
JPCERT/CC observes how DNS-abuse incidents occur and develop daily. Like other CERTs we share trends and characteristics of these incidents with the local and wider security community to help security service providers improve their services and DNS service providers to take necessary measures in the future.
In April, I participated in the panel session ‘Real Life Perspectives on Regional DNS Abuse in APAC’ at the APAC DNS Forum 2022, during which I and my fellow panellists shared examples of DNS incidents that we’ve seen in the Asia Pacific region and how we, as a community, can improve how we mitigate these threats.
Phishing and domain hijacks
Security incidents caused by DNS attacks are often difficult to investigate and respond to because they are hardly detectable from external observation. As a coordination centre, we try to gain an overall understanding of the situation based on historical data and various information from the affected organization as well as partner organizations. The details of the attacks obtained from such investigations are used to prevent recurrence in the future.
Two DNS-related incidents that we see a lot in Japan are phishing sites and domain hijackings.
JPCERT/CC received 44,242 incident reports in 2021 more than half of which were related to phishing sites. One recent incident, that I presented during the panel session, involved an attacker targeting a hosting service provider (Figure 1).
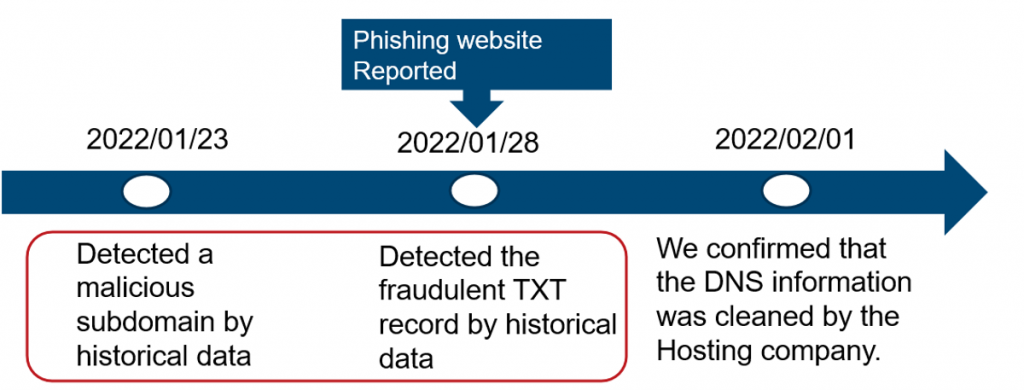
In this incident, the attacker altered the DNS information of a user, registered a fraudulent subdomain, and ran a phishing site on the target host together with some traces of a malicious TXT record (Figure 2) registration to add SPF information.
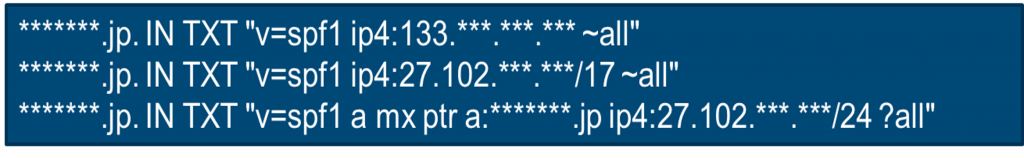
We assumed that the attackers added the SPF record to prevent the malicious email from being detected.
Another case study I presented on was of a domain hijack targeting a cryptocurrency business in Japan.
Based on passive DNS information, my colleagues and I at JPCERT/CC analysed how attackers introduced traces of an attempt to steal information by overwriting the name server (NS) information of a business and altering the route to an NS under the control of the actor (Figure 3).
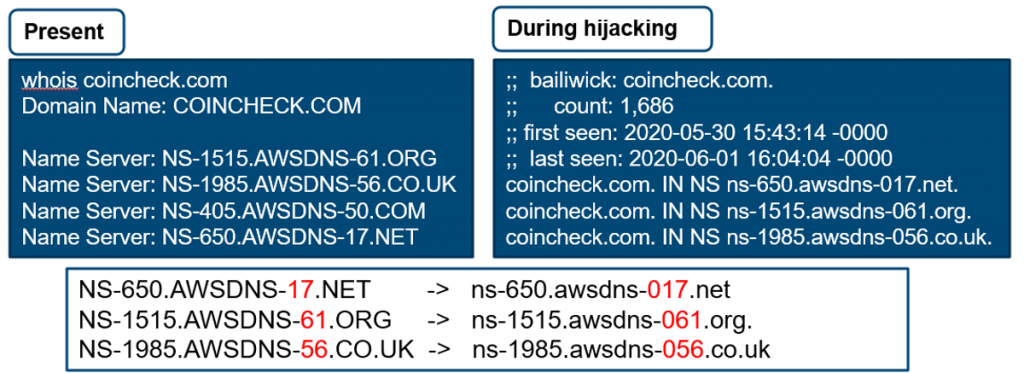
From our investigation, we could see the existence of a malicious mail exchange (MX) server (Figure 4). We assumed that the actor sent a phishing email to impersonate the staff in question and received a response though we are unsure of the reason for the attack.

Be proactive when it comes to securing the DNS
There are numerous ways that DNS operators can be proactive when it comes to securing their DNS against attacks.
The panellists agreed that registry lock is one of the best and easiest security precautions you can implement to protect your domain name. It allows you to lock the data associated with your domain names and add extra levels of authentication between the registry and registrar when making changes.
We also discussed the effectiveness of domain authentication technologies in conjunction with DNSSEC for detecting phishing emails and the like in place of email security protocols such as SPF, DKIM and DMARC, which are difficult to configure.
Read: Adoption of DNS security mechanisms related to ease-of-use, cost
Sharing experiences helps everyone
I hope to continue contributing to the good of the domain space by sharing our observations and trends on DNS abuse with DNS operators and related stakeholders.
Thanks to my fellow panellists Carlos Alvarez (ICANN) and Carel Bitter (The Spamhaus Project).
Shoko Nakai is an information security analyst and incident coordinator at JPCERT/CC.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.
