
Distributed Denial of Service (DDoS) attacks pose a major and omnipresent threat to the stability of the Internet. On average, about one-third of the active /24 networks on the Internet receive some form of DDoS attack every two years.
Reflective amplification attacks are a simple and cost-effective (and therefore popular) means of performing DDoS attacks. Traditionally, these types of attacks have been observed using honeypots, which mimic a vulnerable service and log all activity. However, honeypots cannot infer the extent to which other infrastructures are involved (other amplifiers) and are therefore limited in the assessment of general attack properties such as intensity.
To breach this gap, my colleagues and I at Freie Universität Berlin, University of Twente, and HAW Hamburg, developed a passive method to infer DNS amplification attacks in sampled IXP flow data. At the IXP, we had to overcome the challenge of distinguishing between legitimate and attack traffic. But in contrast to honeypots, the IXP enables an in-network view of how the complete amplification ecosystem is misused and how good attackers are at amplifying.
Surprisingly, with an overlap of only ∼4%, IXPs and honeypots detect mostly disjointed sets of attacks. We found 24k new attacks in three months that were not observed by the honeypots.
Below are some more key insights and recommendations on how to protect against the shortcomings of the DNS when it comes to its abuse for such attacks.
Attackers are really good at selecting large zones
First, we investigated whether attackers inquire names for maximizing amplification, or whether there is an unused threat potential.
Using OpenINTEL data, we estimated the response sizes of ANY queries of 440 million domain names (Figure 1). We calculated the response sizes based on the cumulative resource record sizes stored in the DNS and ignored common software or protocol limits (4,096 bytes for EDNS and 65,536 bytes for UDP).
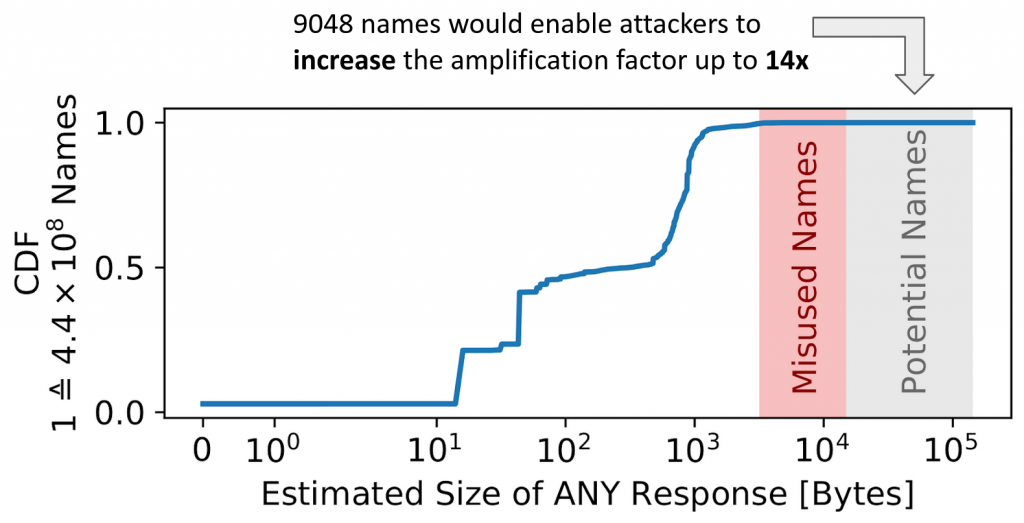
Misused names (highlighted in red) are domain names that were used in attacks detected at the IXP. Overall, only 9,048 domains show a higher amplification factor than the highest-ranked, misused name — about 0.002% of all names (grey area). This suggests that attackers attempt to cherry-pick names for high amplification factors without selecting the best options.
Recommendation: If possible, limit your zone size!
ANY queries are still effective
By analysing the packet sizes in the sampled IXP data, we could confirm that attacks achieve effective amplification factors. Figure 2 shows the relative frequency of the actual response sizes observed at the IXP, grouped by each name.
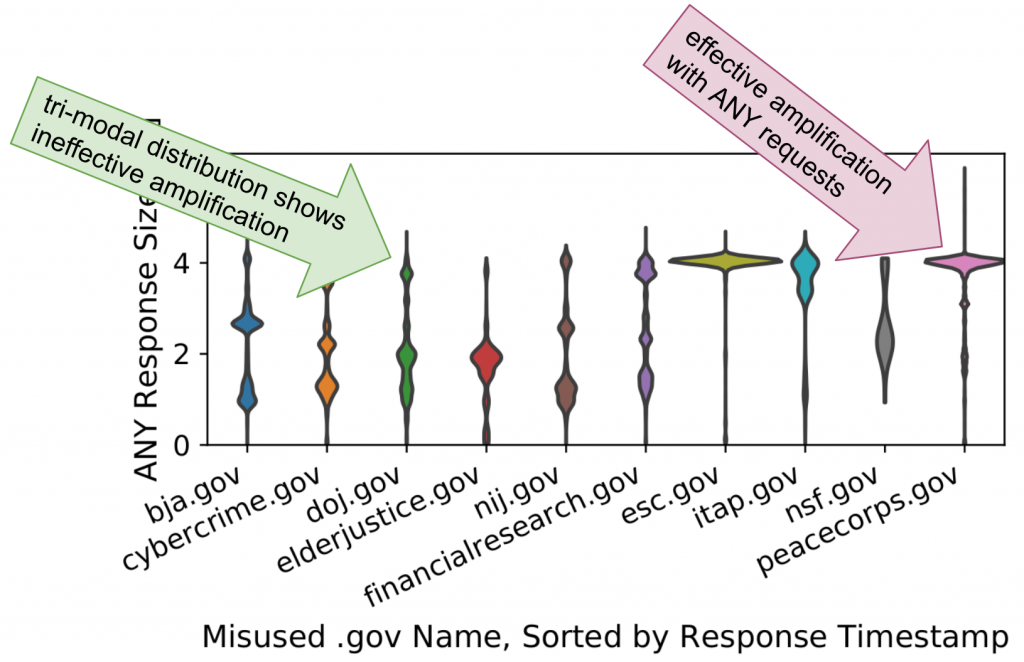
We considered all DNS query types. However, we only observed type ANY for these names during attacks. Most names exhibit a bi- or tri-modal distribution.
