
As providers increasingly deploy IPv6 to the edge, often unbeknown to end users, the importance of understanding their deployment strategies and implementation peculiarities grows.
Recently, my colleagues and I from CMAND, the Naval Postgraduate School and CAIDA, investigated large-scale residential deployments of consumer-grade routers and examined a phenomenon in which some IPv6 access providers regularly and periodically cycle prefixes allocated to their customers. We can characterize this phenomenon as ‘prefix rotation’, due to the widespread use of a legacy IPv6 addressing mode (EUI-64) among certain providers and device manufacturers.
Our IMC paper, Follow the Scent: Defeating IPv6 Prefix Rotation Privacy, builds on previous research aimed at discovering the IPv6 ‘periphery’, that is, the Customer Premises Equipment (CPE) routers typically found in residential and small business deployments.
In Discovering The IPv6 Network Periphery (PAM 2020), we developed and deployed an IPv6 periphery discovery algorithm that enables researchers to elicit responses from CPE devices using yarrp.
These responses illuminate both deployment decisions that access providers make in extending IPv6 service to their customers, as well as insights into consumer-grade router networking software.
Read: Measuring the IPv6 network periphery
For instance, our experiments found that millions of IPv6 CPE routers continue to use Global Unicast Addresses (GUAs) with an Interface Identifier (IID) formed using the interface’s Extended Unique Identifier-64 (EUI-64).
EUI-64 GUAs have long been considered a privacy and security risk, as they are formed using the interface’s 48-bit Media Access Control (MAC) address, modified by inverting the Universal/Local (U/L) bit and inserting a static ‘0xfffe’ in-between the third and fourth bytes to form a 64-bit identifier. Using globally-routable IPv6 addresses that contain the device’s MAC address allows remote adversaries to fingerprint devices and track them across address changes, potentially enabling targeted attacks and losing the privacy benefits offered by randomly-generated IPv6 IIDs.
