The DNS root is the starting point of the domain name space. To mitigate against denial-of-service (DoS) attacks and improve stability, all 13 root servers are deployed using anycast with multiple root server instances. In 2022, more than 1,600 root server instances were operating across the globe, which is 56% more than 2020.
While the number of DNS root server instances has been growing, there has been little understanding of their practical effect, for example, which networks are within their catchment area, which networks are still underserved by close instances, and how they are absorbing DNS root queries from nearby resolvers. My colleagues and I at Tsinghua University recently sought to close this knowledge gap from the perspective of the 16 root server instances deployed in the Chinese mainland (December 2020), including four F-Root, one I-Root, two J-Root, three K-Root and six L-Root servers (which we refer to as ‘domestic instances’).
- Many local root queries are turning to instances beyond the international gateway, despite there being 16 closer domestic instances.
- Domestic instances are effectively serving networks within their catchment area with lower delay.
- Deploying domestic instances or recursive resolvers lowers query delay; the corresponding root servers are preferred by DNS recursive software.
The catchment area of root server instances in the Chinese mainland is limited
To begin with, we measured the catchment area of domestic instances, that is, whether they can serve root queries originating from domestic networks. Our methodology leveraged the well-known DNS censorship mechanisms, which provide side-channel information about whether DNS queries (for censored domains) pass through the international gateway (Figure 1).
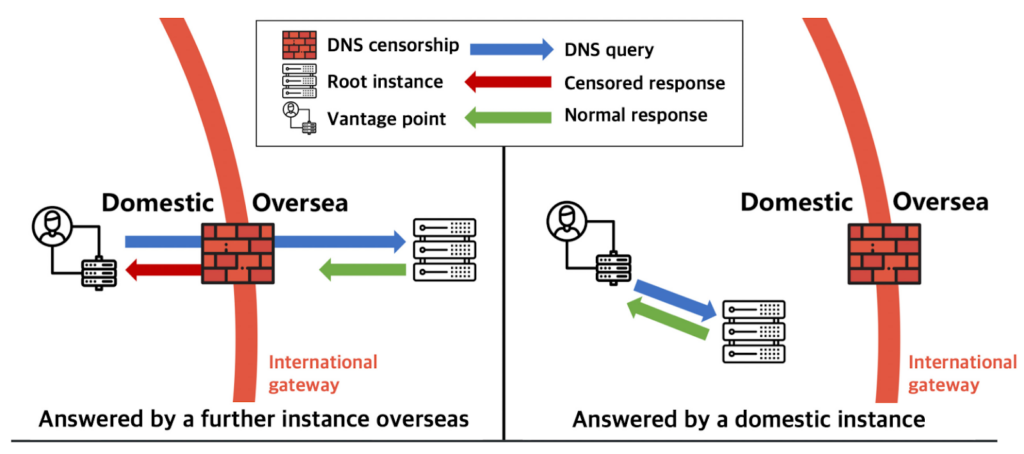
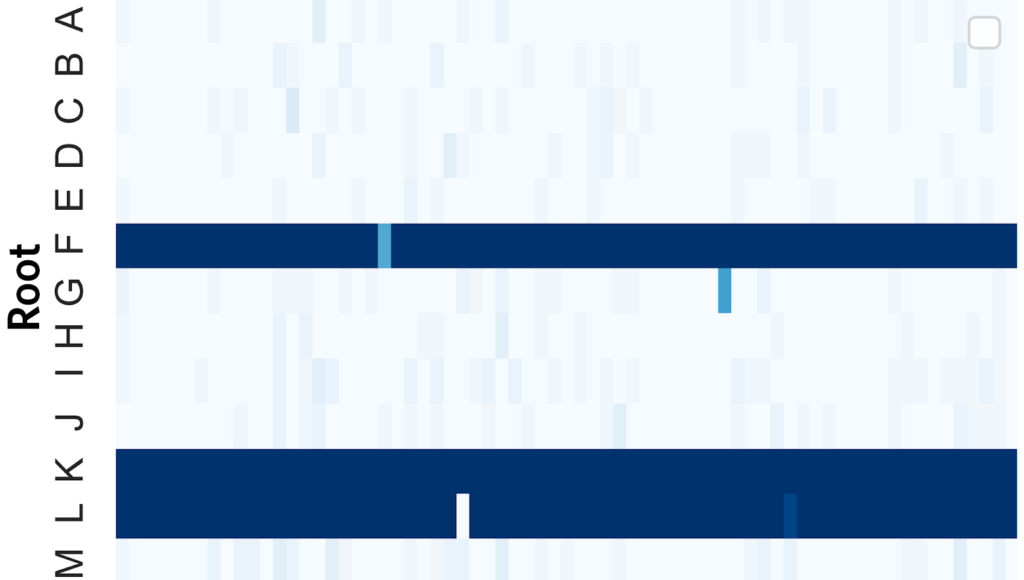
Table 1 shows the overall fraction of root DNS queries that are resolved by domestic instances from the vantage points of four major Chinese ISPs.
