
DNS is important in nearly all interactions on the Internet but DNS is easy to spoof; third parties intercept and respond to queries for benign or malicious purposes. As nearly all large DNS providers use IP anycast to provide service from many physical locations, spoofing can often look like ‘just another site’.
Although spoofing has been around for a long time, there has been no longitudinal study of how it is changing over time. Prior studies of DNS spoofing explored how it works, particularly the use of spoofing for censorship. While DNSSEC protects the integrity of DNS answers (when it is used), there is increasing interest in DNS privacy, prompting our study of spoofing.
To provide a better understanding of DNS spoofing trends, John Heidemann and I from the University of Southern California / Information Sciences Institute, analyzed six years and four months of the 13 DNS root ‘letters’ as observed from RIPE Atlas’s 10k observers around the globe, and augmented it with one week of server-side data from B-Root to verify our results.
Our work and validation shows three important results:
- DNS spoofing has been increasing (the fraction doubled over six years) and is occurring worldwide
- Most identifiable spoofers are ISPs and network providers
- Our validation with B-root shows nowadays most spoofing directly drops the original queries instead of using injection — injecting a reply faster than the authoritative servers.
Our full work is available here [PDF].
How did we discover spoofing replies?
We probed from controlled vantage points (VPs) that can initiate three kinds of queries: DNS (hostname.bind), ping, and traceroute. We use RIPE Atlas probes as our VPs and target all 13 DNS root letters from A-root to M-root.
Overt spoofers: ‘nnn1-lax2’ vs. ‘lego’
We detected tentative legitimate replies when the answer contains server IDs that follow the operator-specific pattern. Often such patterns indicate the location, a server number, and the root letter. Historically, A-root operators had a naming convention where the Server ID starts with nnn1- and is then followed with three letters representing a site/city and ending with a number, with examples like nnn1-lax2 and nnn1-lon3. Other root letters follow similar patterns. By contrast, spoofers use other types of names, often with their own identities.
Spoofing examples include: lego, chic-cns13.nlb.mdw1.comcast.net, 2kom.ru.
This test only conditionally detects legitimate replies, since a covert spoofer could intentionally reply following the pattern. We used traceroute and ping to verify our initial results.
Covert delayers
For those answers with the valid-looking server IDs, we also looked to see if these DNS queries were processed through a third-party, bringing delays to the original answers.
To learn more about the goals of the spoofers, we took some manual steps to learn the identities of the spoofers. We manually checked the websites of the third-party spoofers, according to their server IDs, to learn about their identities and what they do.
DNS spoofing keeps increasing
How much?
From 2014 right up until today, the fraction of VPs seeing spoofing increased. In Figure 1, we see from 2014 to 2020, the fraction of VPs that experienced DNS spoofing more than doubled from 0.007 (2014-02) to 0.017 (2020-05).
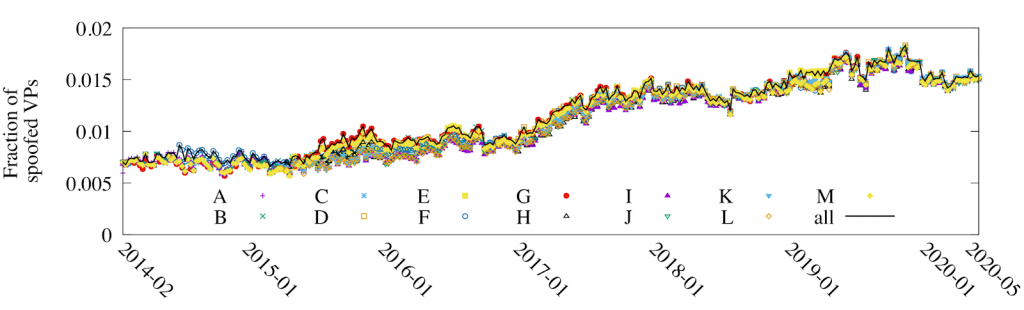
Where?
DNS spoofing happens worldwide, although more often in some areas than others. Figure 2 shows the fraction of VPs that saw spoofing per area in 2019.
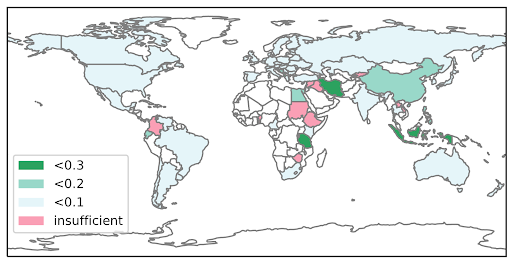
Who?
We attempted to identify and categorize spoofers by looking at their server IDs. We can see most of the identifiable spoofers are ISPs or network providers in Table 1.
| Types | Example URLs | Number of spoofers |
| ISPs | skbroadband.com2kom.ru | 32 (16.16%) |
| network providers | softlayer.comlevel3.com | 24 (12.12%) |
| education-purpose | eenet.ee | 1 (0.5%) |
| DNS tools | dnscrypt.eu | 1 (0.5%) |
| VPNs | nordvpn.com | 1 (0.5%) |
| hardware | eero.com | 1 (0.5%) |
| personal | yochiwo.org | 1 (0.5%) |
| unidentifiable | DNS13DNS-Expire | 137 (69.19%) |
Table 1 — Classification of spoofers
Validation and spoofing mechanisms
We validate the spoofing detection of B-root whether the query has an answer from the authoritative B-root server or not. Queries that are not received by servers are definitely spoofed. Our spoofing detection shows a true positive rate over 0.98 in Table 2.
Read: Why don’t we have DNS-security policy for context-full threat protection?
Nowadays, most spoofing attempts are processed by a proxy instead of by injection. Server-side data also allows us to distinguish DNS proxies from DNS injection. DNS injection will respond quickly to the query while letting it pass through to the authoritative server (on-path processing), while a DNS proxy will intercept the query without passing it along (in-path processing). Table 2 shows 139 out of 142 (98%) of VPs detected as spoofed never reached B-root, suggesting a DNS proxy instead of injection.
| Sent | Received | True positive rate | |
| Active VPs | 8981 | 8449 | – |
| timeout | 241 | 47 | ≥ 0.81 |
| spoofed | 142 | 3 | ≥ 0.98 |
| not spoofed | 8598 | 8399 | – |
Table 2 — the number of queries that reached B-root based on spoofing detection, for sample hour 2019-01-10T03:52:49Z
Conclusions
We have shown that DNS spoofing is global and increasing, and provide a detection methodology that has a high positive rate. We have also shown that proxies are a more common method of spoofing today than DNS injection.
We can draw two recommendations from this work:
- Based on the growth of spoofing, we recommend that operators regularly look for DNS spoofing
- Interested end-users and operators may wish to watch for spoofing, using our approach
Lan Wei is a computer science PhD from the University of Southern California / Information Sciences Institute.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.