In our most recent study, we leveraged EUI-64 IPv6 addresses to characterize several aspects of IPv6 access ISP deployments. First, we used the three upper bytes of the MAC addresses (the Organizationally Unique Identifier or OUI) embedded in EUI-64 IPv6 addresses to determine CPE device manufacturer diversity. We found that CPE manufacturers are highly homogeneous within an Autonomous System (AS); this is possibly due to ISPs partnering with device manufacturers to provide a standard CPE device for their residential customers.
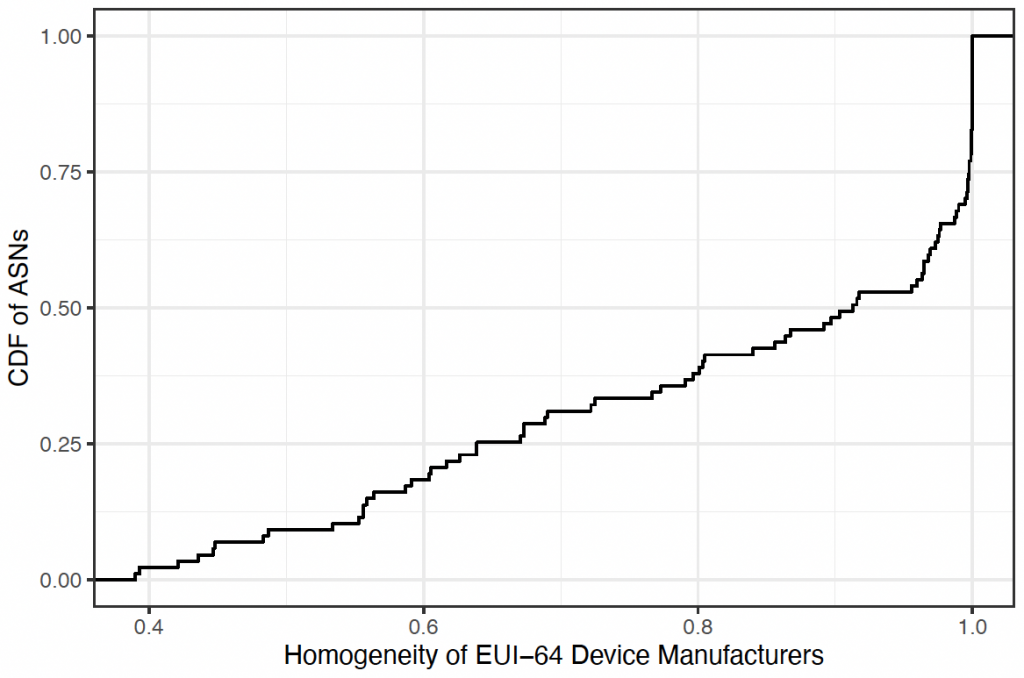
More than half of the ASes have a homogeneity of at least 0.9 (Figure 1), indicating that manufacturer homogeneity is particularly pronounced. For example, in NetCologne (AS8422), 99.8% of the MAC addresses we discovered embedded in EUI-64 IPv6 addresses come from AVM GmbH MAC address allocations. AVM GmbH manufactures the Fritz!Box line of home routers, which are common in Europe. In contrast, 99.6% of MAC addresses embedded in Viettel Group (AS7552) EUI-64 IPv6 addresses that we discovered are from ZTE MAC address space.
While conducting large-scale measurements in previous work, we stumbled across many residential providers that ‘cycle’ network prefixes allocated to their customers with high frequency, typically on the order of 24 hours. Due to the use of EUI-64 GUAs by CPE devices in some of these networks, we can track the rotation of allocated prefixes to these devices over time. We do this by matching the same EUI-64 IID to the varied /64 networks we observe it occurring over time as we periodically probe the address space of prefix-rotating service providers.
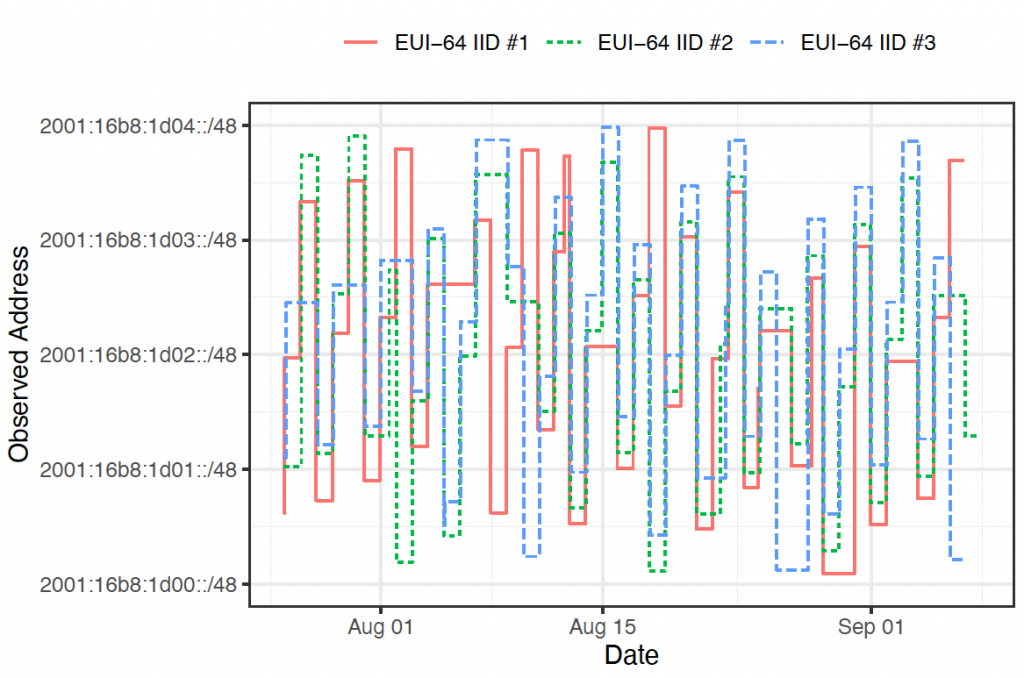
As per Figure 2, all three IIDs are observed in a new /64 network daily, indicating that the provider (in this case, Versatel 1&1, a German residential provider) frequently rotates its customer-allocated prefixes. Each EUI-64 IID’s network prefix increments by one /48 each day, until it lands in the 2001:16b8:1d04::/48, at which point the prefix ‘wraps around’ back to the 2001:16b8:1d00::/48. In other words, the 2001:16b8:1d00::/46 ‘rotation pool’ constrains the prefix rotation of devices that were allocated subnets from it.
