where an attacker and a victim supplicant are connected to the same Wi-Fi network to access Internet services. Imagine accessing the Wi-Fi network of Starbucks, for example, after passing the phone authentication. The target Wi-Fi network is secured with WPA2 or WPA3, and each session to the AP router is safeguarded with the Pairwise Transient Key (PTK) session key.
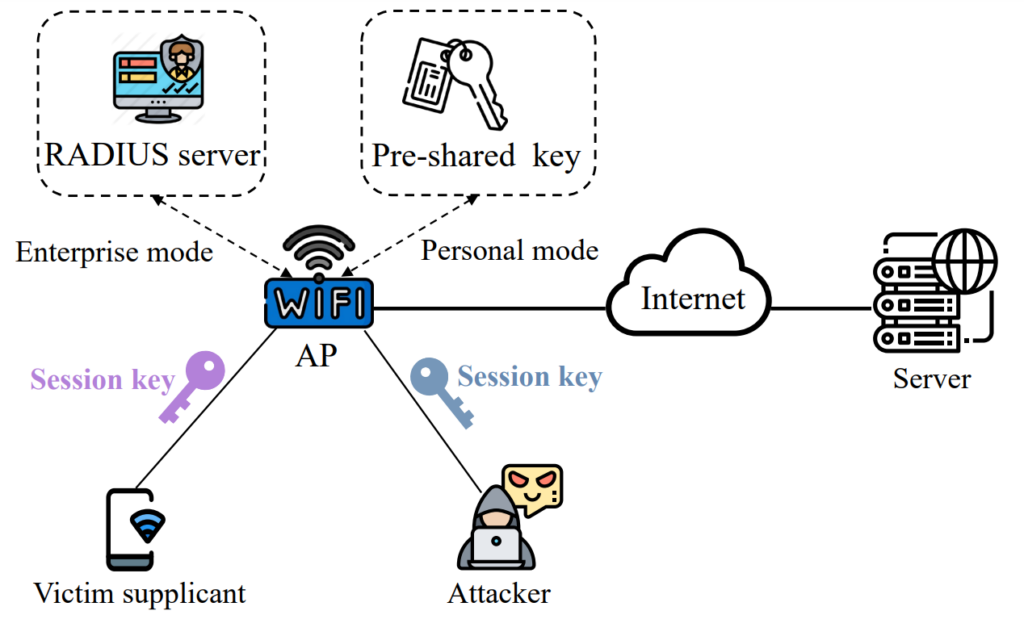
We discovered that the security mechanisms (such as WPA2 and WPA3) can be easily circumvented, enabling attackers to intercept the victim supplicant’s traffic in plaintext. The attacker impersonates the AP by spoofing the source IP address and sends an ICMP redirect message (an ICMP error message with type=5) to the victim supplicant.
Due to the performance consideration, the NPU (for example, Qualcomm IPQ5018 and HiSilicon Gigahome Quad-core) in the AP router will directly forward the received fake message of ICMP redirects to the victim supplicant. Upon receiving the message, the victim supplicant will be tricked into updating its routing cache and replacing the next hop to the server with the attacker’s IP address. As a result, subsequent IP packets intended for the server are routed to the attacker at the IP layer, allowing the attacker to forward the packets. The attacker successfully executes a MITM attack that can silently intercept and modify the victim supplicant’s traffic, all without using any rogue AP.
Qualcomm and Hisilicon have confirmed the vulnerability in their NPUs that prevents AP devices from blocking forged ICMP redirect messages. Qualcomm has assigned CVE-2022-25667 to this issue.
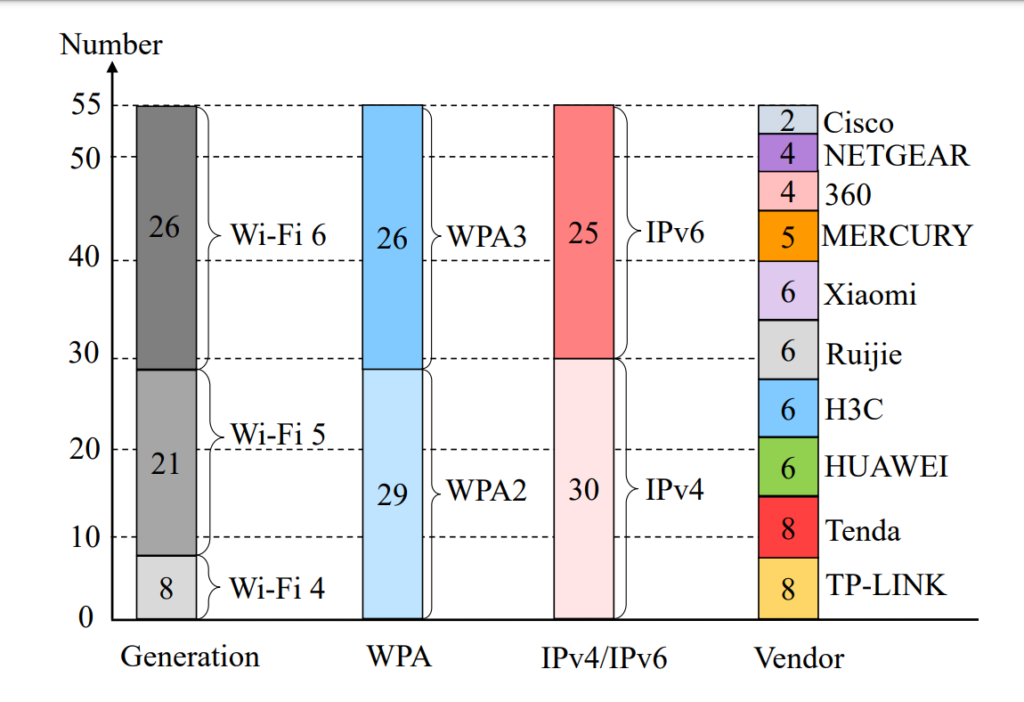
In a large-scale empirical study of mainstream AP routers and affected real-world Wi-Fi networks, we found that nearly all mainstream AP routers are affected due to the vulnerability in the embedded NPUs. Figure 2 depicts the 55 vulnerable AP routers tested from 10 well-known AP vendors. In addition, we tested 122 real-world Wi-Fi networks and discovered that 109 (over 89%) of them were susceptible to the identified attacks.
Mitigation
To mitigate this attack, the researchers suggest two countermeasures:
- Enhancing APs to throttle the crafted ICMP redirects. If the message has obvious illegal characteristics (for example, the source IP address of the message is specified with the AP’s IP address, and the message can only be generated by the AP itself), then the message should be blocked and discarded by the AP. This approach relies on the collaboration between the NPU chip manufacturers and the AP vendors.
- Enhancing supplicants to check the received ICMP messages. By checking the consistency of the received ICMP message’s source IP address and source MAC address, the supplicant can effectively identify fake ICMP messages and defend against this attack.
More details about the work are described in the paper. View a video demonstration of the attack below:
Xuewei Feng works on network security from a large-scale Internet measurement perspective.
This post and paper were co-authored by Qi Li, Yuxiang Yang, Kun Sun, and Ke Xu. Qi Li is an associate professor at Tsinghua University. His research interests are in network and system security. Yuxiang Yang is a PhD student. His research interests are network security and program analysis. Kun Sun is a professor at George Mason University. His research focuses on systems and network security. Ke Xu is a professor at Tsinghua University. His research focuses on Internet architecture and network security.
Discuss on Hacker NewsThe views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.

Interesting work, maybe we should turn off the ICMP redirect function of the OS when connecting to WIFI
bagaimana cara mematikan fungsi ICMP ?