In the context of third-party tracking, various in-browser privacy protection techniques (such as browser extensions) have been designed to protect end-users.
Due to the increasing use of extensions that block third-party tracking, tracking providers introduced a new technique called Canonical Name (CNAME) cloaking. It misleads web browsers into believing that a request for a subdomain of the visited website originates from this particular website, while this subdomain uses a CNAME to resolve to a tracking-related third-party domain. This technique thus circumvents third-party targeting privacy protections.
In our recent research paper, we at The Graduate University for Advanced Studies (Sokendai) in collaboration with the French National Cybersecurity Agency (ANSSI), sought to address this issue and characterize CNAME cloaking-based tracking for the Alexa top 300K websites.
What is CNAME cloaking-based tracking?
A CNAME record is a type of Domain Name System (DNS) record that maps an alias name to a true or canonical domain name. Using CNAME records has become an emerging technique in web tracking to hide usual tracking domains that are blocked by browser filter lists and extensions.
Tracking providers ask their clients to delegate a subdomain for data collection and link it to an external domain using a CNAME record.
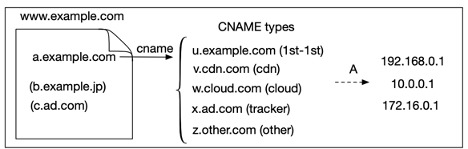
We define CNAME cloaking-based tracking as using CNAME records to disguise requests to a third-party tracker as first-party ones (see Figure 1). For example, when end users access the example.com website, it actually embeds a first-party subdomain named a.example.com, which points to a tracking provider, ad.com via the CNAME x.ad.com. The tracking provider ad.com thus tracks activities of end users on the website, example.com.
How to detect CNAME cloaking-based tracking?
To characterize CNAME cloaking-based tracking, we used OpenWPM to conduct large-scale automatic crawls on the Alexa Top 300K websites in January 2020. We then resolved each CNAME answer set by the DNS for each subdomain for these target sites.
To detect CNAME cloaking-based tracking, we applied wildcard matching based on well-known tracking filter lists — Easy privacy list and AdGuard tracking protection filter — on a subdomain on the Alexa Top 300K websites. Then we built regular expressions from tracking domains to match with CNAME records behind all subdomains. Finally, we inspected individual CNAME nodes in all CNAME chains (a series of CNAMEs from the initial first-party subdomain to all CNAME nodes before the resolution to an IP address) using this customized filter list. If any node in a CNAME chain was flagged by this list, we classified this CNAME chain as tracking-related.
Overall, we detected 1,762 websites that contained CNAME cloaking-based tracking, which belong to 56 tracking providers.
Websites using CNAME cloaking-based tracking
We then looked at the category and geographic location of websites containing CNAME cloaking-based tracking. For the 1,762 websites containing CNAME cloaking-based tracking, websites in Finance, Personal Vehicles, and Travel categories use CNAME cloaking-based tracking more than other categories. Meanwhile, Ireland and Belgium host the most websites using CNAME cloaking-based tracking in the Alexa Top 300K websites.
Tracking providers using CNAME cloaking-based tracking
For tracking providers behind CNAME cloaking-based tracking, the major player in the Alexa Top 300K websites is Adobe (61%). Besides Adobe, we see some well-known tracking providers, such as Act-on, Eulerian, and Intent Media.
Interestingly, we observed some specific co-occurrence between providers and categories: Act-on for Business, Eulerian for Shopping, Intent Media for Travel, and Oracle for Information Technology. Meanwhile, tracking providers cooperating with websites such as Adobe, Act-on, and Oracle are mainly located in the United States.
We also observed that some tracking providers are mainly observed in specific economies, for example, Eulerian in France and Intent Media in Germany. Again, Adobe is the most popular tracking provider in almost all economies, except France (Eulerian is first with 42.1%).
Measuring the effectiveness of protection techniques against CNAME cloaking
There are several available privacy protection methods. Some browsers provide specific features and some browser extensions also use several techniques (such as blacklisting, or traffic monitoring) to block third-party tracking.
We investigate five major browsers and six popular privacy-protecting extensions that support these browsers by crawling the 1,762 websites containing CNAME cloaking-based tracking that we detected before.
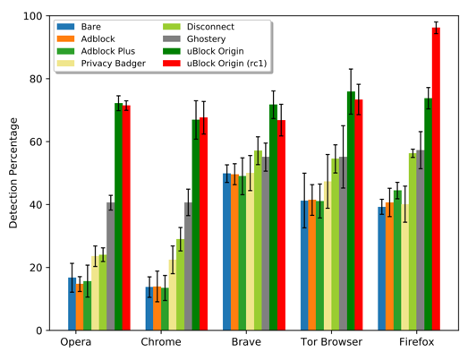
Figure 2 shows the detection percentage of the CNAME cloaking-based tracking among browsers and their extensions.
Brave shows the best performance among five browsers without any extension and blocks CNAME cloaking-based tracking on around 50% of websites. We speculate that the Shields feature is effective at detecting CNAME cloaking-based tracking. We also manually confirm that Shields blocks some CNAME cloaking-related subdomains, such as smetrics.10daily.com.au (Adobe), f7ds.liberation.fr (Eulerian), and 5ijo.01net.com (Eulerian).
For all browsers, the most effective extension is uBlock Origin — it blocks CNAME cloaking-based tracking on around 70% of websites. Adblock and Adblock Plus provide insufficient protection abilities for all browsers. This result is not surprising because these extensions target ad-blocking. Another notable point is that uBlock Origin version 1.24.5rc1 with anti-CNAME cloaking-based tracking technique outperforms uBlock Origin version 1.24.4. It, however, is only available on Firefox because other browsers do not provide an API that allows an extension to perform DNS lookups (see uBlock Origin issue #780).
We also reported on a slight increase in the number of sites containing CNAME cloaking-based tracking from 2016 to 2020. This proves that CNAME cloaking is not a new phenomenon — it has been deployed for at least four years.
To the best of our knowledge, this is the first in-depth analysis of CNAME cloaking-based tracking. If you are interested in the details of our work, please read our paper and watch a recording of our presentation at TMA 2020.
Ha Dao is a PhD student at The Graduate University for Advanced Studies (Sokendai), Japan.
Discuss on Hacker NewsThe views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.

Hi,
thank you for your research. Brave since version 1.17 released on November 2020 https://brave.com/privacy-updates-6/ integrates a countermeasure against CNAME Cloaking.
“In version 1.25.0, uBlock Origin gained the ability to detect and block CNAME-cloaked requests using Mozilla’s terrific browser.dns API. However, this solution only works in Firefox, as Chromium does not provide the browser.dns API. To some extent, these requests can be blocked using custom DNS servers. However, no browsers have shipped with CNAME-based adblocking protection capabilities available and on by default.”
It would be good to update the article accordingly.
Best Regards
Interesting read on CNAME cloaking. Since many trackers bypass traditional filters, tools like uBlock Origin work best. On macOS, pairing it with a good ad blocker for mac
adds another layer of privacy.