| Root | Telecom | Unicom | Mobile | CERNET |
| A-Root | 0.80% | 0.50% | 2.36% | 100.00% |
| B-Root | 0.94% | 2.79% | 2.08% | 100.00% |
| C-Root | 1.22% | 3.29% | 1.25% | 100.00% |
| D-Root | 0.85% | 0.95% | 5.69% | 100.00% |
| E-Root | 0.70% | 0.00% | 1.81% | 100.00% |
| F-Root | 99.34% | 3.24% | 1.53% | 100.00% |
| G-Root | 1.78% | 0.99% | 6.11% | 100.00% |
| H-Root | 0.85% | 2.43% | 2.22% | 100.00% |
| I-Root | 1.69% | 0.09% | 6.81% | 100.00% |
| J-Root | 1.27% | 98.24% | 23.47% | 100.00% |
| K-Root | 100.00% | 98.29% | 2.22% | 100.00% |
| L-Root | 98.50% | 98.38% | 95.83% | 100.00% |
| M-Root | 2.02% | 0.05% | 0.00% | 100.00% |
| Total | 23.84% | 23.79% | 11.65% | 100.00% |
Table1 — Fraction of root queries resolved by domestic instances. Root servers with domestic instances are marked with lighter backgrounds.
All queries from the China Education and Research Network (CERNET) are resolved domestically (even for root servers without a domestic instance, like the A-Root), which is expected because an unauthorized root server is working for this network. It is also notable that the catchment area of domestic instances does not cover the entire Chinese mainland, for example, only 3.2% of queries from China Unicom to F-Root are resolved domestically.
Figure 2 focuses on the fraction for each vantage point. In general, the domestic instances either serve one ISP network or not at all (for example, domestic F-Root instances can serve subscribers of China Telecom but not China Unicom or China Mobile). Combined with discussions with ISPs and DNS root operators, we confirmed that root instances in the Chinese mainland are typically advertised from ISP networks instead of Internet Exchanges (IXs). Besides, the BGP routing policies among ISPs are limited. In the end, we concluded that many root queries are still turning to further instances beyond the international gateway, despite there being 16 closer domestic instances.
Figure 2 — Ratio of root queries that are responded to by domestic instances per vantage point. Darker cells indicate that more DNS queries from the corresponding vantage points are resolved by domestic instances.
Domestic root server instances help absorb queries from recursive resolvers
We also investigated how deploying domestic instances can impact root server selection and absorb queries from recursive resolvers within their catchment area.
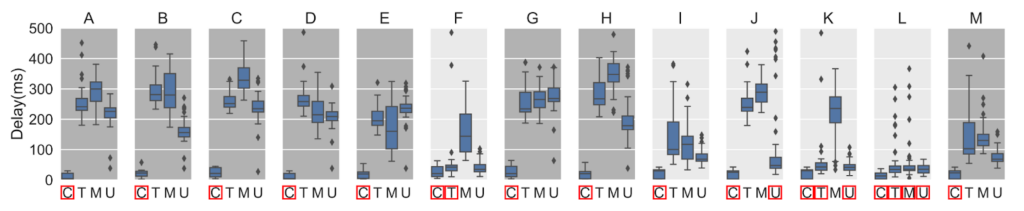
Figure 3 plots the results of the delay of our vantage points to root servers. We confirmed that domestic instances are effectively serving networks within their catchment area with lower delay.
We also reviewed the source code of four types of common recursive resolver implementations: BIND 9, Unbound, Knot Resolver, and PowerDNS Recursor. We confirmed that deploying domestic instances effectively lowers query delay, and their corresponding root servers will thus be preferred by the selection algorithms (especially in BIND and Knot Resolver).
Recommendations
Our study revealed several major ISP networks that are not served by domestic instances. We recommend:
- Networks that are not covered by the catchment area of nearby instances, if permitted in terms of political and commercial interests, should peer with the root server networks. They should also consider adopting alternative measures that improve access to the RSS (for example, running a local root copy as documented in RFC 8806).
- The DNS community needs to develop systems that measure root servers from resolvers’ perspectives.
For more details on our study, please refer to our presentation at the APAC DNS Forum 2022 (below) and paper ‘Measuring the Practical Effect of DNS Root Server Instances: A China-Wide Case Study’ in Passive and Active Measurement Conference 2022 (PAM).
Fenglu Zhang is a PhD student at Tsinghua University. His research interests include Internet measurement and network security.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.