The observed clusters of response sizes near the theoretical limit (all resource records from a zone, around 4KB) highlight that the attacker succeeds in finding names (and related authoritative nameservers) as well as amplifiers that still allow ANY requests.
Furthermore, closer investigation reveals that smaller response sizes appear rather at the end of a name’s life cycle. This indicates that attackers observe the current effective amplification factor and update misused names upon a decline.
Recommendation: Refuse ANY queries (or force TCP failover)!
Bad DNSSEC key rollovers make your zone attractive for misuse
The dashed line in Figure 3 indicates the recommended maximum payload size (4,096 bytes) of EDNS. We observed that the expected response sizes change while names are actively misused in attacks and also that transitions to other names follow drops in sizes.
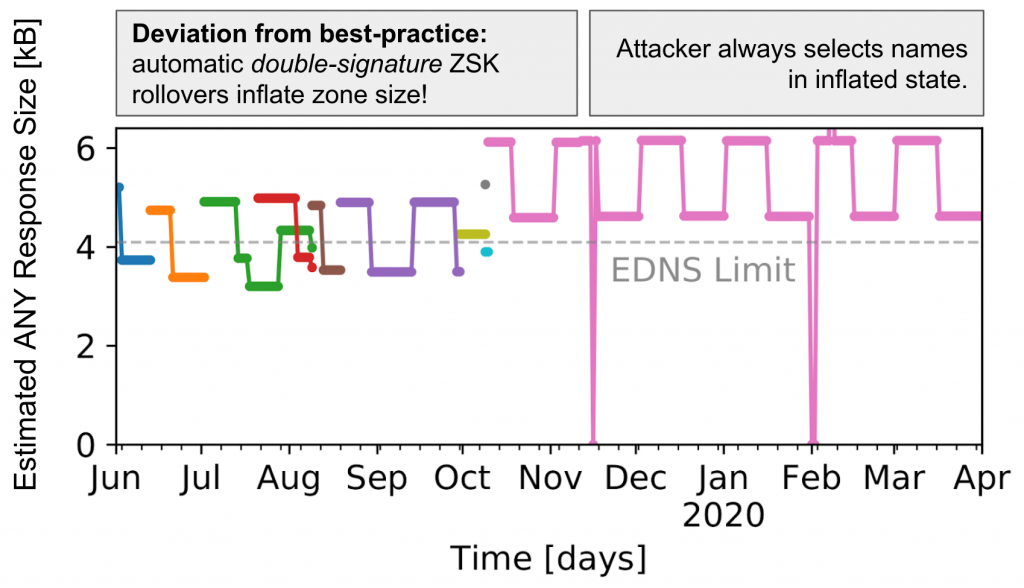
The plateaus in response sizes — which last two weeks — relate to DNSSEC key rollovers. When a new zone signing key (ZSK) is introduced, an increase in response size can be expected, as multiple DNSKEY records are present at the same time. ZSK rollovers can be completely automated in software, which explains the regular patterns. RFC 6781 recommends two rollover schemes: Pre-publish and double-signature (Figure 4). Although both rollover schemes are proposed, pre-publish has been established as a de facto standard (it is used 8x more often in 2020 and is recommended by various DNS software vendors).
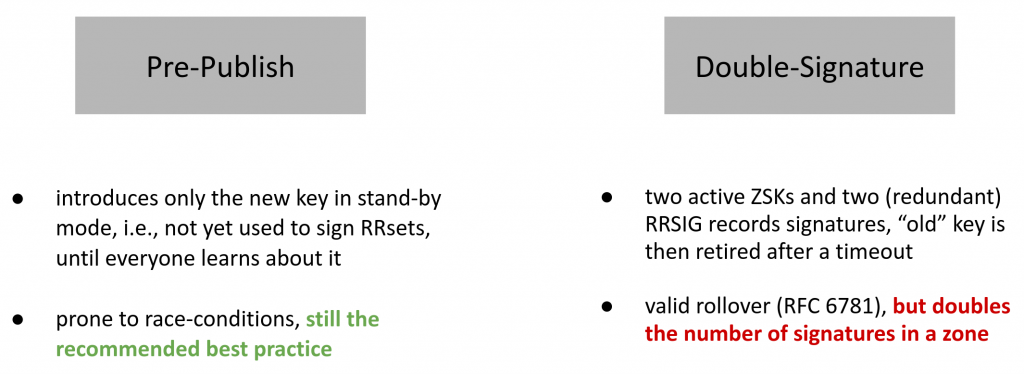
Pre-publish introduces only the new key in standby mode, that is, the key is not yet used to sign RRsets. This allows resolvers to learn about the new key before it is actively used.
Double-signature allows two active ZSKs and generates two (redundant) RRSIG records signatures. The old ZSK can then be retired at any given time. On the downside, this scheme doubles the number of signatures in a zone, which attracts misuse.
At the IXP, we only observe double-signature schemes for the misused .gov names.
Recommendation: Rollover with pre-publish!
Please refer to our paper for more details.
Marcin Nawrocki is is a PhD student and research assistant at Freie Universität Berlin.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.