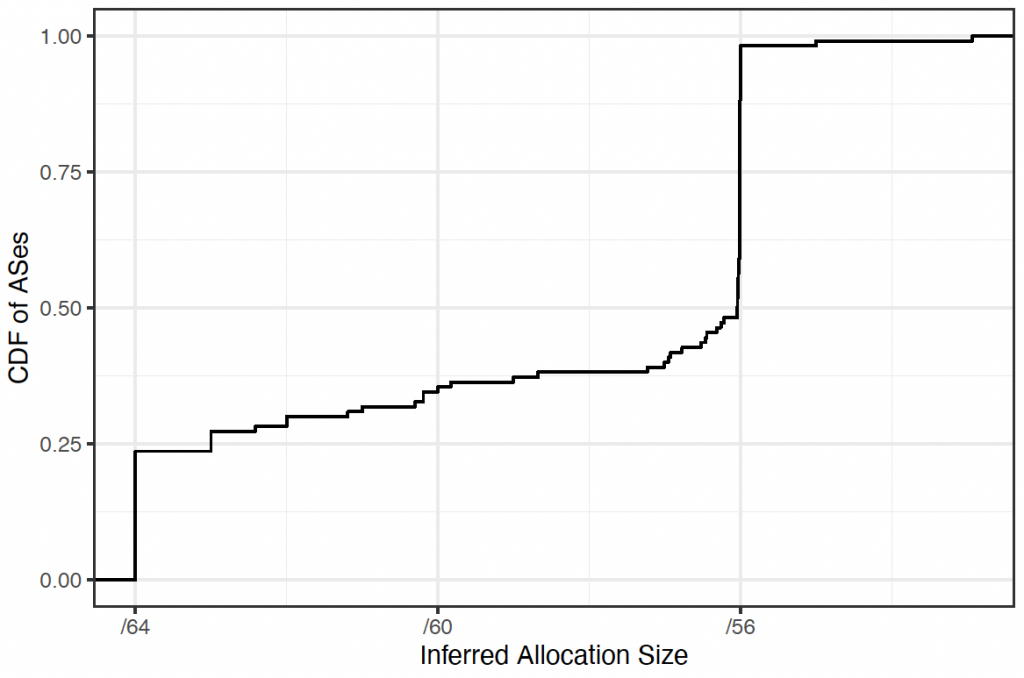
Finally, we continued previous work aimed at inferring the prefix sizes that IPv6 providers allocate to customers. We were able to infer allocated prefix sizes in residential networks by grouping probe target addresses by response address. The range of target networks that elicit the same response address from a CPE device indicates how large a customer subnet is.
As per Figure 3, our IMC results showed that:
- Approximately half of the ASes we studied allocated /56s to their customers, while about a quarter allocated /64s.
- Approximately 25% of the prefix inferences lie between /64 and /56; we found some ASes that allocate /60s to customers, while others allocate multiple sizes, leading to a median allocation size of about /60.
Note that we considered only prefixes subnetted below /48 in our study to reduce the amount of probing required.
We invite curious readers to read the full-length IMC paper, Follow the Scent: Defeating IPv6 Prefix Rotation Privacy.
Erik Rye is a student at the University of Maryland. His interests include network measurement and security and privacy topics.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.
